The dark web leak site associated with the Everest ransomware operation has been defaced and is now offline, marking a significant development in the ongoing battle against cybercrime. This incident highlights the vulnerabilities even sophisticated cybercriminal groups face and underscores the importance of robust cybersecurity practices for businesses.
The Defacement and its Aftermath
The Everest ransomware gang’s leak site, a crucial component of their double-extortion strategy, was compromised over a weekend. The unknown attacker replaced the site’s original content with a provocative message: “Don’t do crime CRIME IS BAD xoxo from Prague.” This act of defacement effectively disrupted the gang’s ability to leverage stolen data to pressure victims into paying ransoms. Currently, attempts to access the site result in an “Onion site not found” error, indicating its complete unavailability.
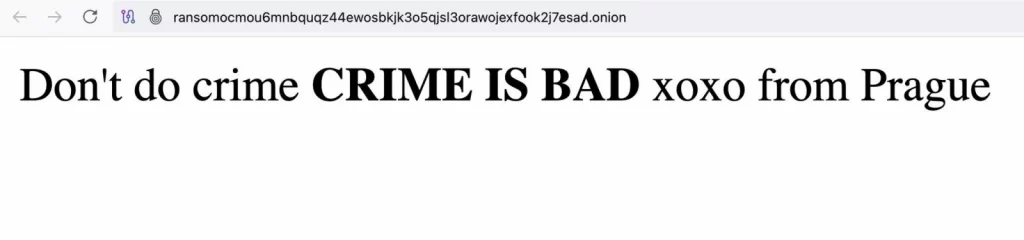
Everest’s defaced leak site (Tammy H.)
While the precise method of attack remains unconfirmed, security experts have pointed towards a potential vulnerability in the website’s infrastructure as the likely entry point. Flare Senior Threat Intelligence Researcher Tammy Harper suggested that a weakness in the WordPress template used by Everest could have been exploited: “It is worth mentioning that Everest was using a WordPress template for their blog. I would not be surprised if that was how this happened.” This highlights the importance of regularly updating and patching website software to mitigate known vulnerabilities.
Everest’s Evolving Tactics and Impact
Everest ransomware’s operations have significantly evolved since its emergence in 2020. Initially focusing on data exfiltration as a primary extortion tactic, the group has expanded its methods to include ransomware encryption of victim systems. This double-extortion approach maximizes their leverage, forcing victims to choose between paying a ransom to decrypt their data or facing the public release of sensitive information. Furthermore, Everest has established itself as an initial access broker, selling access to compromised corporate networks to other threat actors, expanding its reach and impact within the cybercriminal ecosystem.
The group’s leak site, prior to its defacement, contained data from over 230 victims accumulated over five years. This data served as a potent weapon in their extortion efforts. High-profile victims include STIIIZY, a California-based cannabis brand, whose point-of-sale (POS) vendor was compromised, leading to the theft of customer information including purchase details and government-issued IDs. The U.S. Department of Health and Human Services also issued a warning in August 2024 regarding Everest’s increasing targeting of healthcare organizations across the United States.
Implications for Businesses
The defacement of Everest’s leak site, while a temporary setback for the group, serves as a stark reminder of the ever-present threat of ransomware attacks. Businesses must prioritize proactive cybersecurity measures to protect themselves against similar attacks. This includes:
- Regular software updates and patching
- Robust endpoint protection
- Employee security awareness training
- Data backup and recovery plans
- Incident response planning
The incident underscores the need for a multi-layered security approach and the importance of staying vigilant against evolving cyber threats. The ongoing evolution of ransomware tactics necessitates a proactive and adaptable security posture to mitigate the risks posed by these sophisticated cybercriminal groups.