In the world of ethical hacking and penetration testing, few tools have stood the test of time quite like Cain and Abel. Originally developed for Windows, Cain and Abel is a powerful password recovery and network sniffing tool designed to help security professionals identify vulnerabilities before cybercriminals can exploit them.
From LAN password recovery to ARP poisoning and cryptanalysis capabilities, this free but robust software has become a go-to utility for penetration testers and network administrators seeking to improve their organization’s defenses.
“Think of Cain and Abel as a Swiss Army knife for ethical hackers — versatile, efficient, and capable of exposing weak points in your security.”
While Cain and Abel has a somewhat controversial reputation because it can also be used maliciously, in the hands of a certified cybersecurity specialist, it serves as a legitimate tool for penetration testing, MITM (Man-in-the-Middle) attack simulations, and password hash cracking to strengthen defenses against real-world cyber threats.
The beauty of Cain and Abel lies in its multi-functional design — it can recover passwords using brute force attacks, dictionary attacks, and cryptanalysis, as well as perform protocol analysis on HTTP, FTP, and SMTP traffic. With features like VoIP sniffing, wireless key recovery, and hash decoding, it remains a relevant addition to any cybersecurity toolkit, especially for training, research, and ethical testing.
Core Functionalities of Cain and Abel
Cain and Abel stands out in the cybersecurity toolkit because of its versatility in password recovery and network security testing. While its reputation often precedes it as a hacking tool, it is also extensively used by penetration testers, ethical hackers, and cybersecurity specialists to identify weaknesses before malicious actors exploit them. Let’s break down its key capabilities in detail.
Password Cracking Capabilities
Cain and Abel is widely known for its password cracking efficiency, supporting various techniques such as:
- Dictionary Attacks – The tool runs through large wordlists to guess passwords, making it useful for testing weak password policies in corporate networks.
- Brute-Force Attacks – Cain and Abel systematically tries all possible combinations of characters until the correct password is found, ideal for identifying weak or default credentials.
- Cryptanalysis Attacks – The software can break password hashes using precomputed tables (also known as Rainbow Tables) to speed up the cracking process.
- Decoding Passwords – It can reveal passwords stored in cache, hidden in Windows Protected Storage, or saved in network authentication protocols.
By combining these methods, Cain and Abel provides comprehensive password recovery testing to evaluate an organization’s resilience against credential-based attacks.
Network Traffic Analysis
Another standout feature is its ability to sniff and analyze network traffic. This is critical in penetration testing because it allows cybersecurity specialists to see what data is traveling across the network in cleartext.
- ARP Spoofing – Cain and Abel can position itself as a “man-in-the-middle” to intercept traffic between devices. This helps test whether encryption protocols (like HTTPS) are properly enforced.
- Packet Capture – The tool records and decodes packets in real time, enabling testers to analyze protocols such as HTTP, FTP, POP3, IMAP, and SMB.
- VoIP Conversation Sniffing – It can capture and reconstruct Voice over IP conversations, which is crucial when assessing secure communication channels.
In professional use, these features help identify unsecured protocols and data leakage risks that might be invisible to regular security scans.
Password Hash Recovery & Decryption
Cain and Abel’s hash recovery abilities make it a staple in ethical hacking labs and cybersecurity training environments. It supports recovery for various hash algorithms, including:
- LM & NTLM Hashes (Windows authentication systems)
- MD5, SHA-1, and SHA-256 Hashes
- MySQL, Oracle, and Cisco Hashes
The tool can extract password hashes from Windows systems or network authentication exchanges and then attempt to crack them using dictionary, brute-force, or cryptanalysis attacks. This helps security teams verify the strength of stored credentials and implement stronger hashing algorithms if weaknesses are found.
Routing Protocol Exploitation
Cain and Abel isn’t just about cracking passwords — it can also manipulate routing tables and sniff routing protocol updates. This allows penetration testers to simulate network redirection attacks, highlighting the need for secure routing authentication in enterprise environments.
Cryptanalysis and Decoding Tools
In addition to password attacks, Cain and Abel provides several data decoding utilities, including:
- Base64 Decoding
- Hexadecimal Conversion
- Unix Password File Cracking
- Windows Key Decoding (product keys and license information)
These tools allow security analysts to reverse-engineer stored data to ensure sensitive information is properly encrypted before deployment.
💡 Pro Tip for Cybersecurity Specialists
While Cain and Abel is a powerful penetration testing tool, using it outside of authorized environments can lead to serious legal consequences. Always ensure you have written permission before engaging in any form of network sniffing or password recovery tests.
How Cain and Abel Works — A Professional, Non-Actionable Overview (for Authorized Testing)
Cain & Abel is a Windows-based toolkit that bundles multiple offensive techniques into a single GUI. For defenders and authorized penetration testers, the value of Cain & Abel is in emulation and diagnostics: it reproduces the attacker behaviors your SOC, EDR, and network defenses should detect and contain.
Below I describe the key workflows you would simulate under authorization, how to interpret tool outputs, and — crucially — how blue teams should detect, monitor, and mitigate the same behaviors.
1) Packet Capture & Network Analysis — Conceptual Workflow and Expected Output
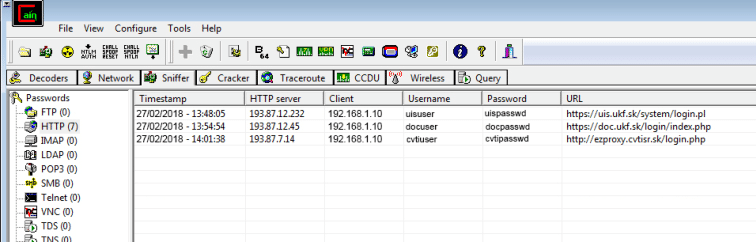
What the feature does:
Cain & Abel includes a packet-sniffer component that captures Layer-3/Layer-4 network traffic for analysis. In authorized testing, this is used to discover unencrypted credentials, misconfigured services, and cleartext protocol leaks (e.g., legacy protocols or misconfigured services).
What to set up in an authorized lab:
- Isolated virtual network with Windows/Linux guests (no internet).
- One or more services configured to use intentionally weak configurations (for training): HTTP, FTP, or an intentionally misconfigured SMTP server.
- Test user accounts with known passwords (lab-only).
- A logging server or PCAP archive location where captured network traffic will be stored.
What you’ll observe (sanitized example output):
- A PCAP record showing
POST /loginwith an unencryptedusername=alice&password=Password123in HTTP payload (sanitized). - A list of network conversations and timestamps, e.g.: rubyCopyEdit
10.0.0.5:80 -> 10.0.0.10:49712 [HTTP] "POST /login" 10.0.0.5:21 -> 10.0.0.12:50102 [FTP] "USER alice"
How defenders interpret this:
- Presence of credentials in plaintext indicates need for TLS/HTTPS enforcement.
- Repeated connections from one host to many endpoints may indicate scanning/MITM and must be investigated.
Blue-team detection & mitigation guidance:
- Monitor for cleartext credential submissions with network IDS signatures (Suricata/Bro/Zeek rules that look for
username=orpassword=in POST bodies). - Enforce TLS across all web endpoints; implement HSTS.
- Use network segmentation and deny east/west traffic between client subnets unless required.
2) ARP Table Manipulation / MITM Emulation — What It Simulates and Defensive Signals
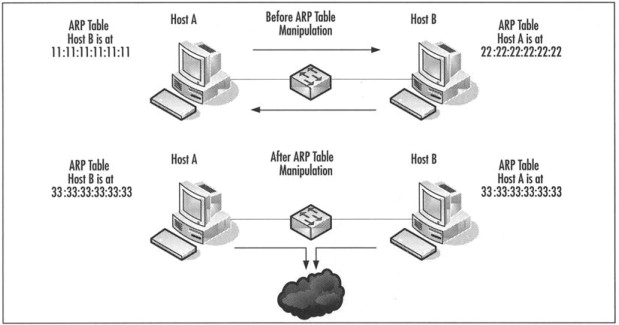
What the feature simulates (conceptual):
Cain & Abel can emulate man-in-the-middle (MITM) scenarios commonly performed via ARP cache poisoning or similar techniques in a flat LAN environment. The goal in a test is to confirm whether such interception would allow credential capture or session hijacking.
Authorized lab setup (high level):
- A flat VLAN with a few hosts plus a test “attacker” VM.
- Instrumented endpoints with endpoint logging enabled (EDR).
- Packet capture for the experiment (PCAP) stored centrally.
Sanitized example observations:
- Duplicate ARP replies; multiple hosts reporting the same MAC for a gateway address (logged).
- Unexpected change in MAC-to-IP mapping in DHCP/ARP tables.
