The Largest Data Breach in History Just Happened
Security researchers have uncovered what may be the most significant data breach in internet history. According to Cybernews, over 16 billion login credentials have been exposed across 30 separate datasets, many of which have never been reported before.
This discovery includes credentials tied to virtually every major online platform—from Facebook, Google, and Apple to enterprise logins, VPN services, government portals, and messaging platforms like Telegram.
The leaked data appears to be compiled from infostealer malware, credential stuffing dumps, and previously unreleased breach material. Crucially, most of the data is recent, not recycled.
“This is not just a leak – it’s a blueprint for mass exploitation,” said the researchers. “With over 16 billion records exposed, cybercriminals now have unprecedented access to personal credentials.”
What Was Leaked and Where It Came From
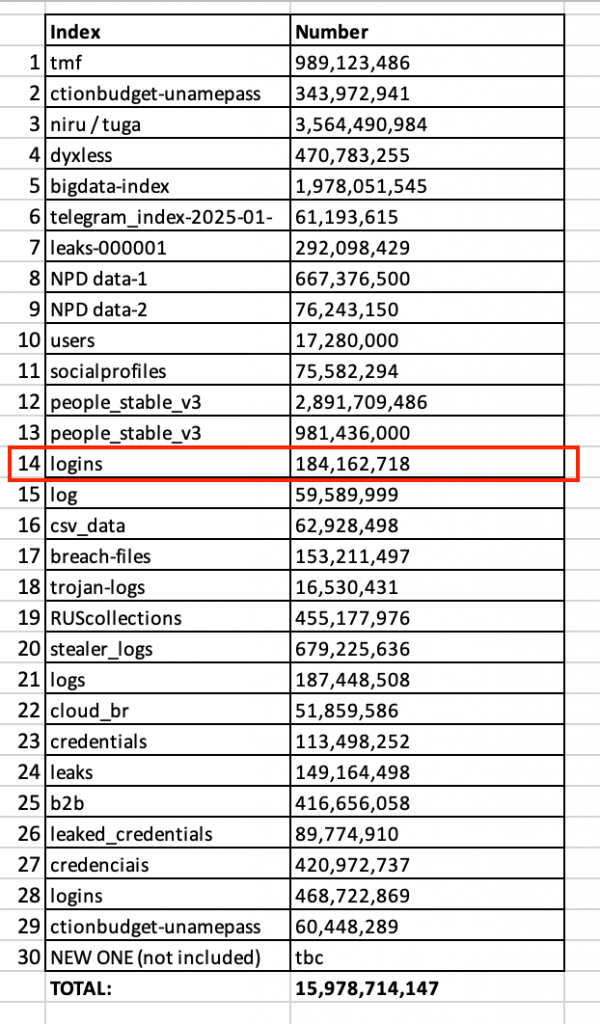
Researchers found:
- 30 exposed credential datasets
- Ranging from tens of millions to 3.5 billion records each
- Data from infostealer logs, credential dumps, and past breaches
- Records including URLs, login names, and plaintext passwords
- Some logs also include tokens, cookies, and session metadata
Screenshot by Bob Diachenko
The data follows the format used by modern infostealers—malware designed to capture login sessions, browser cookies, and saved passwords directly from infected devices.
One of the largest datasets, with 3.5 billion records, appeared to target Portuguese-speaking users. Others were named after malware or platforms like “Telegram,” while one dataset explicitly pointed to origins in the Russian Federation.
Are Big Tech Credentials Included?
Contrary to some media reports, there was no centralized breach of companies like Facebook, Google, or Apple. However, credentials for those services were found in infostealer logs.
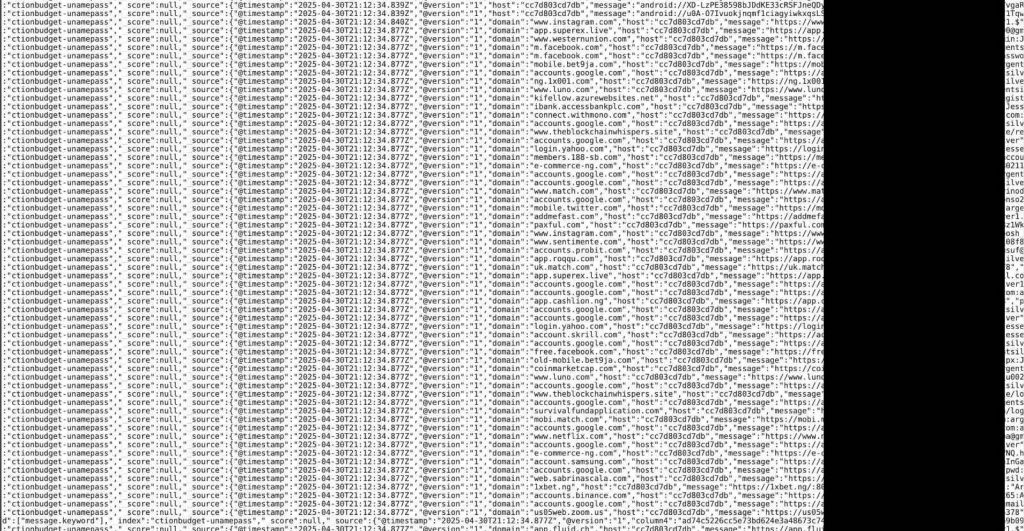
Below, you can see that they actually include URLs to Facebook, Google, Github, Zoom, Twitch, and other login pages.
