A weakness discovered in DoNex ransomware’s cryptographic scheme
Antivirus giant Avast has discovered a vulnerability in the cryptographic implementation of the DoNex ransomware family that allows victims to decrypt their files for free. Avast has been leveraging this weakness since March 2024 to privately help law enforcement provide decryption to DoNex ransomware victims. However, the flaw was publicly disclosed at last month’s Recon 2024 cybersecurity conference. Therefore, Avast has now decided to release the decryptor tool to the public.
DoNex ransomware’s evolution and activity
DoNex is a rebrand of the DarkRace ransomware from 2024, which itself was a rebrand of the Muse ransomware initially released in April 2022. Based on Avast’s telemetry, recent DoNex activity was focused mainly in the United States, Italy, and Belgium, but it had a worldwide reach.
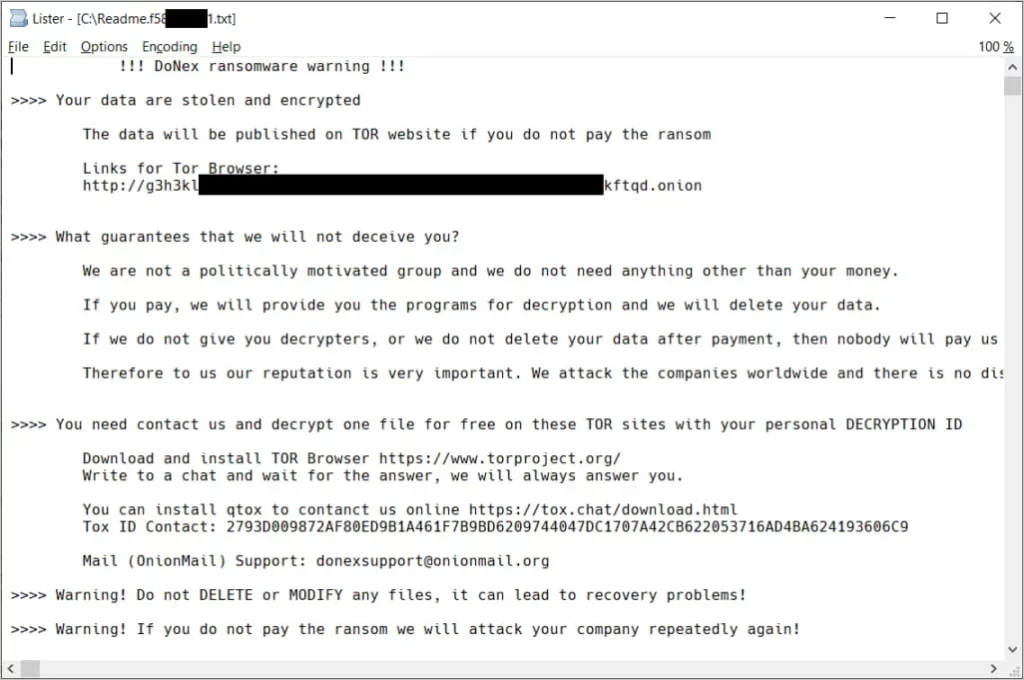
A sample DoNex ransom note shared by Avast demands a payment in Bitcoin for decryption.
Technical details of the vulnerability
During encryption, DoNex ransomware first generates an encryption key using the ‘CryptGenRandom()’ function to initialize a ChaCha20 symmetric key. This key is then used to encrypt victims’ files. However, after file encryption, the ChaCha20 key is encrypted with RSA-4096 and appended to each encrypted file. Avast discovered a weakness in either the key generation, reuse, padding, or another aspect of this process.
Notably, DoNex uses intermittent encryption for files larger than 1MB, speeding up the encryption process but introducing vulnerabilities. This likely played a role in Avast’s ability to develop a decryptor.
Avast’s free DoNex Rasomware decryptor
Avast’s decryptor works on all DoNex variants like DarkRace and Muse due to exploiting the underlying flaw. It is available for free on Avast’s website.
The 64-bit version is recommended as the password cracking step requires significant memory. The tool requires administrative privileges and a pairing of an encrypted file with its original, undamaged version. Larger files make for better “examples” to determine maximum decryptable file size. Backups should be made before decryption in case of errors.
With this vulnerability now publicly known, Avast has taken the important step of freely providing DoNex victims with a decryptor to recover their files without paying the ransom. This highlights the ongoing cat-and-mouse game between malware authors and security researchers, where technical flaws may be leveraged to defeat encryption without reward criminal groups.