How defenders detect this behavior:
- ARP cache anomalies: entries that flip MAC addresses for a given IP.
- IDS/IPS alerts for ARP spoofing patterns.
- Unusual gratuitous ARP packets from a host that isn’t the gateway.
Mitigations and hardening:
- Deploy DHCP snooping and Dynamic ARP Inspection on switches (Cisco, Juniper, etc.).
- Use static ARP entries for critical hosts where feasible.
- Monitor for gratuitous ARP and trigger automatic quarantine of suspicious hosts.
3) Credential Harvesting & Hash Extraction
What the tool emulates:
Cain & Abel can extract credential artifacts and password hashes that exist in memory, on disk caches, or within captured network authentication flows. In a lab, testers validate whether credential storage mechanisms are secure.
Authorized lab setup:
- A Windows VM configured to run an authentication flow (e.g., RDP login, SMB auth).
- Pre-seeded test accounts whose hashes are known to the tester.
- Logging/EDR agents installed to observe memory and process behaviors.
Sanitized sample outputs you’d review:
- Hash table entries (displayed as
NTLM: 32charhash) with a timestamp and source host. - A list of captured authentication exchanges showing which protocol was used and whether it was encrypted.
Defender takeaways:
- Detect processes that access authentication stores or read LSASS-like memory space (EDRs can flag these behaviors).
- Ensure credentials are not stored in cleartext by applications; verify use of secure credential vaults (e.g., Windows DPAPI, Azure Key Vault).
Remediations:
- Enforce credential vaulting and rotate service credentials regularly.
- Apply LSA protection, Credential Guard and block suspicious processes from accessing LSASS memory.
4) Password Cracking
Cain & Abel supports dictionary, brute force, and rainbow-table style techniques to evaluate password strength and password storage resilience. In authorized testing, password cracking demonstrates how quickly weak credentials can be recovered.
Lab boundaries and ethics:
- Cracking must be performed only against test accounts or hashes obtained from consenting systems.
- Never run cracking jobs against live production accounts or third-party systems.
What the results show (example, sanitized):
- Password strength metrics: percent cracked from a list of 10,000 hashes = 42%.
- Average crack time under dictionary attack for weak passwords: < 2 seconds.
- Percentage of accounts using default/weak passwords.
How to present findings to stakeholders:
- Provide a table listing password policy coverage, percentage of passwords violating policy, and recommended policy changes (stronger minimum length, password complexity, and blocklist common passwords).
- Suggest technical mitigations: enforce MFA, use password managers, and implement password blacklists.
5) VoIP Analysis — Privacy Testing and Risk Signals
The VoIP analysis capability shows whether voice traffic is sent in the clear and whether credentials for SIP endpoints are exposed.
Authorized tests:
- Run on a lab VoIP PBX with test calls between endpoints.
- Capture RTP/SIP flows and demonstrate whether SRTP or digest authentication is configured.
Sanitized output examples:
SIP REGISTERmessages showingAuthorization: Digest username="testuser"(sanitized).- RTP stream integrity checks showing whether audio is encrypted.
Defender guidance:
- Enforce SRTP and SIP TLS.
- Disable plaintext SIP authentication.
- Monitor SIP registration anomalies and large numbers of call attempts.
6) Storage Password Recovery
Cain & Abel can surface passwords cached in browsers, RDP files, or Windows Protected Storage — showing developers/system owners how their applications might leak secrets.
Lab approach:
- Create sample profiles that store passwords in browser profiles or RDP files (lab only).
- Evaluate whether those secrets are encrypted at rest and if they are recoverable.
Defensive recommendations:
- Use OS-level encryption for user profiles and disk encryption (BitLocker).
- Avoid client-side storage of long-term secrets; use secure vaults (e.g., Managed Identity, Secret Store).
- Harden browsers by disabling password autofill in sensitive environments and enabling profile encryption.
Safe Lab Playbook (High-Level) — What a Professional Test Looks Like
If you’re planning to run authorized Cain & Abel-style tests in a lab, follow a professional, auditable checklist:
- Written Authorization — Signed scope and rules of engagement from owner of the systems.
- Isolated Environment — Use an air-gapped VLAN or local virtual network. No production access.
- Baseline Collection — Record current config, logs, and snapshots before testing.
- Test Accounts — Only use test users and seed known credentials/hashes for analysis.
- Time-boxed Runs — Schedule short, documented windows to reduce impact.
- Comprehensive Logging — Centralize PCAPs, system logs, and EDR telemetry during the test.
- Chain of Custody — Maintain records: who ran what, when, and why.
- Immediate Containment Plan — If unintended impact happens, you must have rollback and restore procedures.
- Detailed Reporting — Include findings, sanitized evidence, timelines, and specific remediation actions.
- Remediation Verification — After fixes, re-test to confirm mitigations worked.
How to Report Findings — Example Structure
Executive Summary:
- Scope: internal LAN credential exposure test
- Key finding: 42% of test accounts had passwords crackable in under 30 seconds; cleartext HTTP auth observed on three web apps.
Technical Findings (sanitized):
Issue 1 — Cleartext Authentication: Unencrypted HTTP credentials captured in PCAPlogin_post_2025_08_01.pcap.Issue 2 — Weak Passwords: 42% of hashes from test accounts cracked using dictionary lists.Issue 3 — ARP Spoofing Vulnerability: Gratuitous ARP traffic detected from a non-gateway host during the test window.
Risk & Impact:
- Credential exposure could enable account takeover and lateral movement, leading to data exfiltration.
Recommendations:
- Enforce TLS (HSTS) for all web apps.
- Enforce password complexity and implement organization-wide MFA.
- Deploy Dynamic ARP Inspection and DHCP Snooping on L2 switches.
- Audit and remove local credential caches; use centralized secret vaults.
Appendices:
- Sanitized screenshots, PCAP excerpts (only non-sensitive parts), log timestamps, and remediation test results.
Detection & Blue Team Response (Practical Tips)
When Cain & Abel-style techniques are used by adversaries, SOCs can detect them by looking for the following signals:
- Network Indicators
- Gratuitous ARP packet anomalies.
- Sudden increase in ARP requests or identical IP claimed by multiple MAC addresses.
- Unusual numbers of DNS queries or HTTP POSTs with embedded credentials.
- Endpoint Indicators
- Processes attempting to read protected memory or access LSASS/DPTA records.
- New local services or scheduled tasks created outside change windows.
- Authentication & Directory
- Atypical login times and anomalous source IPs for admin accounts.
- Spike in failed authentication attempts or account lockouts.
Immediate SOC playbook actions:
- Isolate the suspected host (network quarantine).
- Preserve volatile evidence: memory dump, PCAPs, and EDR artifacts.
- Rotate credentials for any affected accounts and force MFA resets.
- Engage incident response and legal/compliance if PII or regulated data was involved.
Alternatives & Defensive Tools You Can Use (Legal, Non-Actionable)
If your goal is to evaluate defenses or teach, consider these safer, defensible tools and techniques:
- Wireshark for packet analysis (network defenders use it to inspect traffic safely).
- Zeek (Bro) and Suricata for network detection/intrusion signatures.
- Active Directory audit tools (bloodhound, AD ACL review) for privilege mapping (authorized only).
- Password policy testing using controlled, internal tools and enterprise password-policy enforcement.
- EDR and L3 switch hardening for runtime protection.
Ethical and Legal Considerations of Cain and Abel
The Cain and Abel password recovery tool is a double-edged sword in the cybersecurity landscape. On one hand, it’s a legitimate, powerful utility for penetration testers, network administrators, and digital forensics experts; on the other, it’s a tool that can be abused for malicious hacking, credential theft, and unauthorized data access.
Because of this dual nature, professionals must approach its usage with strict adherence to ethical guidelines, legal frameworks, and industry best practices. Below is a deep dive into the ethical boundaries and legal responsibilities when working with Cain and Abel.
1. Legal Boundaries: Know the Law Before You Launch the Tool
Cain and Abel’s capabilities—like network packet sniffing, brute-force attacks, ARP poisoning, and VoIP conversation recording—can easily violate privacy laws and cybercrime regulations if used without authorization.
- United States: Unauthorized access to systems, even for “testing,” is prohibited under the Computer Fraud and Abuse Act (CFAA). Penalties can include hefty fines and imprisonment.
- United Kingdom: The Computer Misuse Act 1990 makes it illegal to access or interfere with any computer system without permission.
- European Union: Under the GDPR, intercepting personal data without consent can lead to multi-million euro fines.
- Cybersecurity Law of the People’s Republic of China – China
- Other jurisdictions: Many countries have adopted similar laws criminalizing unauthorized use of hacking tools.
