Ukraine’s Computer Emergency Response Team (CERT-UA) issued a warning about sophisticated spear-phishing attacks leveraging compromised Signal accounts. These attacks target defense industry employees and military personnel.
The attacks, which began this month, involve Signal messages containing archives disguised as meeting reports. The malicious archives contain a PDF, acting as a lure, and an executable file. Opening the PDF triggers the execution of the executable.
This executable is identified as the DarkTortilla cryptor/loader. Upon execution, it decrypts and launches the Dark Crystal RAT (DCRAT), a remote access trojan. This allows attackers to gain unauthorized access to systems and potentially steal sensitive data.
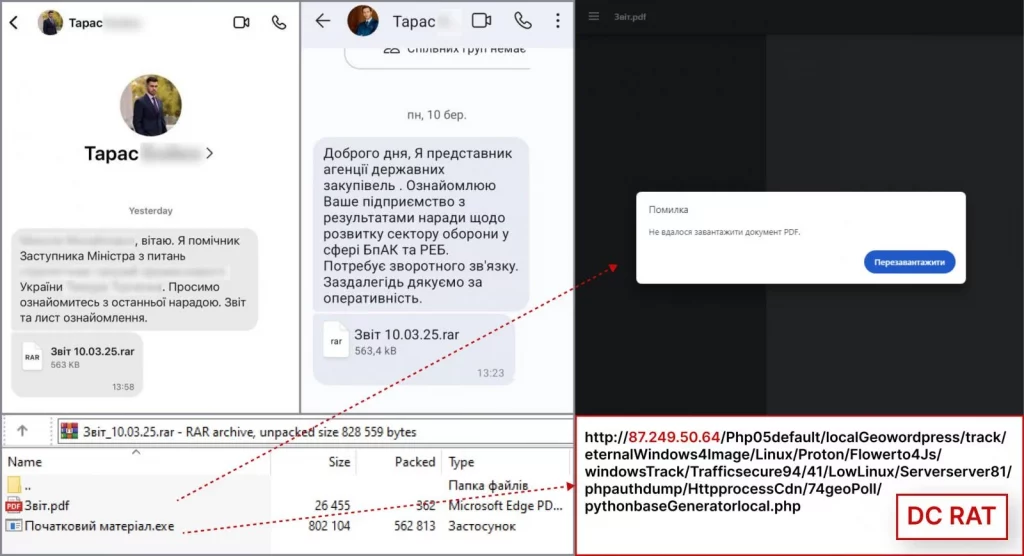
Overview of the DCRAT attack
Source: CERT-UA
The CERT-UA tracks this activity under UAC-0200, a threat cluster that has used Signal in similar attacks since June 2024. However, recent attacks show a notable evolution.
“Starting in February 2025, the bait messages have shifted their focus to topics related to UAVs, electronic warfare systems, and other military technologies,” explains CERT-UA in its recent bulletin.
This indicates the attackers are adapting their tactics to exploit current events and interests within the Ukrainian military.
In February 2025, Google’s Threat Intelligence Group (GTIG) reported that Russian hackers were exploiting Signal’s “Linked Devices” feature to compromise accounts. This highlights the importance of regularly reviewing linked devices on your Signal account. This sophisticated spear-phishing attack underscores the need for robust cybersecurity measures within organizations, especially those handling sensitive information.
Mitigation Strategies:
Signal users, particularly those in high-risk positions, should take the following precautions:
- Disable automatic attachment downloads.
- Exercise extreme caution with all messages, especially those containing files.
- Regularly check the list of linked devices in Signal.
- Update the Signal app to the latest version on all devices.
- Enable two-factor authentication.
Staying informed about the latest threats and implementing robust security practices are essential for protecting your organization.
Helpful Reads:









