FinalDraft Malware: New Stealthy Cyber Attack Abuses Outlook for Command and Control
A new and sophisticated malware, dubbed FinalDraft, is leveraging the seemingly innocuous feature of Outlook email drafts for covert command-and-control (C2) communication.
This stealthy approach allows attackers to maintain persistent access and exfiltrate data while evading detection. The malware is a key component of the REF7707 cyber espionage campaign, initially targeting a South American ministry but with links to Southeast Asian victims.
What is FinalDraft Malware?
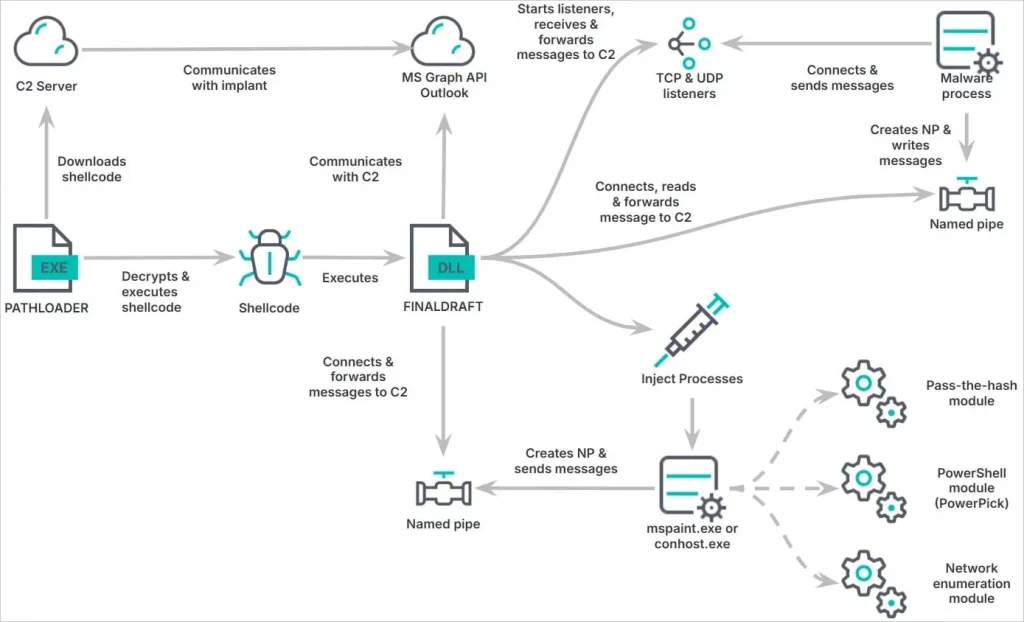
FinalDraft is a backdoor malware used for data exfiltration and process injection. It’s part of a larger toolset that includes a custom malware loader, PathLoader, and several post-exploitation utilities.
PathLoader, designed to bypass static analysis, uses API hashing and string encryption. FinalDraft establishes communication through the Microsoft Graph API, sending and receiving commands via Outlook email drafts. This method cleverly avoids detection by blending into typical Microsoft 365 traffic.
How the FinalDraft Malware Works
The attack chain begins with the deployment of PathLoader. This malware loader downloads and executes the FinalDraft malware. FinalDraft then obtains an OAuth token from Microsoft using a refresh token embedded in its configuration.