Bottom line: Always have explicit written consent from the system owner before using Cain and Abel in any environment.
2. Ethical Usage in Cybersecurity Testing
For penetration testers and red teams, Cain and Abel can be ethically deployed in controlled environments to identify vulnerabilities such as weak passwords, outdated hashing algorithms, or insecure protocols.
Best practices include:
- Limiting tests to approved targets only.
- Documenting every step of the testing process.
- Reporting vulnerabilities immediately and confidentially to the client or system owner.
Example:
If you are hired by a bank to test employee credential security, you may use Cain and Abel to sniff network traffic and recover NTLM hashes during the engagement. The findings would then be compiled into a penetration testing report outlining remediation steps.
3. Real-World Scenarios: Ethical vs. Unethical Use
| Scenario | Ethical | Unethical |
|---|---|---|
| Using Cain and Abel in a lab network you control for training | ✅ | ❌ |
| Testing your company’s network with management approval | ✅ | ❌ |
| Capturing passwords over a public Wi-Fi hotspot without consent | ❌ | ✅ |
| Conducting phishing simulations on employees with pre-approved scope | ✅ | ❌ |
4. Chain of Custody and Evidence Handling
In digital forensics work, Cain and Abel may be used to recover credentials or decrypt stored data on seized devices. In these cases:
- Maintain a chain of custody to ensure evidence is admissible in court.
- Document hash recovery processes with time stamps, screenshots, and logs.
- Avoid altering original data—use forensic images of drives instead.
5. Industry Certifications and Ethical Codes of Conduct
Cybersecurity professionals using Cain and Abel often hold certifications that require strict adherence to ethical standards, such as:
- Certified Ethical Hacker (CEH) – Abides by EC-Council’s Code of Ethics.
- Offensive Security Certified Professional (OSCP) – Requires responsible disclosure.
- GIAC Penetration Tester (GPEN) – Focuses on lawful and ethical penetration testing.
- (ISC)² Code of Ethics
- EC-Council Code of Ethics
- SANS Security Code of Ethics
Violating these codes could lead to loss of certification and reputation damage.
Key Takeaway
Cain and Abel is not inherently “good” or “bad”—its morality lies in how it is used. In professional contexts, it is a legitimate penetration testing and password recovery tool; in malicious hands, it is a cybercrime enabler.
Golden Rule: If you wouldn’t want your own data recovered or intercepted without permission, don’t use Cain and Abel that way on someone else’s systems.
Best Practices for Using Cain and Abel Responsibly
Using Cain and Abel effectively and ethically requires a disciplined, security-focused approach. The same capabilities that make it powerful for penetration testing can also cause serious harm if misused. Cybersecurity professionals should integrate the following best practices into their workflow to ensure compliance, accuracy, and professional integrity.
1. Always Obtain Written Authorization
Before launching Cain and Abel on any network or system, secure a signed authorization from the system owner. This ensures your activities are legally covered and align with penetration testing contracts or red team engagements. For example:
- In a corporate security test, your scope agreement might specify only password cracking from dumped Active Directory hashes, not live ARP poisoning on production systems.
- The written scope should clearly mention what modules in Cain and Abel can be used—e.g., “Dictionary-based NTLM cracking” or “SSL MITM testing in lab environment.”
2. Isolate Testing Environments
Cain and Abel should ideally be run inside controlled lab environments or isolated VLANs. Using virtualized environments (VMware, VirtualBox) ensures you don’t unintentionally disrupt production services.
- Example: Run Cain and Abel against a cloned Active Directory lab setup to test NTLMv2 cracking without exposing sensitive company data.
- Maintain separate VM snapshots for pre- and post-testing states so you can revert changes quickly.
Tools like VirtualBox or VMware Workstation let you simulate corporate network environments with multiple virtual machines acting as clients, servers, and routers.
Example Lab Setup:
- VM1: Windows Server 2016 (Domain Controller)
- VM2: Windows 10 Client
- VM3: Attacker machine with Cain and Abel installed
- All connected via an internal-only virtual network to avoid leaking any packets to the internet.
3. Prefer Dictionary and Hybrid Attacks Before Brute Force
Cain and Abel supports multiple cracking methods (dictionary, brute force, cryptanalysis via rainbow tables). A responsible approach is to:
- Start with targeted dictionary lists relevant to the organization (e.g., company name variations, seasonal passwords).
- Use hybrid modes to append numbers/symbols.
