EncryptHub Breach: 618 Organizations Hit by Infostealers and Ransomware
The threat actor known as EncryptHub, also called Larva-208, has launched a significant cyberattack. This EncryptHub breach affected at least 618 organizations worldwide.
EncryptHub used spear-phishing and social engineering. They gained access to corporate networks. The attacks involved SMS phishing, voice phishing, and fake login pages. These pages mimicked popular VPN services. These included Cisco AnyConnect, Palo Alto GlobalProtect, Fortinet, and Microsoft 365.
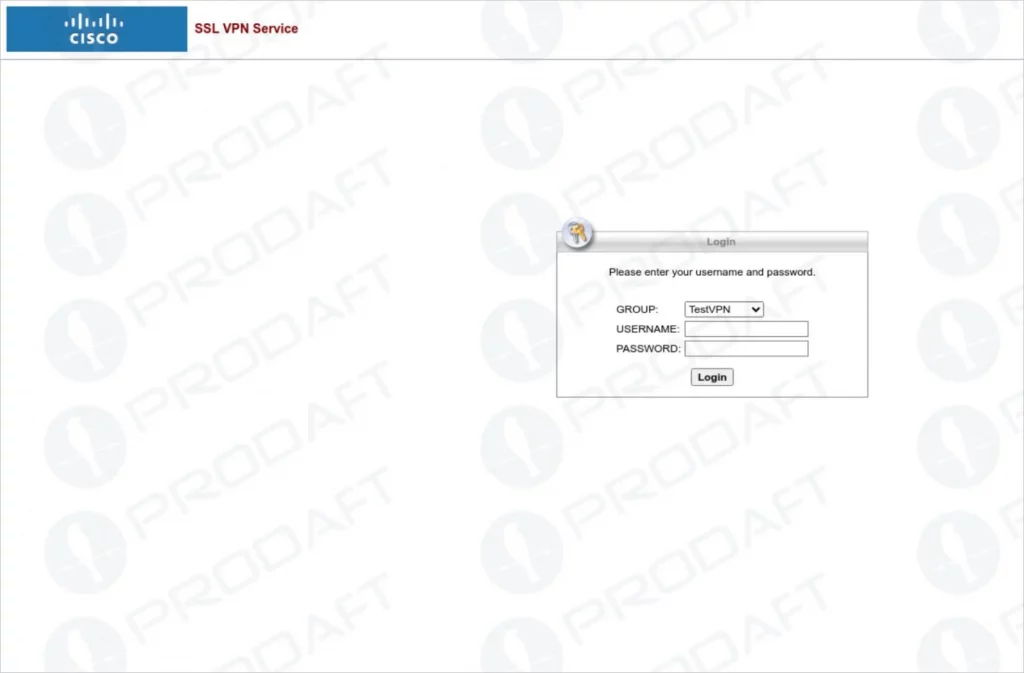
Fake Cisco login page
Source: Prodaft
The attackers impersonated IT support. They claimed issues with VPN access or account security. This tricked victims into visiting phishing sites. Victims entered credentials and MFA tokens. The sites then redirected victims to legitimate services. This avoided suspicion.
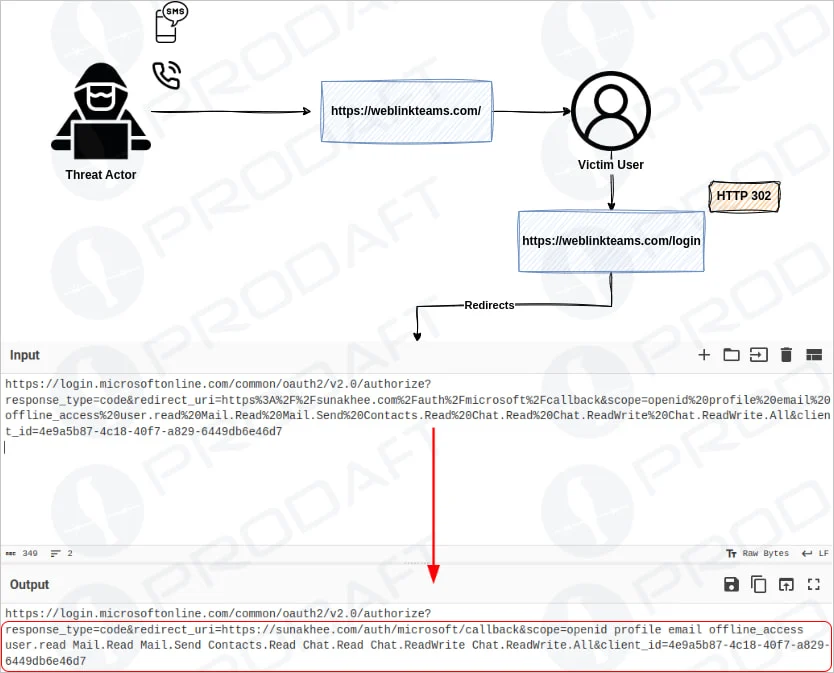
Overview of the phishing process
Source: Prodaft
EncryptHub registered over 70 domains. These mimicked legitimate services. Examples include ‘linkwebcisco.com’ and ‘weblinkteams.com’. This made the phishing pages appear legitimate. They used bulletproof hosting providers like Yalishanda. These providers often ignore takedown requests.
Another group, Larva-148, helped with domain purchases. They managed hosting and infrastructure. Their exact relationship with EncryptHub is unclear. They may sell domains and phishing kits.