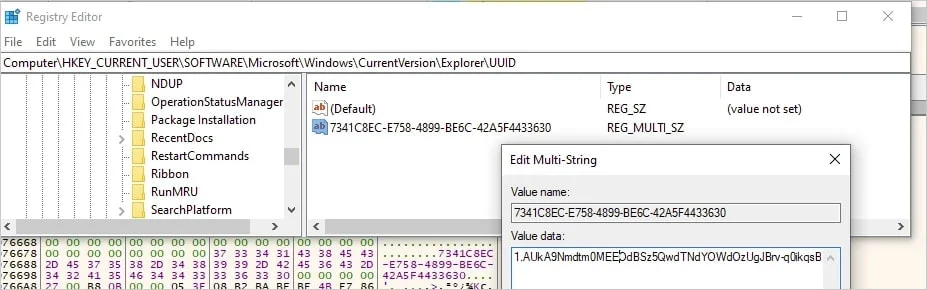
Token stored in the Windows Registry
Source: Elastic Security
This token is stored in the Windows Registry for persistent access. Commands from the attacker are hidden in drafts (r_), and responses are stored in new drafts (p_). After execution, these drafts are deleted, hindering forensic analysis.
Capabilities of FinalDraft Malware
FinalDraft boasts 37 commands, including:
- Data exfiltration (files, credentials, system info)
- Process injection (using legitimate processes like
mspaint.exe) - Pass-the-Hash attacks (for lateral movement)
- Network proxying (creating covert tunnels)
- File operations (copying, deleting, or overwriting files)
- PowerShell execution (without launching
powershell.exe)
A Linux variant of FinalDraft also exists, utilizing various communication methods, including Outlook via REST and Graph APIs, HTTP/HTTPS, UDP/ICMP, TCP, and DNS-based C2.
Token stored in the Windows Registry
Source: Elastic Security
The REF7707 Campaign and Wider Implications
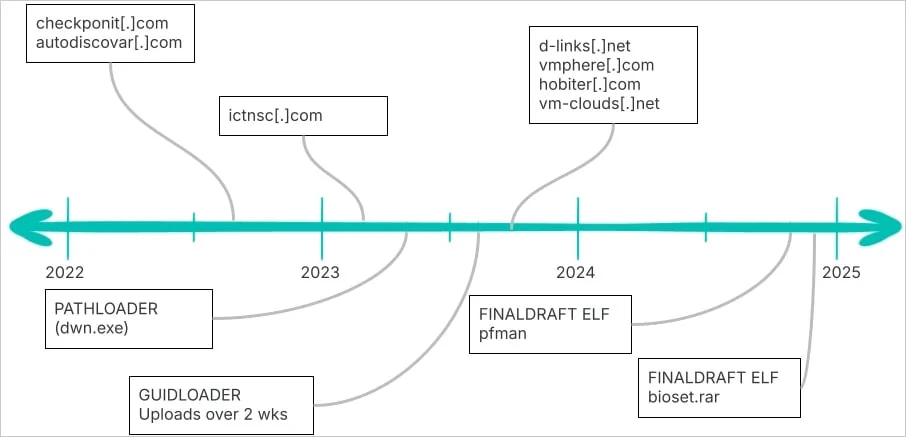
Elastic Security Labs, who discovered the malware, detailed the REF7707 campaign in a separate report. While sophisticated, the attackers made operational security (opsec) mistakes leading to their exposure.
The campaign’s focus on a South American foreign ministry, coupled with links to Southeast Asian victims, suggests a broader, potentially state-sponsored operation. The researchers also uncovered another malware loader, GuidLoader.
Token stored in the Windows Registry
Source: Elastic Security
The attackers repeatedly targeted high-value institutions through compromised endpoints in telecommunications and internet infrastructure providers in Southeast Asia. A compromised Southeast Asian university’s public-facing storage system was used to host malware payloads.
Detection and Mitigation
YARA rules for detecting GuidLoader, PathLoader, and FinalDraft are available in Elastic’s reports. Organizations should prioritize strong security practices, including regular patching, endpoint detection and response (EDR) solutions, and security awareness training to mitigate the risk of similar cyber attacks.
The use of multi-factor authentication (MFA) is crucial to reducing the impact of credential theft. This sophisticated malware highlights the ever-evolving nature of cyber threats and the need for robust cybersecurity defenses. The implications extend beyond ransomware; this is a clear example of cyber espionage targeting critical infrastructure and sensitive government data.









