The source code for the VanHelsing ransomware-as-a-service (RaaS) operation has been leaked on a cybercrime forum after a disgruntled former developer attempted to sell it for $10,000. This leak includes core components of the VanHelsing ransomware builder, Windows encryptor, and the affiliate infrastructure used by the group.
VanHelsing, a multi-platform ransomware operation launched in March 2025, was designed to target Windows, Linux, BSD, ARM, and ESXi systems. Since its debut, it has claimed at least eight victims, according to Ransomware.live, making it a growing concern in the ransomware landscape.
Developer Leak Forces Public Release
Early this morning, a user identifying as ‘th30c0der’ advertised the sale of the VanHelsing ransomware builder and source code on the RAMP hacking forum. The offer included the TOR-hosted affiliate panel, file server, admin chat, data leak blog, and associated databases.
“vanhelsing ransomware source code for sell: include TOR keys + web panel for admin + chat + file server + blog include database everything,” the post read.
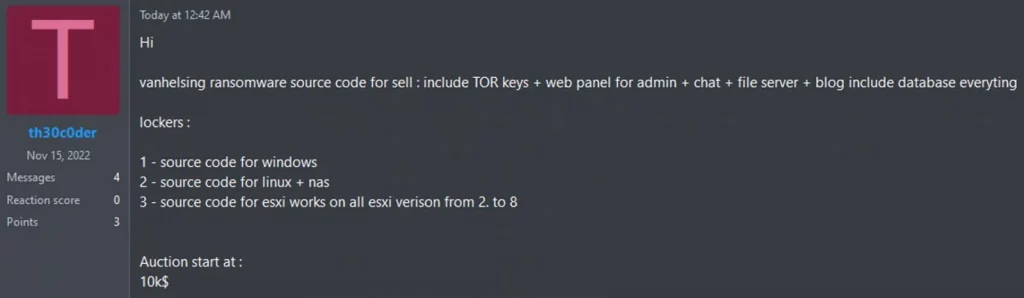
th30c0der attempting to sell the VanHelsing source code
In response, the official VanHelsing operators moved quickly to undercut the rogue sale. They released a portion of the VanHelsing source code themselves, claiming ‘th30c0der’ was a former developer attempting to scam buyers.
“Today we are announcing that we are publishing the old sources codes and will soon come back with the new and improved version of the locker (VanHelsing 2.0),” stated the VanHelsing group.
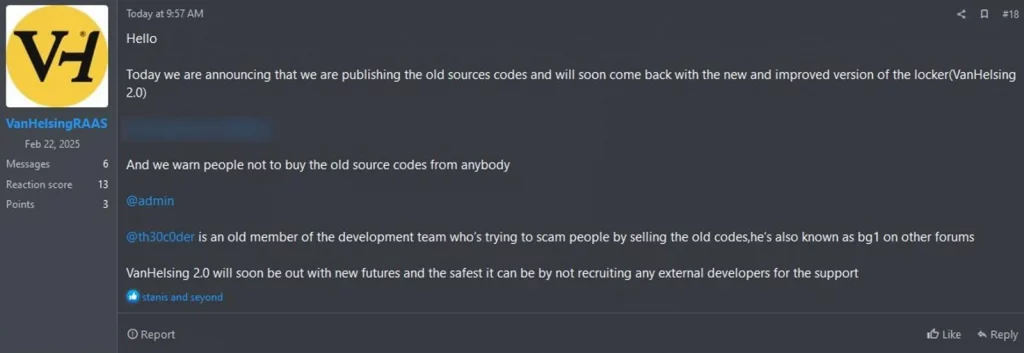
VanHelsin RaaS releases the source code on RAMP
Leak Confirmed: Builder, Panel, and Encryptor Exposed
BleepingComputer obtained and verified the leaked archive, confirming that it includes:
- The Windows encryptor builder
- The affiliate panel source code
- The data leak blog code
- A decryptor and loader
- A partially developed MBR locker, meant to overwrite a system’s Master Boot Record with a custom bootloader displaying a ransom note
While the leaked archive is functional, it lacks critical elements like the Linux builder and the databases, which would have increased its utility for threat intelligence and cybersecurity teams. The Visual Studio project files were oddly stored in the “Release” directory—usually reserved for compiled binaries—suggesting a disorganized development process.
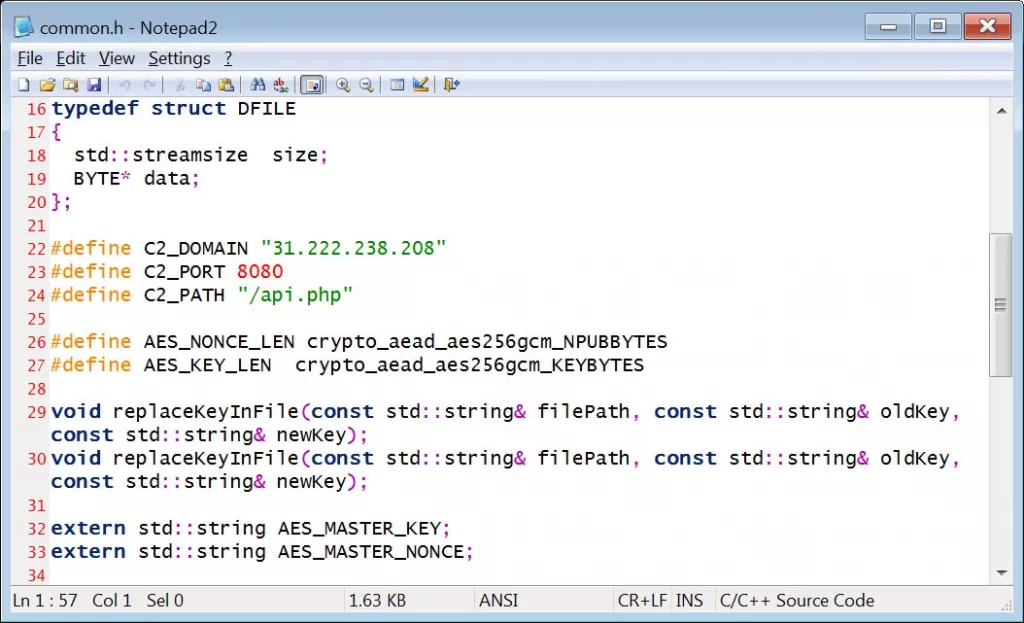
common.h header file used by the builder
Source: BleepingComputer
The builder requires a connection to the affiliate panel (previously located at IP address 31.222.238[.]208) to function correctly. However, since the affiliate panel source code is also included, cybercriminals could replicate or modify the infrastructure to reactivate the ransomware toolkit.
Another Chapter in Builder Leaks
The VanHelsing ransomware source code leak adds to a growing list of ransomware builder disclosures that have significantly impacted the threat landscape. Previous high-profile leaks include:
- Babuk ransomware (June 2021) – Enabled mass attacks against Windows and VMware ESXi environments
- Conti ransomware (March 2022) – Breach led to widespread code reuse among emerging groups
- LockBit ransomware (September 2022) – A disgruntled developer leaked the gang’s builder, which remains in circulation
These ransomware builder leaks allow even low-skilled threat actors to deploy sophisticated ransomware with minimal development effort, further accelerating the proliferation of ransomware-as-a-service operations.