Source: Cybernews
“Credentials we’ve seen in infostealer logs contained login URLs to Apple, Facebook, and Google login pages,” explained cybersecurity researcher Bob Diachenko.
So while the companies weren’t breached themselves, many users’ credentials for their services were compromised.
How the Data Was Discovered
Cybernews researchers had been monitoring the web since early 2024. The exposed datasets were found briefly accessible online through unsecured Elasticsearch databases and object storage systems.
The records surfaced intermittently, long enough for researchers to capture samples but short enough that it’s still unknown who compiled the collections.
Some believe security researchers may have collected parts of it for analysis. But many of the datasets were almost certainly compiled by cybercriminals.
How Dangerous Are These Credentials?
The impact goes far beyond login theft:
- Account Takeovers: Gaining access to one account could allow attackers to change passwords and lock out the user.
- Identity Theft: Personal accounts often contain sensitive data, which can be used to impersonate victims.
- Phishing Campaigns: With access to contact lists and email accounts, attackers can launch highly targeted phishing attempts.
- Credential Stuffing: If passwords are reused, hackers can use them on other services.
- Session Hijacking: Cookies and tokens in the logs can bypass 2FA, letting attackers access accounts without needing the password.
“The inclusion of both old and recent infostealer logs – often with tokens, cookies, and metadata – makes this data particularly dangerous,” Cybernews warned.
Why Is This Happening So Often?
There’s been a noticeable shift in the underground cybercrime world. According to researcher Aras Nazarovas, the volume and centralization of these datasets suggest criminals are moving away from Telegram groups and toward storing data in more traditional formats.
He explained that the datasets now resemble databases, making them easier to search, share, and exploit.
A Glimpse Into the Dark Web Marketplace
Most of these massive credential dumps end up on the dark web, where cybercriminals buy and sell stolen data. Many users are unaware their information is circulating underground long after the breach.
The dark web remains difficult to police, allowing these dumps to spread freely across forums, encrypted markets, and invite-only groups.
How Can You Protect Your Organization and Yourself?
While identifying every affected account is impossible, there are key steps that every business and user should take:
- Reset all account passwords, especially those reused across services
- Use a password manager to generate and store strong, unique passwords
- Enable multi-factor authentication (MFA) wherever available
- Audit your environment for signs of infostealer malware
- Monitor account activity and contact service providers if suspicious behavior is detected
According to the researchers, even cookies from stolen sessions can be used to bypass 2FA, so simply changing the password is not always enough. Some platforms do not reset all tokens after a password change.
Previous Breaches Set the Stage
This isn’t the first breach of its kind, but it is the largest of its type:
- RockYou2024: Nearly 10 billion unique passwords leaked in a public compilation
- MOAB (Mother of All Breaches): In early 2024, Cybernews uncovered 26 billion records from combined sources
- China mega breach: Leaked financial and personal data from WeChat and Alipay
These events underscore the ongoing failure in password hygiene and the persistent risks posed by infostealer malware.
“Even a success rate of less than one percent could compromise millions of accounts,” Cybernews warned.
What Happens When Hackers Get In?
With access to credentials, hackers can:
- Lock users out of their accounts and demand ransom
- Steal identities to open bank accounts or apply for loans
- Send phishing messages to users’ contacts
- Use the same credentials to breach work accounts
- View browser and email history to gather intelligence
- Sell private files, credit card numbers, and business documents
Implications of the 16-Billion Credential Leak for Enterprise Security Teams
This breach should be seen as a critical threat signal for enterprises. The attack surface has dramatically expanded with billions of credentials now exposed.
Corporate systems relying on passwords alone are at significant risk. Infostealer malware can easily infect unmanaged or remote endpoints and siphon data without being noticed.
Adopting zero trust principles, endpoint detection, secure session management, and hardened identity practices is more essential now than ever.
Looking for a trusted recovery solution? Defend your organization with StoneFly DR365—an air-gapped, immutable backup and recovery appliance trusted by enterprises to ensure zero data loss even in the event of complex cyberattacks.










