A newly discovered speculative execution attack called VMScape allows a malicious virtual machine (VM) to leak sensitive data from a hypervisor process running on AMD and Intel processors. The attack bypasses existing Spectre mitigations and compromises the trust model of multi-tenant cloud environments.
How VMScape Breaks Guest-Host Isolation
VMScape is designed to target QEMU, a widely used user-mode hypervisor component that maps guest memory into its address space. Researchers from ETH Zurich demonstrated that VMScape can leak cryptographic keys and other secrets without compromising the host operating system or modifying virtualization software.
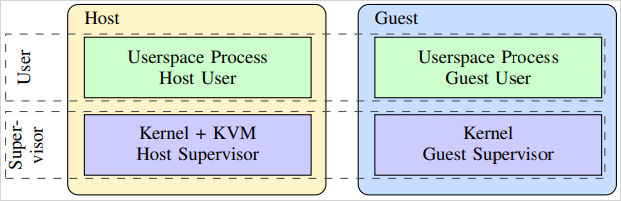
Host to guest separation
Source: ETH Zurich
The attack exploits incomplete isolation in branch prediction units (BPUs) on modern CPUs. While hardware mitigations were added after Spectre to separate guest and host branch prediction, researchers found that shared structures such as the Branch Target Buffer (BTB), Indirect Branch Predictor (IBP/ITA), and Branch History Buffer (BHB) remain vulnerable.
By influencing indirect branch prediction in the host, an attacker can misguide QEMU’s execution flow, triggering a Spectre-BTI (Branch Target Injection) scenario where secret data is speculatively leaked into a shared cache.
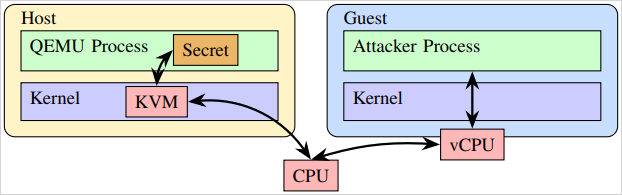
Overview of the attack
Source: ETH Zurich
Technical Details of the Exploit
Researchers used a FLUSH+RELOAD cache side-channel attack to monitor and extract leaked data from the reload buffer. They extended the speculative execution window by carefully evicting cache entries from inside the guest, specifically targeting the Last-Level Cache (LLC) on AMD Zen 4 CPUs.
ASLR (Address Space Layout Randomization), which typically prevents attackers from knowing memory locations, was defeated by probing branch collisions to locate the victim gadget and brute-forcing the virtual address of the reload buffer.
The team reported that VMScape can leak arbitrary memory data from QEMU at:
- 32 bytes per second data exfiltration rate
- 98.7% byte-level accuracy
- 43% overall success rate for a complete attack
At this speed, a 4KB secret, such as a disk encryption key, can be stolen in roughly 128 seconds, with the entire end-to-end attack taking just under 13 minutes when including ASLR bypassing.
Impact on Cloud and Virtualized Environments
The vulnerability affects all AMD processors from Zen 1 through Zen 5 and Intel’s Coffee Lake CPUs, while newer architectures like Raptor Cove and Gracemont remain unaffected.
Cloud environments are particularly at risk because an attacker only needs to rent a virtual machine to mount this attack and potentially extract secrets from the hypervisor or other co-hosted VMs.
Researchers emphasized that while VMScape is powerful, it requires:
- Advanced technical skills
- Careful preparation and tuning
- Sustained execution time to collect meaningful data
This makes it a more realistic threat for targeted attacks against high-value cloud workloads rather than mass exploitation.
Vendor Response and Security Patches
The issue was disclosed to AMD and Intel on June 7, 2025, and has been assigned CVE-2025-40300.
- AMD has released a security bulletin acknowledging the issue.
- Linux kernel developers have deployed a patch that introduces an IBPB (Indirect Branch Prediction Barrier) on VMEXIT, which flushes the branch prediction state whenever switching from guest to host.
- Researchers confirmed that this mitigation has minimal performance impact on common workloads.
Recommendations for Enterprise Security Teams
System administrators and cloud providers should ensure that:
- Hypervisors are updated with the latest kernel patches.
- CPU microcode updates from AMD and Intel are applied.
- Multi-tenant workloads are monitored for unusual cache or CPU branch activity.
These measures will help reduce exposure to speculative execution attacks like VMScape.