Cyber Security
News
FraudOnTok Malware Campaign Targets TikTok Shop Users Through Fake Apps and Phishing Tactics
Mitchell Langley
August 5, 2025
CTM360 exposes the FraudOnTok campaign targeting TikTok Shop users through fake apps and phishing, using SparkKitty spyware to steal crypto wallet data and drain funds. ...
News
Ransomware Gangs Exploit Microsoft SharePoint Flaws in Widespread Attack Campaign
Mitchell Langley
August 5, 2025
Ransomware groups are exploiting Microsoft SharePoint flaws in a global attack campaign, affecting over 148 organizations and linking to Chinese state-backed threat actors.
News
348,000 Patients Impacted in Mt. Baker Imaging Data Breach
Andrew Doyle
August 5, 2025
A cyberattack on Mt. Baker Imaging exposed sensitive data for 348,000 Washington patients, including medical and financial records, triggering a class action lawsuit.
News
Attackers Abuse Link-Wrapping Services to Steal Microsoft 365 Credentials
Mitchell Langley
August 5, 2025
Attackers hijack Proofpoint and Intermedia link-wrapping to hide Microsoft 365 phishing pages, using compromised protected accounts to harvest login credentials.
News
Akira Ransomware Surges on SonicWall Devices Using Zero-Day and Credential Abuse
Andrew Doyle
August 5, 2025
A sharp uptick in Akira ransomware activity is exploiting SonicWall remote access infrastructure, potentially via an unpatched zero-day. Akira Ransomware ...
News
Everest Ransomware Group Claims Mailchimp but Experts Say Leak Is Minor and Unproven
Mitchell Langley
August 5, 2025
Everest claims Mailchimp data breach, citing a small internal dataset; security insiders and Intuit report no evidence of systemic compromise.
Resources
DragonForce Ransomware – Hacktivist Turned Cybercriminal Enterprise
Andrew Doyle
August 4, 2025
DragonForce is a ransomware and data extortion group that evolved from a pro-Palestinian hacktivist collective into a financially motivated cybercriminal enterprise.
News
Hackers Target Python Developers With Phishing Campaign Using Fake PyPI Site
Andrew Doyle
August 3, 2025
A phishing attack is targeting Python developers with fake PyPI login prompts to steal credentials and potentially distribute malware via compromised Python packages.
Blog
Mastering the Metasploit Framework: The Ultimate Guide to Exploits, Payloads, and Ethical Hacking
Mitchell Langley
August 1, 2025
Explore the full potential of the Metasploit Framework for ethical hacking, penetration testing, and CVE exploitation with this complete, real-world guide for cybersecurity professionals.
Blog
Shadow IT in the Enterprise: Risks You Didn’t Know You Had
Gabby Lee
July 31, 2025
Unmanaged SaaS and shadow IT applications silently open dangerous security gaps. Discover how enterprise teams can detect, control, and protect against these invisible but growing ...
News
Minnesota Deploys National Guard Cyber Unit Following Major Cyberattack on St. Paul City Systems
Andrew Doyle
July 31, 2025
Minnesota activates the National Guard’s cyber unit after a cyberattack cripples St. Paul’s municipal systems, prompting emergency declarations and a multi-agency response.
News
Tea App Disables Messaging After Second Breach Exposes Over One Million Private Conversations
Andrew Doyle
July 31, 2025
Tea app disables messaging after two breaches: 72,000 verification images leaked, then 1.1 million private messages exposed; FBI and security firms investigating.
News
ShinyHunters Behind Salesforce-Related Data Breaches at Qantas, Allianz Life, LVMH
Mitchell Langley
July 31, 2025
ShinyHunters targets Salesforce users at Qantas, Allianz, and LVMH in voice phishing attacks to steal customer data and conduct private extortion campaigns.
News
RiteCheck Confirms Data Breach Affecting Nearly 70,000 Customers and Employees
Andrew Doyle
July 31, 2025
RiteCheck has disclosed a 2023 data breach impacting nearly 70,000 people, exposing Social Security numbers, payment card data, and IDs after an 11-month delay.