- Only escalate to brute force when necessary to avoid excessive computation and time wastage.
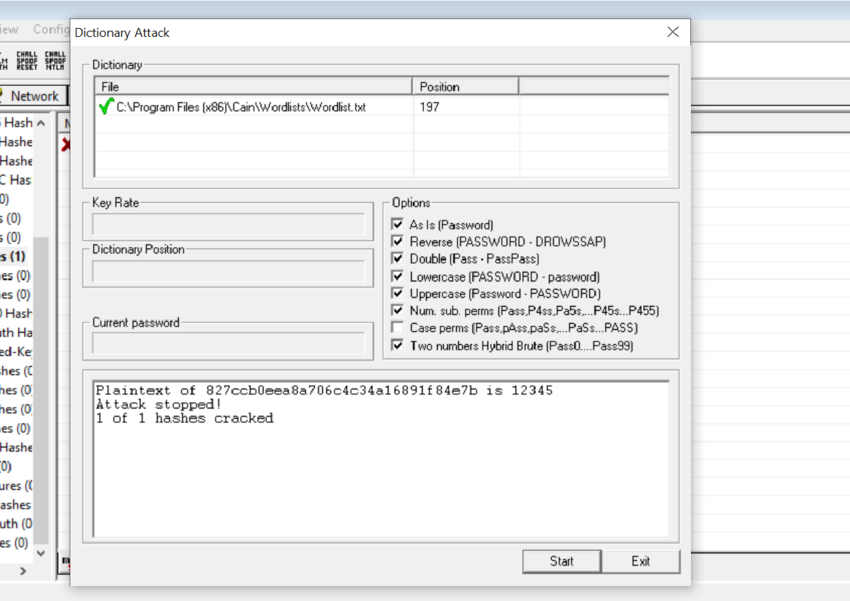
Example Dictionary Attack Command in Cain and Abel:
Select "Cracker" → "LM & NTLM Hashes" → Add hashes → Right-click → Dictionary Attack → Select wordlist.txt
4. Monitor for Collateral Network Impact
Certain Cain and Abel features, such as ARP poisoning, can degrade network performance if misconfigured.
- Run tests during low-traffic hours or in a dedicated subnet.
- Use the “Sniffer → Stop” button immediately if packet loss or delays spike.
5. Limit ARP Poisoning Campaigns
ARP poisoning is one of Cain and Abel’s most widely used features, but it can also disrupt legitimate traffic.
- Use filters in Cain and Abel’s Sniffer tab to target only specific IP pairs you’re authorized to monitor.
- Example: Instead of poisoning the entire subnet (
192.168.1.0/24), narrow the scope to192.168.1.50(workstation) and192.168.1.10(server). - Monitor packet loss and network latency in real-time to ensure your actions aren’t degrading performance.
6. Securely Store and Destroy Recovered Credentials
Recovered passwords, hashes, and keys should be stored encrypted at rest (e.g., VeraCrypt, BitLocker) and destroyed securely after engagement.
- Maintain a password evidence log for reporting but redact sensitive content in the final client report.
- Use secure deletion tools such as sdelete.exe for wiping temporary files.
7. Stay Updated on Legal Jurisdictions
Laws differ widely on password cracking and network sniffing.
- In the US, Cain and Abel usage without permission can violate the Computer Fraud and Abuse Act (CFAA).
- In the UK, it can breach the Computer Misuse Act 1990.
- In EU countries, GDPR may classify certain recovered passwords as personal data, invoking strict handling rules.
8. Regularly Update and Validate Tool Integrity
Since Cain and Abel is no longer actively maintained, there are risks of using outdated binaries or modified versions containing malware.
- Download only from reputable sources.
- Verify the checksum (MD5/SHA256) before running the executable.
- Consider running it in a dedicated penetration testing VM with no persistent credentials to limit the impact of potential compromise.
9. Integrate Cain and Abel with a Larger Testing Strategy
Cain and Abel shouldn’t be the only tool in your arsenal.
- Pair it with tools like Wireshark for packet analysis, Hashcat for GPU-accelerated password cracking, and Metasploit for exploitation.
- Example: Cain and Abel can dump NTLM hashes from a Windows machine, which you then import into Hashcat for faster brute force attacks.
💡 Pro Tip for Professionals:
Create custom attack profiles within Cain and Abel with preconfigured settings tailored to specific test scenarios. This minimizes accidental misuse and speeds up engagements.
