A dataset reportedly containing 15.8 million PayPal credentials — including login emails and plaintext passwords — was posted on a well-known data-leak forum, where threat actors sell and trade stolen records. The post’s author says the data is fresh and was obtained in May. PayPal disputes that characterization, telling investigators the dump relates to an earlier 2022 incident and that there was no new breach.
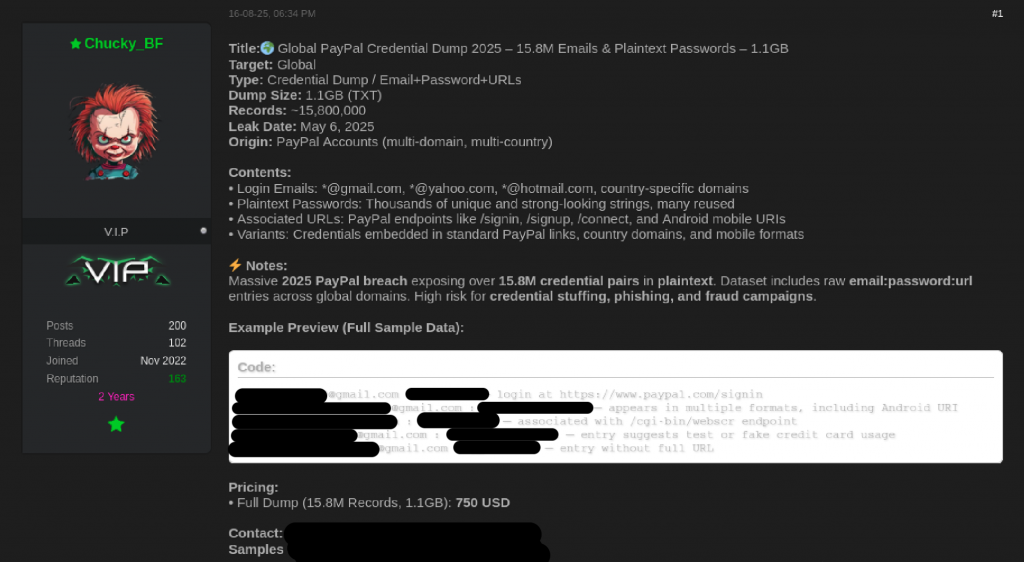
The claim reignites scrutiny of credential theft and automated account-takeover tactics. Cybernews and other researchers examined samples provided by the forum seller but could not independently verify the full dataset’s provenance or quality. The sample size was small and inconclusive, and experts noted several signals that complicate the post’s headline numbers.
What the Forum Post Claims and What the Dump Purports to Contain
According to the forum advertisement, the leak includes:
- Login email addresses
- Plaintext passwords associated with those emails
- Associated URLs and site variants for automated targeting
The seller asserts the dump is recent and global in scope. The posted sample follows a common infostealer-style format: a URL or domain followed by the username and password. That layout allows attackers to feed entries directly into credential-stuffing tools.
The forum author highlighted “thousands of unique and strong-looking” passwords in the sample but also acknowledged wide password reuse. Reused credentials reduce the effective number of usable accounts, since many entries are duplicates of people who reuse the same password across services.
PayPal’s Response and Historical Context
PayPal issued a direct denial that a new breach had occurred, characterizing the posting as tied to prior incidents. “There has been no data breach – this is related to an incident in 2022 and not new,” a PayPal representative told Cybernews.
The company’s reference points are notable. PayPal experienced a major credential-stuffing campaign in 2022 that resulted in roughly 35,000 accounts being exposed. That episode later drew regulatory scrutiny: in early 2025 PayPal agreed to a $2 million settlement with U.S. regulators over alleged failures to meet New York’s cybersecurity regulation.
PayPal also emphasized it has no evidence of a current platform compromise and reiterated that it does not view the forum post as proof of a fresh system breach. Company statements stress that cloud providers and platforms do not always know how customers handle credentials or the origin of aggregated credential sets that resurface on criminal markets.
Verification Challenges, Sample Quality, and Sale Pricing
Researchers who examined the leak faced three main verification problems:
- Small Sample Size: The subset published by the seller was too small to determine whether the full 15.8 million records are authentic or merely inflations.
- Timing Uncertainty: If the dataset were collected in May, as claimed, many of the most valuable credentials would likely have been exploited already — which weakens the seller’s pitch and raises questions about freshness.
- Price Signal: The advertised sale price for the dump was judged low relative to the claimed volume, suggesting the overall quality of the data may be poorer than advertised.
Analysts also noted the infostealer-style formatting points to a likely origin: credential harvesters installed on consumer machines that scrape login forms and send the data home. Infostealers frequently compile large, messy collections of credentials from many minor breaches and browser infections; those collections often show the exact URL-then-credentials pattern present in the PayPal post.
These factors mean the market listing may be a composite of older thefts, recycled data, or partially corrupted records rather than evidence of a single, fresh PayPal compromise.
Risks if the Data is Valid and Why Verification Matters
If any portion of the posted dataset is valid and corresponds to active PayPal accounts, exposed credentials would enable account access attempts and automated credential-stuffing campaigns against linked services. PayPal commonly offers multi-factor authentication (MFA) as an additional protection; however, knowing a valid email/password pair undermines the first authentication barrier and makes social-engineering and MFA-bypass attempts more feasible.
The inclusion of associated URLs in the dump, if correct, streamlines attackers’ tooling: it points automated bots and credential-testing scripts directly at the right endpoints and increases the scale and speed of account testing.
That said, because the sample was limited and unverifiable, security researchers cautioned against drawing definitive conclusions about scope or immediacy. The distinction between an aggregation of old, partially reused credentials and a freshly stolen, fully functional dataset is material to both users and defenders.
Possible Origins: Infostealers Versus Platform Compromise
The dump’s format and the history of large infostealer collections point toward malware-based harvesting as a plausible source. Infostealer malware commonly captures:
- Browser-stored credentials and form data
- Clipboard or form submissions during active sessions
- Passwords saved in local applications
When aggregated at scale, those harvested records are bulked into data packs sold or traded on criminal forums. That model contrasts with a single-platform breach, where an attacker compromises PayPal’s backend systems to export account records en masse. PayPal’s public denial and historical context lean observers toward the infostealer/recycled-dataset hypothesis, but firms and investigators continue to treat the claim seriously until fully validated.
What Investigators and Users Are Watching for
Independent researchers and fraud investigators are watching two things closely: whether third parties can corroborate large subsets of the claimed dataset, and whether automated credential-testing activity spikes against PayPal or the associated URLs mentioned in the dump.
Cybernews and other outlets said they could not independently confirm the authenticity of the full 15.8 million-record set. Absent broader corroboration, the forum listing remains an unverified market claim, albeit one with realistic implications if any usable credentials are present.