News
Hackers Exploit SAP NetWeaver Flaw to Deploy Advanced Auto-Color Malware on U.S. Chemical Firm
Mitchell Langley
July 30, 2025
Hackers exploited a critical SAP NetWeaver vulnerability to deploy Auto-Color malware on a U.S. chemicals firm, using advanced stealth and sandbox evasion techniques.
News
Aeroflot Flights Canceled After Hacktivist Cyberattack Cripples Airline Systems
Mitchell Langley
July 30, 2025
Aeroflot’s operations were disrupted after a cyberattack claimed by Ukrainian and Belarusian hacktivists who allege wiping critical systems and exfiltrating sensitive airline data.
News
Orange Discloses Cyberattack, Service Disruptions in France Following Breach
Mitchell Langley
July 30, 2025
French telecom giant Orange confirmed a cyberattack that disrupted services in France. The affected system was isolated; no data exfiltration has been found yet.
News
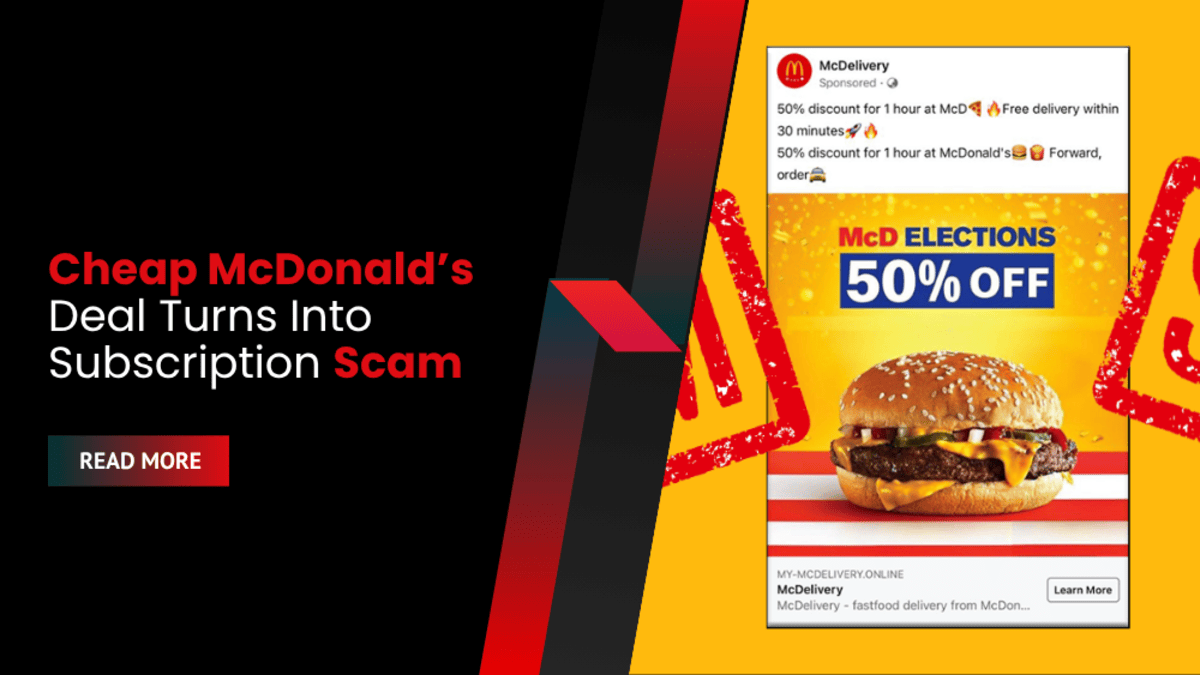
Cheap McDonald’s Deal Turns Into Subscription Scam: Over 10,000 Romanians Targeted via Facebook and Instagram Ads
Andrew Doyle
July 30, 2025
A $2 McDonald's deal scam has duped over 10,000 Romanians into €63.42 bi-weekly subscriptions via fake ads on Instagram and Facebook, Bitdefender reports.