PowerShell scripts and Malware Deployment
After gaining access, EncryptHub deployed various tools. They used PowerShell scripts and malware. This ensured persistence, remote access, data theft, and file encryption.
First, they tricked victims into installing RMM software. This included AnyDesk, TeamViewer, ScreenConnect, Atera, and Splashtop. This gave them remote control. It allowed for long-term access and lateral movement.
Next, they deployed infostealers. These included Stealc, Rhadamanthys, and Fickle Stealer. These stole data from web browsers. This included saved credentials, session cookies, and cryptocurrency wallet information. BleepingComputer also saw Python scripts for Linux and Mac devices.
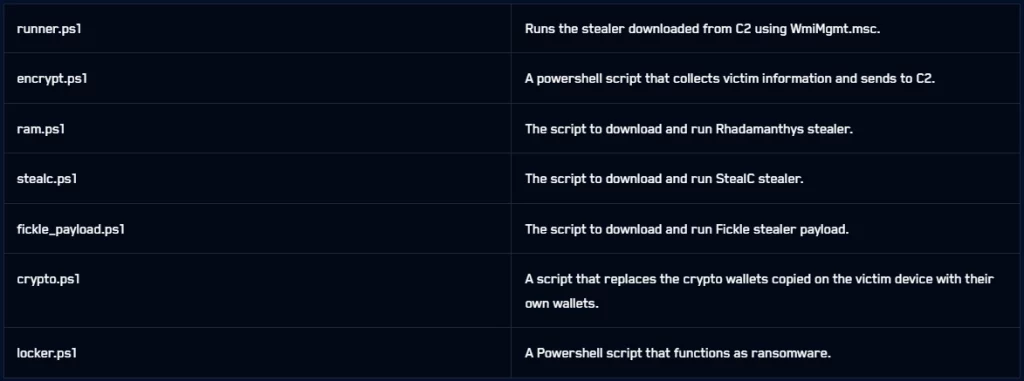
Custom PowerShell scripts
Source: Prodaft
The stolen data included:
- Data from various cryptocurrency wallets. This included MetaMask, Ethereum Wallet, Coinbase Wallet, Trust Wallet, Opera Wallet, Brave Wallet, TronLink, Trezor Wallet, and many others.
- Configuration data for VPN clients. This included Cisco VPN Client, FortiClient, Palo Alto Networks GlobalProtect, OpenVPN, and WireGuard.
- Data from password managers. This included Authenticator, 1Password, NordPass, DashLane, Bitwarden, RoboForm, Keeper, MultiPassword, KeePassXC, and LastPass.
- Files matching specific extensions or keywords. Keywords included “pass,” “account,” “auth,” “2fa,” “wallet,” “seedphrase,” “recovery,” “keepass,” “secret,” and many others.
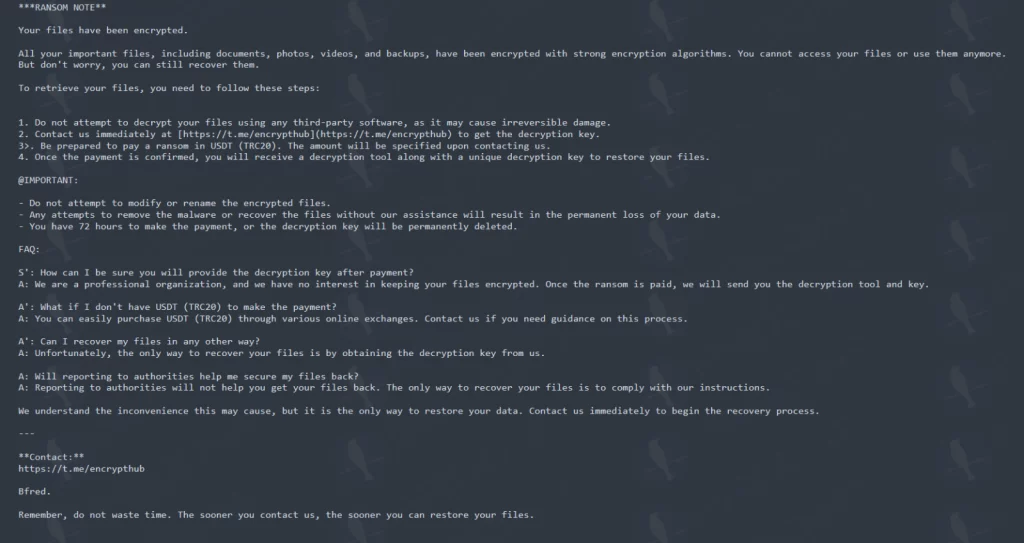
Larva-208’s ransom note
Source: Prodaft
Finally, EncryptHub deployed ransomware. This was a custom PowerShell-based encryptor. It used AES encryption. It appended the “.crypted” extension. Original files were deleted. A ransom note demanded payment in USDT via Telegram.
Prodaft’s Assessment of EncryptHub Ransomware
Prodaft described EncryptHub as sophisticated. They tailor attacks for better effectiveness. They achieve high-value breaches on large organizations.
“The LARVA-208 spear-phishing actor examined in this report exemplifies the increasing sophistication of targeted cyber attacks,” warns Prodaft. “By employing highly customized social engineering tactics, advanced obfuscation methods, and meticulously crafted lures, this threat actor has demonstrated a significant capability to evade detection and compromise high-value targets.”
This EncryptHub breach highlights the ongoing threat of sophisticated cyberattacks. Organizations need strong security measures to protect themselves. This includes robust phishing defenses and multi-factor authentication. Regular security awareness training for employees is crucial.