Common Mistakes When Using Cain and Abel
While Cain and Abel is powerful, even experienced penetration testers and cybersecurity professionals can make costly errors when deploying it. These mistakes can lead to inaccurate results, wasted time, or—worse—unintentional legal violations.
1. Running Cain and Abel Without Proper Authorization
Mistake: Using Cain and Abel on a live corporate network without written permission.
Example:
A junior pentester runs ARP poisoning during a training session on a client’s production network, causing temporary service disruptions. This results in the client losing trust and halting the engagement.
Avoidance Tip:
Always have a signed scope of work (SOW) that clearly authorizes Cain and Abel usage on the designated systems.
2. Not Isolating the Test Environment
Mistake: Conducting password recovery tests on a network segment connected to production systems.
Example:
While testing SMB hash cracking, a misconfigured Cain and Abel ARP spoofing session starts affecting unrelated machines, leading to random authentication failures.
Avoidance Tip:
Use an isolated lab environment or a VLAN specifically created for penetration testing to avoid collateral network impact.
3. Over-Reliance on Default Wordlists
Mistake: Using the default Cain and Abel wordlist for dictionary attacks.
Example:
An attacker’s password is “Winter2025!”—which isn’t in Cain’s default dictionary. The pentester misses the hit because they didn’t load a custom wordlist like RockYou.txt or a targeted, company-specific list.
Avoidance Tip:
Integrate external, updated wordlists and augment them with rules-based attacks.
4. Incorrect Configuration of ARP Poisoning
Mistake: Enabling ARP poisoning but forgetting to configure the correct network gateway and target hosts.
Example:
Instead of sniffing credentials between a workstation and the gateway, the tester poisons their own machine’s connection, capturing nothing useful.
Avoidance Tip:
In Cain and Abel:
- Go to Sniffer > APR
- Add both the gateway and the specific target IPs.
- Ensure “APR (ARP Poison Routing)” is enabled before starting.
5. Ignoring Cain’s Event Log
Mistake: Skipping the Event Log tab to check for errors.
Example:
Cain and Abel silently fails to capture any LM/NTLM hashes because the WinPcap driver isn’t running, but the tester doesn’t notice until hours later.
Avoidance Tip:
Regularly check Tools > Event Log in Cain to ensure all modules are working and that no driver/service is failing.
6. Misunderstanding the Hash Cracking Progress
Mistake: Assuming Cain will instantly crack captured hashes.
Example:
A tester tries to brute force a 12-character NTLM hash on a low-power laptop, expecting instant results—it’s still running days later.
Avoidance Tip:
Understand computational limitations:
NTLM Brute Force: ~50 million guesses/sec on average CPU
12-char password: ~3.2 x 10^21 combinations
For heavy cracking, export hashes to tools like Hashcat on GPU rigs.
7. Failing to Save and Backup Captured Data
Mistake: Shutting down Cain without exporting results.
Example:
After hours of sniffing RDP credentials, a tester closes Cain accidentally, losing all session captures.
Avoidance Tip:
Regularly export:
- Passwords (
Passwords > Export) - Sniffer Logs
- APR Captures
8. Not Disabling Cain Properly After Use
Mistake: Leaving ARP poisoning active after testing.
Example:
A consultant finishes their engagement but doesn’t stop Cain’s ARP module, causing intermittent network issues for the client.
Avoidance Tip:
Always go to Configure > Stop APR Poisoning and Stop Sniffer before disconnecting.
💡 Pro Tip: Cain and Abel is a precision tool. Treat it like a loaded firearm—never “leave it running” unattended, and never point it at anything you’re not authorized to test
Alright — let’s wrap this up with a detailed FAQ section for your long-form SEO blog on Cain and Abel.
I’ll make it keyword-rich and ensure it aligns with a cybersecurity professional’s audience while remaining accessible to beginners.
Frequently Asked Questions (FAQ) About Cain and Abel
1. What is Cain and Abel used for in cybersecurity?
Cain and Abel is a password recovery and network analysis tool primarily used by penetration testers and ethical hackers to identify security weaknesses. Its functions include packet sniffing, password cracking, VoIP decoding, network traffic monitoring, and ARP spoofing. In ethical contexts, it’s used to assess system defenses and simulate real-world attack vectors.