Cybersecurity
Scattered Spider Ransomware Group Ramps Up Sophisticated Attacks Targeting Enterprises Globally
Gabby Lee
July 30, 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the FBI and international partners, has issued an updated advisory ...
Resources
Lynx Ransomware: INC Ransomware Reincarnated
Gabby Lee
July 29, 2025
The Lynx ransomware group is a financially motivated threat actor operating under a Ransomware-as-a-Service (RaaS) model. Emerging as a successor to the INC ransomware group ...
CVE Vulnerability Alerts
SolarWinds Vulnerability Exploitation Prompts Immediate Response from Federal Agencies
Andrew Doyle
February 4, 2026
Cybersecurity
UK Data Protection Authority Probes X’s Grok AI for Generating Inappropriate Images
Mitchell Langley
February 4, 2026
News
Everest Extortion Group and Iron Mountain Data Incident: Key Insights
Mitchell Langley
February 4, 2026
TOP CYBERSECURITY HEADLINES
Application Security
The DockerDash Vulnerability: Understanding Its Impact on Docker Desktop and CLI
This Week’s Security Spotlight
Cybersecurity
Revelations from Epstein Files: Allegations of a “Personal Hacker”
Andrew Doyle
February 4, 2026
Cybersecurity
Nike Investigates Breach as Hackers Threaten Data Disclosure
Andrew Doyle
January 28, 2026
Application Security
Microsoft Investigates Outlook Crashing on iPad Devices due to Coding Error
Andrew Doyle
January 28, 2026
Network Security
TP-Link’s Vulnerability: Critical Patch for VIGI Cameras
Gabby Lee
January 20, 2026
Trending
Daily Briefing Newsletter
Subscribe to the Daily Security Review Email Briefing to stay informed on the latest threats, trends, and technology, along with insightful columns from industry experts.
Featured Videos
Podcasts
Cyber Security News

- All
- Application Security
- Blog
- CVE Vulnerability Alerts
- Cybersecurity
- Cybersecurity Newsletter
- Data Security
- Endpoint Security
- Identity and Access Management
- Information Security
- Network Security
- News
- Phishing
- Podcasts
- Product Reviews
- Ransomware
- Ransomware Victims
- Resources
- Security Spotlight
- Sponsored
- Threat Actors
- Threat Actors
- Threat Detection Tools
FraudGPT, WormGPT, and Dark AI Models Fuel Surge in Cybercrime
August 26, 2025
Malicious AI models like FraudGPT, WormGPT, and PoisonGPT are reshaping cybercrime, enabling scalable phishing, malware generation, and disinformation. Unlike mainstream LLMs, these blackhat tools strip ...
The Imperative for a New Cyber Defense Playbook
August 26, 2025
Traditional cybersecurity models are failing against AI-driven threats, workforce fatigue, and complex tool sprawl. From adaptive malware and deepfake phishing to poorly governed machine identities, ...
UpCrypter Phishing Campaign Exploits Fake Emails to Deliver RAT Payloads
August 26, 2025
A new phishing campaign is distributing the UpCrypter malware loader through fake voicemail and purchase order emails. Targeting industries worldwide, UpCrypter delivers multiple remote access ...
Senator Wyden Demands Independent Review After Federal Court Cyber Breaches
August 26, 2025
Senator Ron Wyden is urging an independent review of federal court cybersecurity after breaches exposed sealed case files. Citing outdated systems and weak defenses, he ...
Nevada State Offices Shut Down Amid Major Network Security Incident
August 26, 2025
Nevada’s state government was forced to suspend in-person services and shut down major websites after a large-scale network security incident on August 25, 2025. Early ...
Android Malware Masquerades as FSB Antivirus To Spy on Russian Business Executives
August 25, 2025
A fake FSB antivirus hides Android malware spying on Russian executives, logging keystrokes, streaming cameras, exfiltrating messenger data, and rotating providers for command and control.
