In a major international cybersecurity operation, authorities and private sector partners have dismantled the infrastructure of the Lumma Infostealer malware, a dominant player in the malware-as-a-service (MaaS) ecosystem. Microsoft, in collaboration with law enforcement agencies and industry leaders, seized approximately 2,300 domains used to control the Lumma operation, severing the link between infected systems and cybercriminals.
The coordinated takedown began on May 13, 2025, and was supported by the U.S. Department of Justice, Europol’s European Cybercrime Center (EC3), and Japan’s Cybercrime Control Center (JC3). Microsoft reported that between March 16 and May 16, over 394,000 Windows devices were found to be infected with Lumma malware, also known as LummaC2.

Domain seizure banner (Microsoft)
Authorities also seized Lumma’s backend control panel and criminal marketplaces used to rent the information stealer malware. According to Microsoft’s Digital Crimes Unit, the operation “severed communications between the malicious tool and victims,” imposing operational and financial disruption on both operators and users of the service.
Cloudflare, another major player in the effort, revealed that Lumma Stealer had abused its services to obscure the IP origins of data exfiltration servers. Even after domains were suspended, the malware managed to bypass Cloudflare’s interstitial warning page. As a countermeasure, Cloudflare enhanced its defenses by integrating its Turnstile verification service.
Other cybersecurity firms—including ESET, Bitsight, Lumen, CleanDNS, GMO Registry, and legal experts at Orrick—contributed to the effort, demonstrating the scale and complexity of modern cybercrime takedown operations.
Lumma is a subscription-based information stealer malware offered for $250 to $1,000, depending on capabilities. Compatible with Windows and macOS, it is designed to evade security software and extract sensitive data including credentials, cookies, cryptocurrency wallet keys, and browser histories from platforms like Google Chrome, Firefox, and Microsoft Edge.
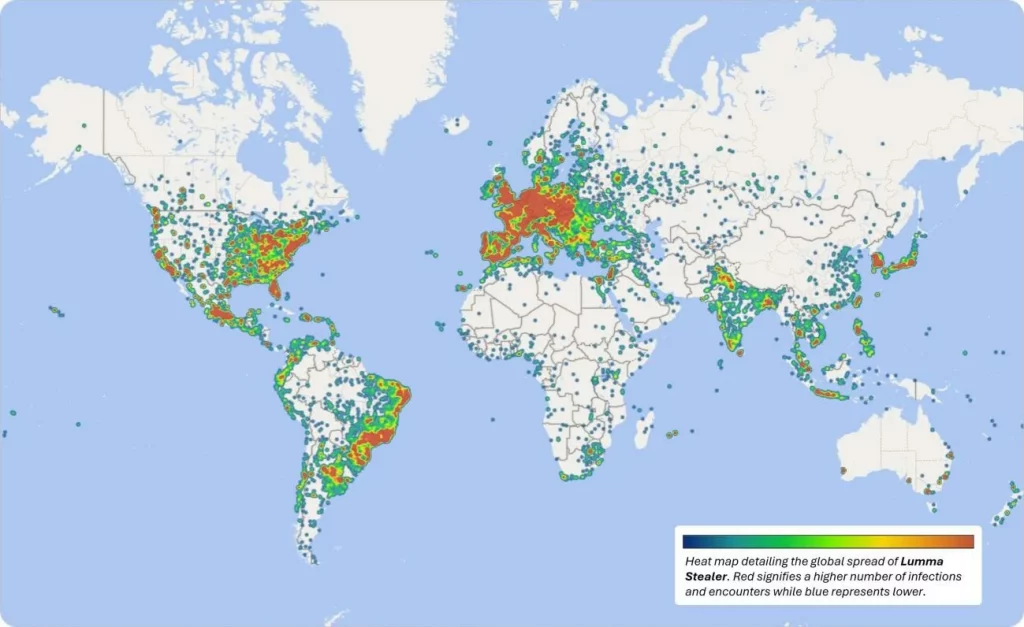
Lumma infections heat map (Microsoft)
The malware has been distributed via phishing, malvertising, GitHub comment injections, and fraudulent deepfake image generator websites. Once installed, Lumma compiles stolen information into encrypted archives and transmits them to attacker-controlled infrastructure for resale or further exploitation.
First appearing on underground forums in December 2022, Lumma rapidly rose in popularity among cybercriminal groups, including the infamous Scattered Spider collective. It played a role in recent breaches at PowerSchool, CircleCI, HotTopic, and Snowflake.
According to IBM X-Force’s 2025 threat report, infostealer malware usage surged dramatically in the past year. Credential data for sale on dark web markets rose 12%, while infostealer delivery via phishing increased by 84%. Lumma is currently the most dominant infostealer variant observed in these trends.
Stolen credentials have also enabled infrastructure-level attacks, such as the hijacking of Orange Spain’s RIPE account to corrupt BGP and RPKI routing configurations.
To further support enterprise defense, the FBI and CISA released a joint advisory outlining Lumma’s indicators of compromise (IOCs) and detailed tactics, techniques, and procedures (TTPs) associated with the malware’s deployment.
The dismantling of Lumma’s network underscores the growing sophistication of information stealer malware operations and the urgent need for collaborative, global countermeasures to address the evolving threat landscape.









