A large-scale ad fraud campaign named Scallywag exploited custom-built WordPress plugins to drive 1.4 billion fraudulent ad requests per day. The scheme focused on monetizing pirated content and URL shortening websites that typically lack access to legitimate advertising due to compliance and brand safety concerns.
HUMAN Identifies and Disrupts the Scallywag Ad Fraud Network
The operation was uncovered by bot and fraud detection firm HUMAN, which linked the activity to 407 domains used across the network. Scallywag’s operations have since declined by 95%, following a targeted response by HUMAN and its ad-tech partners.
Despite the takedown, threat actors behind Scallywag continue rotating infrastructure, including domains and redirect mechanisms, to maintain operations.
Four WordPress Plugins Powered the Fraud-as-a-Service Model
The fraud operation was built around four WordPress plugins developed specifically for ad fraud:
- Soralink (2016)
- Yu Idea (2017)
- WPSafeLink (2020)
- Droplink (2022)
These plugins enabled threat actors to monetize low-quality and piracy-focused websites by redirecting traffic through a chain of ad-filled intermediary pages. HUMAN found that multiple actors independently used these tools, some even publishing tutorials online on how to replicate the fraud.
HUMAN stated:
“These extensions lower the barrier to entry for a would-be threat actor who wants to monetize content that wouldn’t generally be monetizable with advertising.”
How the Fraud Scheme Worked
Visitors to piracy catalog sites were presented with shortened URLs linking to movies or premium software. These links redirected users through WordPress blogs running Scallywag plugins, triggering a series of monetized ad impressions.
- Intermediate pages loaded forced interactions such as CAPTCHAs, timers, and cloaked content.
- Redirection chains ended with access to the promised file, making the experience look legitimate.
Notably, many piracy site owners were not part of the Scallywag operation but formed gray partnerships with fraud operators to handle monetization without directly hosting ads themselves.
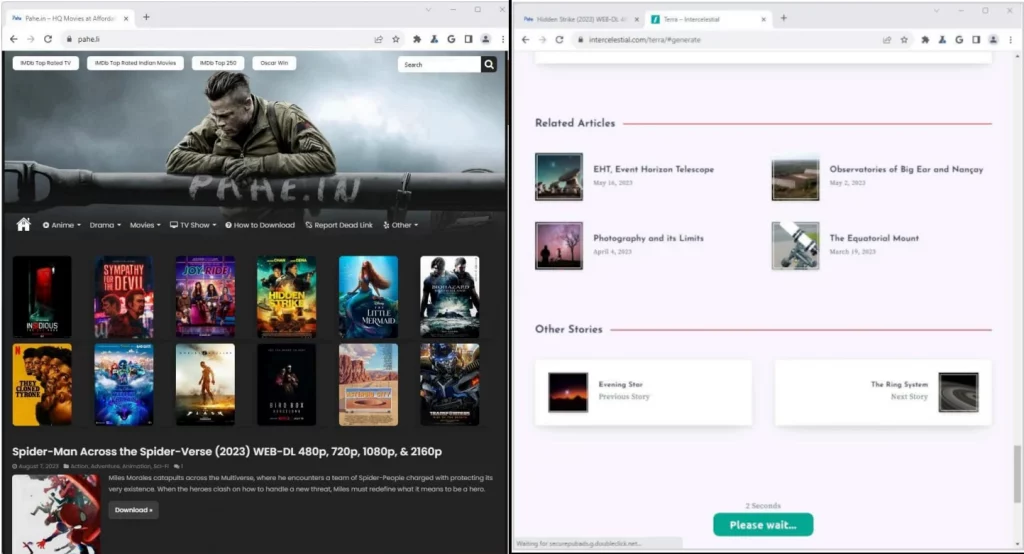
Piracy site (left) linking to Scallywag site (right)
Source: HUMAN
Scallywag’s Traffic Dropped to Near Zero After HUMAN’s Intervention
HUMAN detected irregularities in ad traffic—such as abnormal impression volumes, cloaking, and forced user interaction—through their network of partners. The firm then worked with ad exchanges to block Scallywag requests and cut off its revenue streams.
