Proofpoint research has revealed that the Bumblebee malware has resurfaced after being absent from the cyber threat landscape for four months.
The new Bumblebee malware campaign, observed in February 2024, employed a distinctly different attack chain compared to previous instances of Bumblebee malware attacks.
Interestingly, the reappearance of Bumblebee aligns with the return of several well-known threat actors at the beginning of 2024, following a temporary period of reduced activity known as the “Winter lull.”
Bumblebee Malware Attacks Using a Sophisticated Downloader to Drop Payloads
From March 2022 to October 2023, multiple threat actors frequently employed the Bumblebee malware. Over this timeframe, Proofpoint’s research identified a total of 230 Bumblebee malware campaigns.
This sophisticated downloader serves as an initial access broker, facilitating the download and execution of additional payloads like Cobalt Strike, shellcode, Sliver, and Meterpreter.
To distribute Bumblebee, threat actors have utilized various creative methods. For instance, in April 2023, Secureworks reported instances where popular software tools such as Zoom, Cisco AnyConnect, ChatGPT, and Citrix Workspace were trojanized to infect unsuspecting victims.
The Bumblebee Malware Campaign Targeted Organizations in the US
According to Proofpoint, Bumblebee was no longer detected in October 2023. However, in February 2024, a new campaign emerged with the aim of distributing the malware.
The attackers employed social engineering techniques to lure targets into downloading Bumblebee. In this particular campaign, several thousand emails were sent from the address “info@quarlesaa[.]com” to organizations in the United States. The subject line of these emails was “Voicemail February.”
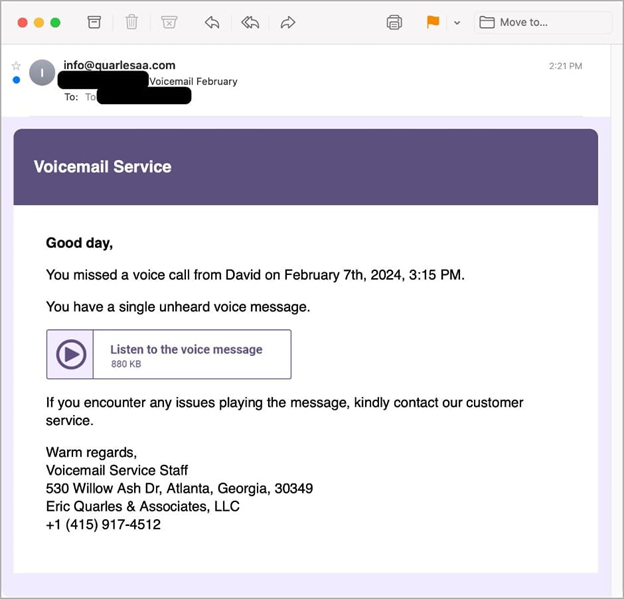
Phishing email spreading Bumblebee
Source: Proofpoint
The emails included OneDrive URLs that directed recipients to a Word file titled “ReleaseEvans#96.docm” and impersonated the consumer electronics company Humane. These Word documents utilized macros to generate a script in the Windows temporary directory, and the dropped file was executed using the “wscript” command.
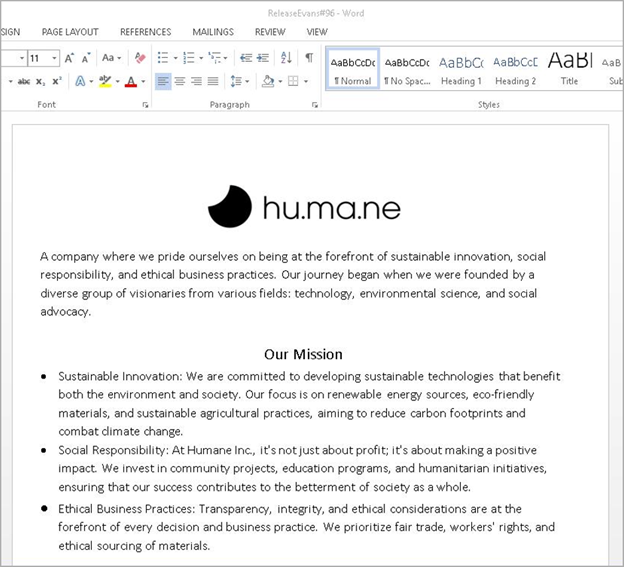
Bogus document containing the VBA macro
Source: Proofpoint
Within the dropped temporary file, there was a PowerShell command that retrieved and executed the subsequent stage of the attack chain from a remote server. This next stage involved another PowerShell command stored in a file named “update_ver,” which proceeded to download and execute the Bumblebee DLL.
Bumblebee Campaigns Can Be Distinctly Identified
The researchers underscored several distinctive attributes associated with this fresh Bumblebee campaign. One notable aspect was the utilization of VBA macro-enabled documents in the attack chain. Proofpoint highlighted that the majority of cybercriminal threat actors have significantly reduced their use of VBA documents.
Earlier Bumblebee malware campaigns employed various tactics such as combining URLs and attachments, as well as exploiting vulnerabilities to carry out their attacks.
Threat Actors Resume Bumblebee Campaigns After the Winter Break
While Proofpoint has not been able to definitively attribute the new campaign to a specific tracked threat actor, the researchers did observe that certain techniques employed, such as the voicemail lure theme and the use of OneDrive URLs, align with the past activities of the TA579 group.
The blog post also highlighted that several tracked threat actors have resumed their activities after a period of absence towards the end of 2023. For example, TA577 reemerged in late January to distribute the Qbot malware after being inactive for about a month from mid-December.
“2024 has started off with a bang for cybercriminal threat actors, with activity returning to very high levels after a temporary winter lull. Proofpoint researchers continue to observe new, creative attack chains, attempts to bypass detections, and updated malware from many threat actors and unattributed threat clusters,”The researchers wrote.