2. Is Cain and Abel legal to use?
Yes — but only in authorized environments. Using Cain and Abel without explicit permission from the system owner is illegal under most cybercrime laws (e.g., the Computer Fraud and Abuse Act in the U.S. and the Computer Misuse Act in the U.K.). Ethical cybersecurity professionals use Cain and Abel only in penetration testing engagements, security audits, or lab-based learning environments.
3. How does Cain and Abel capture network passwords?
Cain and Abel can sniff network packets to capture unencrypted passwords transmitted over the network.
Example workflow:
- Select Sniffer tab → enable network adapter.
- Start ARP Poison Routing to intercept packets between a target and gateway.
- Use the Passwords tab to automatically display captured credentials for protocols like FTP, HTTP, POP3, SMB, and Telnet.
4. Can Cain and Abel crack modern passwords?
Yes, but with limitations. Cain and Abel supports:
- Dictionary attacks (testing a predefined wordlist).
- Brute-force attacks (testing all possible combinations).
- Cryptanalysis via Rainbow Tables (very fast lookups for known hashes).
However, strong hashing algorithms with salts (like bcrypt or Argon2) make recovery much slower or infeasible.
5. What are Rainbow Tables in Cain and Abel?
Rainbow Tables are precomputed hash lookup tables used to reverse cryptographic hashes into plaintext passwords. Cain and Abel allows you to:
- Generate your own Rainbow Tables.
- Use existing pre-built tables for popular algorithms like LM, NTLM, and MD5.
Example:
If you have the NTLM hash 32ED87BDB5FDC5E9CBA88547376818D4, Cain and Abel can check against a Rainbow Table to quickly find that the password is password123.
6. Does Cain and Abel work on Windows 10 or 11?
Cain and Abel was primarily developed for older versions of Windows (up to Windows 7). While it can run on newer versions with compatibility settings, driver signing issues and outdated dependencies may limit functionality. Security professionals often run Cain and Abel in a Windows XP or Windows 7 virtual machine for full compatibility.
7. Is Cain and Abel still maintained?
No — Cain and Abel is no longer actively developed. The last stable release was v4.9.56 (around 2014). This means:
- No security patches.
- Possible instability on modern systems.
- Ethical hackers often use Cain and Abel alongside modern tools like Wireshark, Hashcat, or John the Ripper.
8. What are safer, legal alternatives to Cain and Abel?
If you’re looking for up-to-date and supported tools:
- Wireshark – advanced packet analyzer.
- Hashcat – GPU-accelerated password cracker.
- John the Ripper – multi-platform password testing.
- Ettercap – MITM attack framework.
9. Can Cain and Abel recover Windows account passwords?
Yes — Cain and Abel can extract LM and NTLM hashes from the Windows SAM database and attempt to crack them using various attack methods. This is useful in authorized password recovery scenarios, such as when a system admin needs to regain access to an account.
10. Do companies still use Cain and Abel for penetration testing?
Some do — especially in educational and training labs — because it’s an easy-to-understand tool for demonstrating:
- ARP spoofing.
- Password sniffing.
- Man-in-the-middle attacks.
However, many enterprises prefer more modern, maintained tools for professional penetration tests.
Master Cain and Abel Responsibly
Cain and Abel remains one of the most powerful and versatile password recovery tools in the cybersecurity arsenal. Its capabilities—from sniffing network traffic to recovering lost passwords—make it invaluable for penetration testers, network administrators, and ethical hackers.
However, as with any advanced security tool, the difference between legitimate use and malicious intent lies entirely in the operator’s hands. Misuse can result in severe legal repercussions, reputational harm, and even imprisonment. Used correctly, Cain and Abel can help strengthen systems, uncover vulnerabilities before attackers do, and enhance overall security posture.
In the ever-evolving landscape of cyber threats, knowing your tools inside out is crucial. Whether you are simulating real-world attacks for training, performing security audits, or recovering critical credentials in an enterprise setting, Cain and Abel delivers—provided you follow strict ethical guidelines and legal boundaries.
If you’re serious about elevating your penetration testing skills and want to master Cain and Abel alongside other essential cybersecurity tools, start by:
- Setting up a controlled lab environment to practice sniffing, cracking, and recovery techniques.
- Pairing Cain and Abel with Metasploit Framework, Wireshark, and John the Ripper for full-spectrum testing.
- Pursuing cybersecurity certifications like CEH or OSCP to validate your skills and expand your toolkit.
Cybersecurity is a battlefield. Equip yourself, train hard, and always fight on the right side.









