New SentinelOne Ransomware Attack Bypasses EDR via Installer Exploit
Security researchers from Aon’s Stroz Friedberg Incident Response team have uncovered a “Bring Your Own Installer” EDR bypass technique that was used in a real-world ransomware attack to disable SentinelOne’s tamper protection.
The method allowed threat actors to terminate EDR services during the agent upgrade process, exposing devices to Babuk ransomware deployment. This discovery emerged during an incident response engagement earlier in 2025.
How the “Bring Your Own Installer” Bypass Works
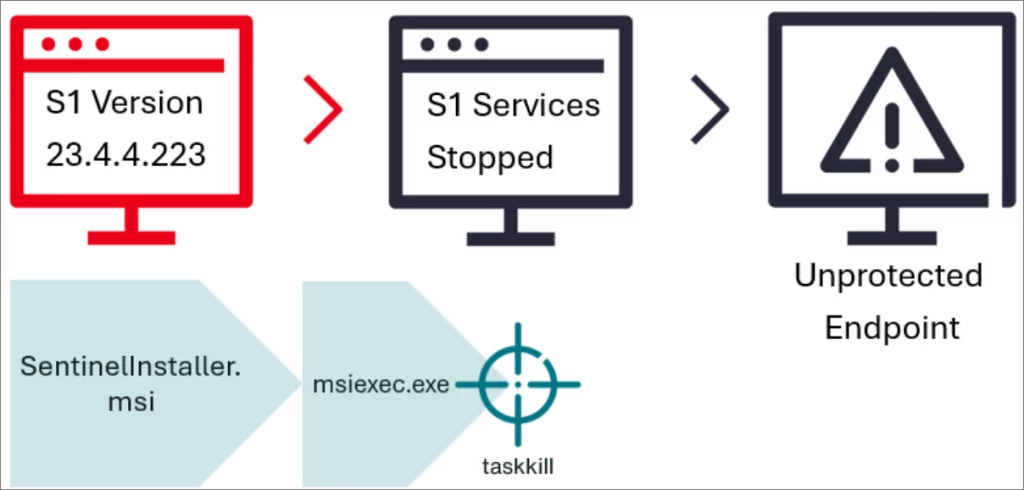
Unlike traditional EDR bypass techniques that rely on third-party tools or drivers, this method abuses the legitimate SentinelOne Windows Installer.
When an agent is upgraded, the SentinelOne installer automatically stops running services to overwrite files. Attackers exploit this window by launching a real installer and then forcefully terminating the installation after the services are disabled — but before the new version is installed. This leaves the device without active protection.
The attack does not require specialized tools, making it accessible to adversaries with admin access.
“We want to get the word out to ensure SentinelOne’s customers know to enable Local Upgrade protection,”
— John Ailes, Manager, Stroz Friedberg DFIR
Bring Your Own Installer EDR bypass attack chain
Source: Stroz Friedberg
Exploited in Live Ransomware Incident
Logs from a breached environment showed that attackers gained administrative access through a separate vulnerability, then executed this bypass technique to disable protections and deploy ransomware.
“Further testing showed that the attack was successful across multiple versions of the SentinelOne agent,”
— Stroz Friedberg
Even fully updated systems remain vulnerable if Online Authorization is not enabled. Once the installer is terminated mid-process, the device also drops offline from the SentinelOne management console, limiting visibility.
SentinelOne’s Response and Mitigation Recommendations
Stroz Friedberg privately disclosed the vulnerability to SentinelOne in January 2025. SentinelOne later notified customers and recommended enabling the “Online Authorization” setting, which requires console approval before any local agent upgrade, downgrade, or uninstall.
This protection is not enabled by default for existing customers, but it is now activated by default in new installations.
“While such local access poses similar threats to anti-tampering for these EDR products at large… we have no knowledge of any EDR vendor, including SentinelOne, that is currently impacted by this attack when their product is properly configured.”
— SentinelOne statement
SentinelOne also confirmed:
- The local agent passphrase is enabled by default to block unauthorized uninstalls.
- The Local Upgrade Authorization (a.k.a. “Online Authorization”) is available to authenticate agent changes.
- The attack can be prevented if either 1a or 1b protection is active.
Other EDR Vendors Alerted
SentinelOne shared the findings with other major EDR vendors as a precaution. Palo Alto Networks confirmed that its products are not affected.
As of now, SentinelOne has not named any other vendors potentially impacted by this technique. BleepingComputer has reached out to the company for further comment.
Summary
This Bring Your Own Installer technique poses a serious risk by exploiting a normal part of EDR software behavior. Organizations using SentinelOne should verify that Online Authorization or Local Upgrade protection is enabled to block unauthorized tampering during upgrades. Without it, even updated agents may remain vulnerable to attack.