This report details the surprising dual identity of EncryptHub, a prolific threat actor. This individual, also known as SkorikARI, secretly reported critical Windows zero-day vulnerabilities to Microsoft. This revelation exposes a complex figure operating within both the cybercriminal and legitimate security research worlds.
Vulnerability Reporting and Patching
EncryptHub, under the alias SkorikARI, reported two zero-day vulnerabilities to Microsoft. These were CVE-2025-24061 (Mark of the Web bypass) and CVE-2025-24071 (File Explorer spoofing). Microsoft addressed these vulnerabilities in their March 2025 Patch Tuesday updates, crediting SkorikARI for the report.
Unmasking EncryptHub’s Dual Identity
Outpost24 researchers connected EncryptHub and SkorikARI through a security breach. EncryptHub accidentally exposed their credentials, revealing links to various online accounts. This exposed profile highlighted the individual’s oscillation between cybersecurity research and malicious activities.
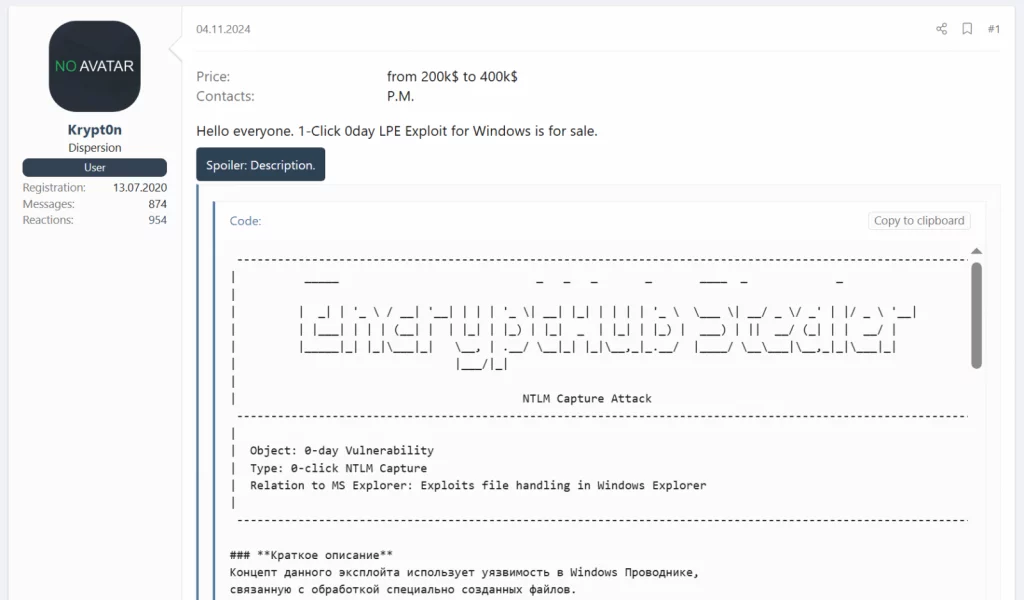
EncryptHub attempting to sell a zero-day on underground forums
Source: BleepingComputer
Hector Garcia of Outpost24 explained the evidence: “The hardest evidence was from the fact that the password files EncryptHub exfiltrated from his own system had accounts linked to both EncryptHub, like credentials to EncryptRAT, which was still in development, or his account on xss.is, and to SkorikARI, like accesses to freelance sites or his own Gmail account.”
He continued, “There was also a login to hxxps://github[.]com/SkorikJR, which was mentioned in July’s Fortinet Article about Fickle Stealer, bringing it all together. Another huge confirmation of the link between the two were the conversations with ChatGPT, where activity related both to EncryptHub and to SkorikARI can be observed.”
Previous Zero-Day Activities and Operational Security Failures
This wasn’t EncryptHub’s first involvement with zero-day vulnerabilities. Evidence suggests attempts to sell zero-days to other cybercriminals on hacking forums.
Outpost24’s investigation revealed EncryptHub’s inconsistent activities—switching between freelance work and cybercrime. Despite their technical skills, poor operational security (OPSEC) led to the exposure of personal information.
ChatGPT Interactions and Self-Assessment
The investigation uncovered EncryptHub’s use of ChatGPT for various malicious purposes: malware development, phishing site creation, code integration, and vulnerability research.
A ChatGPT conversation even included a self-assessment: “40% black hat, 30% grey hat, 20% white hat, and 10% uncertain,” reflecting their conflicted nature. The conversation also revealed plans for a large-scale, though supposedly “harmless,” publicity stunt affecting tens of thousands of computers.
