A new Mirai botnet is behind a significant increase in attacks targeting TVT NVMS9000 digital video recorders (DVRs). The surge, peaking on April 3rd, 2025, involved over 2,500 unique IP addresses scanning for vulnerable devices.
These attacks exploit an information disclosure vulnerability detailed in an SSD Advisory from May 2024. The vulnerability allows attackers to obtain admin credentials in cleartext using a single TCP payload, bypassing authentication and granting unrestricted administrative access.
GreyNoise, a threat monitoring platform, linked the activity to a Mirai-based malware. Infected devices are commonly used for malicious activities such as proxying traffic, cryptomining, or launching distributed denial-of-service (DDoS) attacks. GreyNoise logged 6,600 distinct malicious, non-spoofable IPs over the past month associated with this activity.
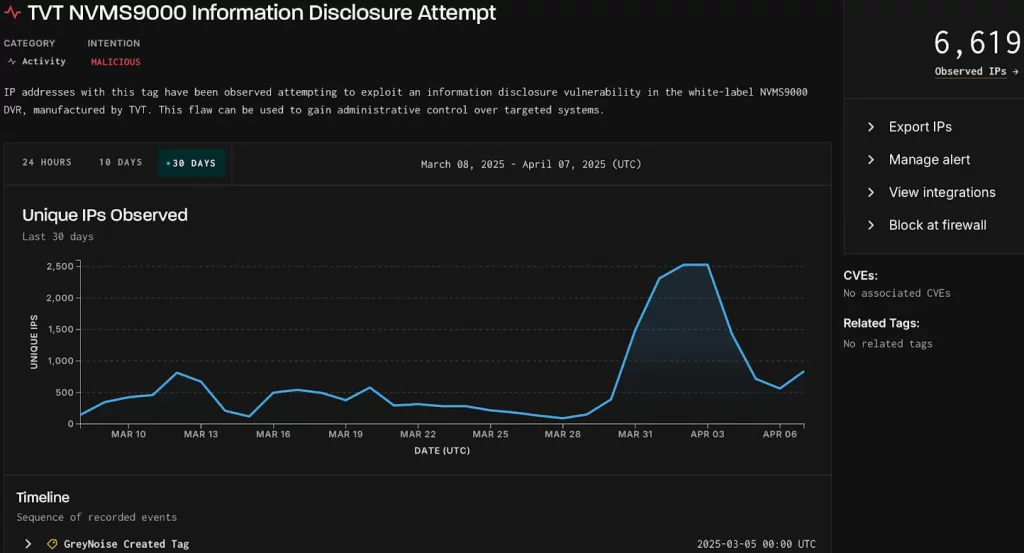
Spike in exploitation attempts
Source: GreyNoise
The attacks primarily originate from Taiwan, Japan, and South Korea, targeting devices mainly in the U.S., the U.K., and Germany. The TVT NVMS9000 DVRs are commonly used in security and surveillance systems. Their internet connectivity makes them attractive targets for botnets, exploiting even five-year-old vulnerabilities. Past examples include HiatusRAT, Mirai, and FreakOut botnets.
According to SSD’s advisory, upgrading to firmware version 1.3.4 or later resolves the vulnerability. If upgrading is not feasible, restricting public internet access to DVR ports and blocking incoming requests from GreyNoise’s listed IP addresses are recommended mitigation strategies.
Signs of Mirai infection on DVRs include unusual outbound traffic, performance issues, crashes, high resource usage even when idle, and configuration changes. If these are observed, disconnecting, factory resetting, updating firmware, and network isolation are crucial steps. The last firmware update for the NVMS9000 was in 2018, raising concerns about ongoing support.