Orange Suffers Data Breach Affecting 850k Customers
August 25, 2025
Orange Belgium reports a cyberattack exposing SIM details, PUK codes, names, phone numbers, and tariff plans for 850,000 customers; no financial data or passwords were ...
Gmail Breach Exposes 2.5 Billion Accounts in Social Engineering Attack
August 25, 2025
Google confirmed a massive breach exposing 2.5 billion Gmail accounts, with hacker group ShinyHunters exploiting Salesforce access through social engineering and launching large-scale phishing and ...
Michigan Health System Hack Exposes Patients’ Lab Results in Healthcare Data Breach
August 25, 2025
Aspire Rural Health Systems suffered a major healthcare data breach, exposing nearly 140,000 patients’ records — including lab results, financial data, and personal identifiers.
Ethical and Regulatory Challenges in AI-Driven Cybersecurity
August 25, 2025
As AI becomes central to cybersecurity, it is also weaponized for deepfakes, adaptive malware, and phishing. Organizations now face ethical dilemmas, regulatory fragmentation, and governance ...
AI-Powered DDoS Attacks Prompt Advanced Defense Mechanisms
August 25, 2025
AI-powered DDoS attacks are reshaping the cybersecurity landscape, replacing brute-force floods with adaptive, machine-led precision. By mimicking legitimate traffic and shifting tactics in real time, ...
Palo Alto Networks Forecasts $10.5B in 2026 Revenue on AI Cybersecurity Growth
August 25, 2025
Palo Alto Networks projects up to $10.53B in fiscal 2026 revenue, fueled by demand for AI cybersecurity tools and strategic acquisitions like CyberArk. With stronger ...
WinRAR Zero-Day Vulnerability Exploited by Multiple Threat Actors
August 25, 2025
A newly discovered zero-day in WinRAR, CVE-2025-8088, is being exploited by RomCom hackers to plant executables in Windows Startup folders via path traversal. The flaw ...
FortiOS Auth Bypass Vulnerability Allows Attackers to Gain Full Control
August 22, 2025
Fortinet has disclosed CVE-2024-26009, a high-severity authentication bypass in the FGFM protocol. The flaw lets attackers impersonate managed FortiGate devices via FortiManager, enabling full administrative ...
Decline in Cybersecurity Prevention Effectiveness Raises Concerns for CISOs
August 22, 2025
New research from Horizon3.ai, WEF, Trend Micro, and others shows a widening gap between cybersecurity strategies and real-world results. CISOs face declining prevention effectiveness, rising ...
Norway Attributes Dam Cyberattack to Russian Hackers
August 22, 2025
Norway confirmed that Russian state-sponsored hackers breached the Bremanger dam’s control systems in April 2025, releasing 1.9 million gallons of water. While no damage occurred, ...
Chrome Extension FreeVPN One Secretly Captures Screens
August 22, 2025
Security researchers found that FreeVPN.One, a Chrome extension with over 100,000 installs and a verified badge, secretly captured user screenshots, URLs, and device data. Updates ...
Critical PostgreSQL Flaws Allow Code Injection During Database Restoration
August 22, 2025
The PostgreSQL team has disclosed three critical vulnerabilities—CVE-2025-8714, CVE-2025-8715, and CVE-2025-1094—impacting backup and restore utilities. These flaws enable malicious code injection and SQL exploitation, posing ...
Internet Archive Abused to Host Stealthy Malware JScript Loaders
August 22, 2025
Attackers are abusing the Internet Archive to host obfuscated malware loaders, launching multi-stage infection chains that deliver the Remcos RAT. By exploiting trusted infrastructure, threat ...
Business Council of New York State Data Breach: Personal Health Data of 47,000 People Exposed
August 21, 2025
BCNYS reports a two-day February intrusion discovered in August exposed personal, financial, and health data for 47,329 people, prompting rolling notifications and credit monitoring for ...