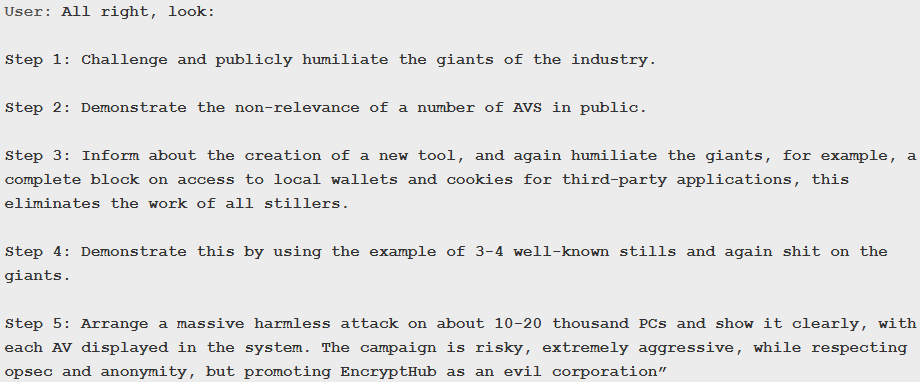
Exposed ChatGPT discussion
Source: Outlook24
EncryptHub’s Criminal Activities and Impact
EncryptHub is loosely connected to ransomware groups like RansomHub and BlackSuit. They are known for sophisticated social engineering campaigns, phishing attacks, and the creation of Fickle Stealer, a custom PowerShell-based infostealer.
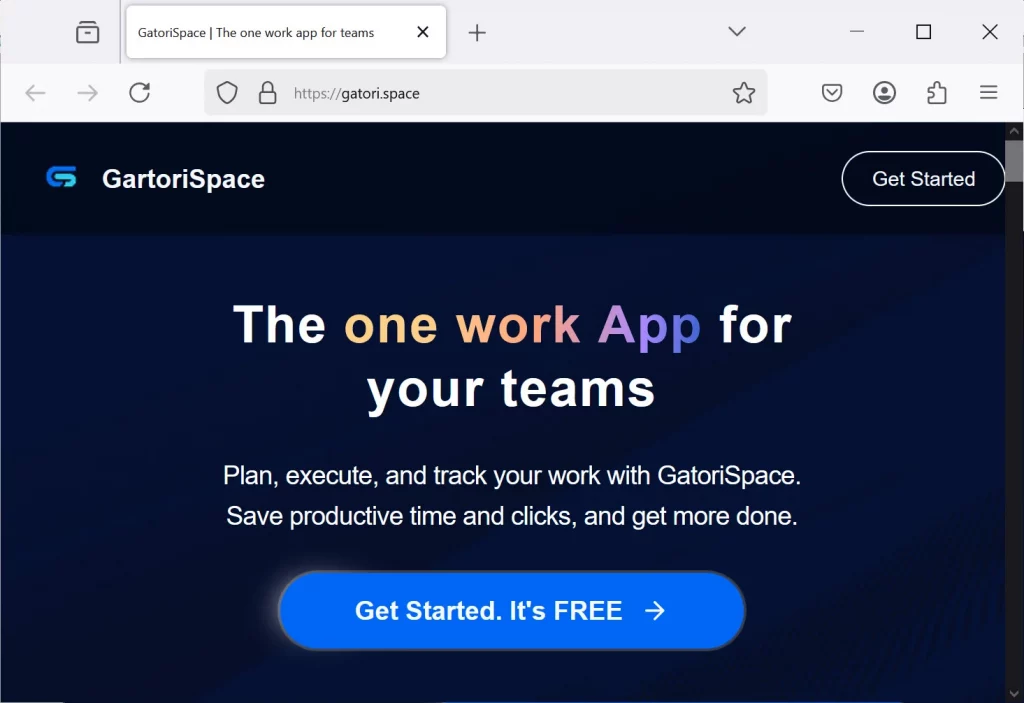
Fake GartoriSpace website
Source: BleepingComputer
One campaign involved a fake project management application, GartoriSpace, distributed via social media.
This delivered Fickle Stealer (Windows) and AMOS (Mac). EncryptHub has also been linked to attacks exploiting CVE-2025-26633, a Microsoft Management Console vulnerability. Prodaft reports over six hundred organizations have been compromised by EncryptHub’s activities.