As fraudsters attempted to adapt by:
- Rotating to new cashout domains
- Using open redirect chains to obfuscate traffic sources
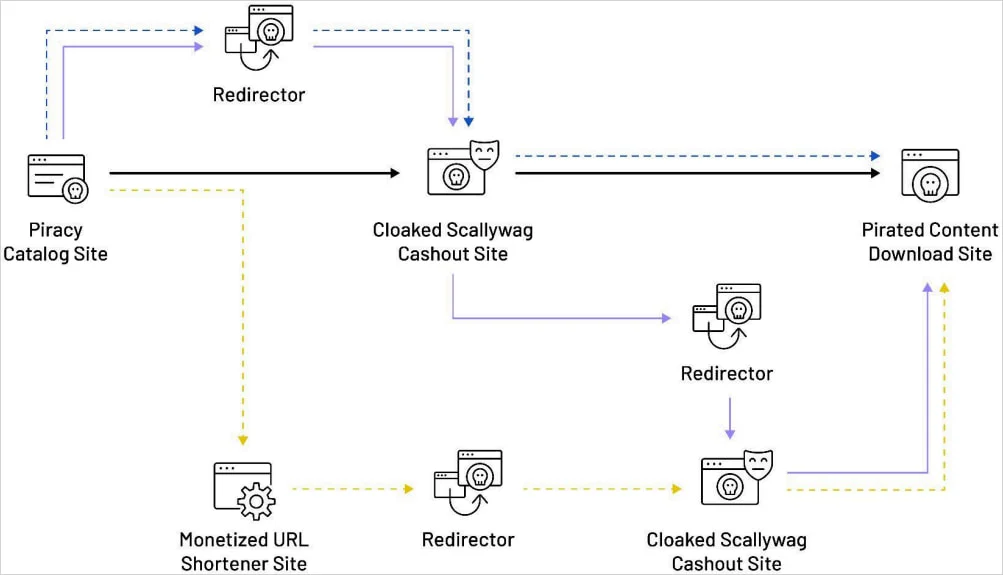
Scallywag’s operational overview
Source: HUMAN
HUMAN’s detection systems adjusted to continue blocking fraudulent activity.
The crackdown forced many affiliates to abandon the scheme, causing a collapse in the Scallywag ad fraud ecosystem.
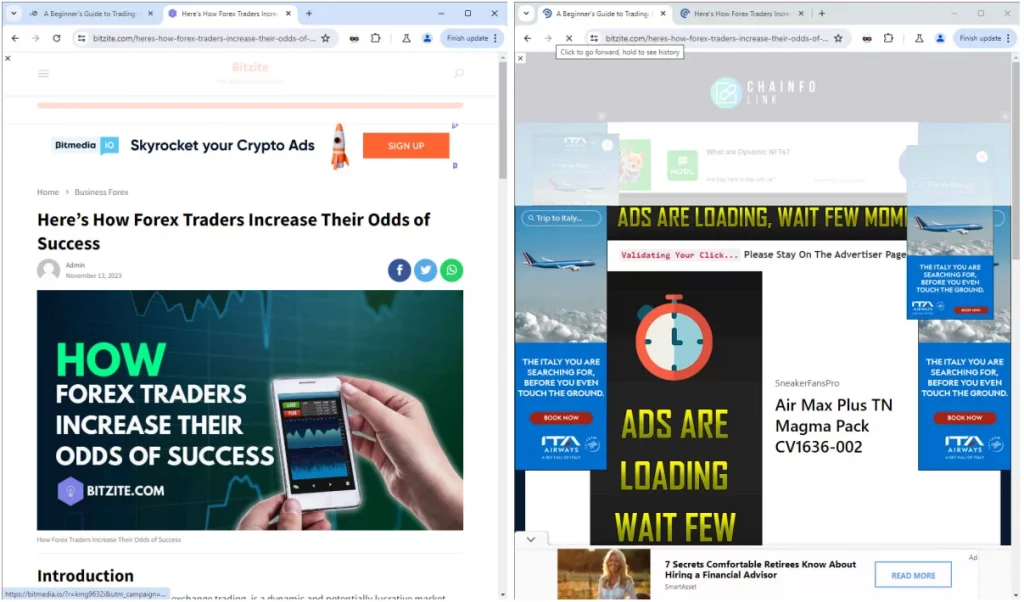
Same site visited directly (left) and visited through URL-shortener (right)
Source: HUMAN
The Threat Remains Despite a Major Disruption
While the economic infrastructure behind Scallywag has been dismantled, HUMAN warned that the actors may continue to adapt and explore new fraud models.
For enterprises, this case highlights the importance of real-time threat intelligence and advertising supply chain visibility to detect and disrupt evolving ad fraud schemes.