The Cybersecurity and Infrastructure Security Agency (CISA) has issued an emergency directive to Federal Civilian Executive Branch (FCEB) agencies. The directive aims to address two Ivanti zero-day vulnerabilities found in Ivanti Connect Secure and Ivanti Policy Secure.
These Ivanti Zero-Day vulnerabilities have been actively exploited by multiple threat actors. It is worth noting that these attacks have been ongoing since December, targeting vulnerable Ivanti appliances through authentication bypass (CVE-2023-46805) and command injection (CVE-2024-21887) vulnerabilities. Despite the attacks, the vendor has not yet released any security patches.
Emergency Directive 24-01 Details Ivanti Zero-Day Vulnerabilities and Mitigations
In accordance with emergency directive ED 24-01, federal agencies are now required to expeditiously implement the mitigation measures provided by Ivanti to effectively block any attempted attacks.
The two Ivanti zero-day vulnerabilities when chained, enable attackers to navigate through a target’s network, extract data, and establish persistent access to systems by deploying backdoors.
“CISA has determined these conditions pose an unacceptable risk to Federal Civilian Executive Branch (FCEB) agencies and require emergency action,”
CISA said in its directive.
According to the threat monitoring service Shadowserver, there are currently over 16,200 ICS VPN appliances exposed online, with over 4,700 of them located in the United States.
Additionally, Shodan, another internet scanning service, has identified almost 17,000 Ivanti ICS devices that are accessible on the internet. Shadowserver is actively monitoring the global count of compromised Ivanti Connect Secure VPN instances and exploitation attempts.
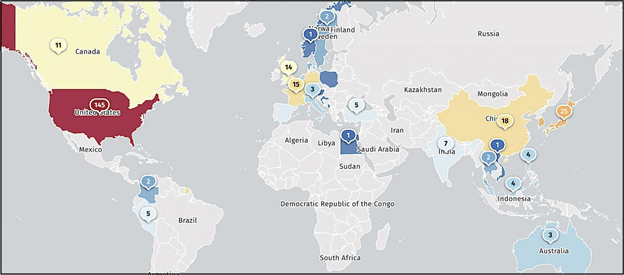
Compromised Ivanti appliances
Source: Shadowserver
On January 18, they detected more than 420 hacked devices alone.
Ivanti Zero-Day Actively Exploited to Drop Crypto-Miners and Additional Malware
According to the threat intelligence company Volexity, a suspected Chinese state-backed threat group known as UTA0178 and UNC5221 has already compromised more than 2,100 Ivanti appliances using a webshell variant called GIFTEDVISITOR.
During their investigation into these Zero-Day attacks, Mandiant discovered the presence of five custom malware strains on the compromised systems of affected customers. These malware strains were specifically designed to carry out various malicious activities, including credential theft, deployment of webshells, and additional harmful payloads.
The threat actor has been actively involved in harvesting and stealing sensitive information, including account and session data, from the compromised networks.
The victims identified so far encompass a wide range of organizations, including government and military departments worldwide, national telecom companies, defense contractors, technology companies, banking and financial institutions, accounting organizations, global consulting firms, as well as aerospace, aviation, and engineering companies.
These victims of the critical Ivanti auth bypass bug vary significantly in size and scale, ranging from small businesses to large multinational organizations, including multiple Fortune 500 companies across various industry sectors.
Volexity and GreyNoise have observed the attackers deploying XMRig cryptocurrency miners and Rust-based malware payloads that are still awaiting analysis.
Third Ivanti Vulnerability Exploited in the Wild
In response to these vulnerabilities, Ivanti, the security vendor, has scheduled the release of patches starting this week. However, in the meantime, Ivanti has also provided mitigation measures, which CISA has requested impacted organizations to download and implement.
“This directive requires agencies to implement Ivanti’s published mitigation immediately to the affected products in order to prevent future exploitation,”
CISA noted.
“As this initial action does not remedy an active or past compromise, agencies are also required to run Ivanti’s External Integrity Checker Tool and take additional steps if indications of compromise are detected.”









