The world of cybercrime is a constantly evolving landscape, with new threats emerging at an alarming rate. Ransomware, a particularly insidious form of attack, has become a major concern for businesses of all sizes. The latest threat to emerge is Cicada3301, a ransomware-as-a-service (RaaS) operation targeting VMware ESXi systems with a sophisticated Linux encryptor. This new threat poses a significant risk to enterprise businesses, particularly those heavily reliant on virtualized environments.
Cicada3301 is not just another ransomware operation. It exhibits a level of sophistication and strategic targeting that sets it apart. The group leverages advanced techniques, including the use of Rust programming language, ChaCha20 encryption, and targeted VM shutdown and snapshot-wiping commands. Furthermore, its focus on ESXi environments, the backbone of many enterprise IT infrastructures, highlights its potential to cause widespread disruption and financial damage.
The group has already claimed 19 victims on its extortion portal, demonstrating its rapid and aggressive approach to cybercrime.
Cicada3301: A Potential ALPHV Reboot or Fork
The name “Cicada3301” is a curious choice, referencing a mysterious online puzzle game that ran from 2012 to 2014. While the ransomware operation uses the same logo as the game for promotion, there is no connection between the two. The legitimate Cicada3301 project has issued a statement condemning the ransomware operators’ actions and disavowing any association.
Cicada3301 first began promoting its operation and recruiting affiliates on June 29, 2024, in a forum post on the ransomware and cybercrime forum RAMP. However, there is evidence of Cicada attacks as early as June 6, suggesting the group was already active before attempting to recruit affiliates.
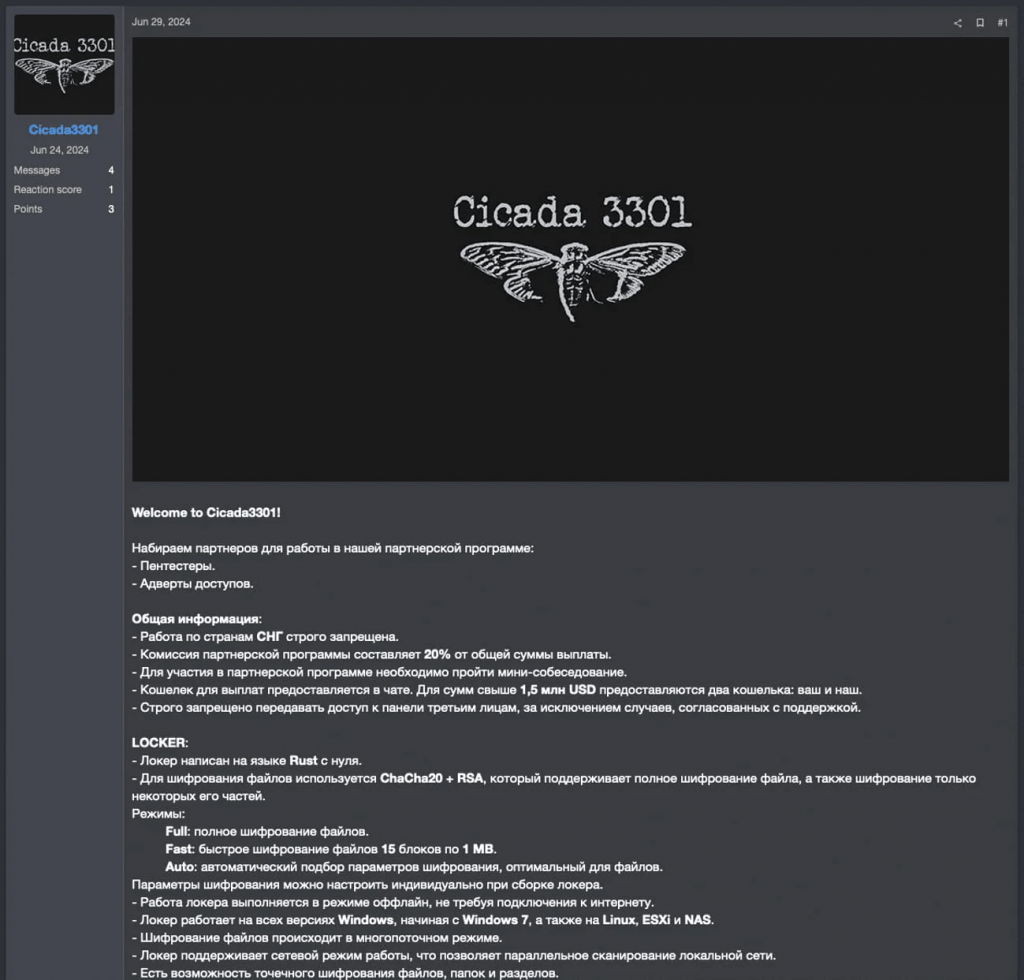
Cicada3301 seeking affiliates on RAMP forums
Source: Truesec
An analysis by Truesec reveals striking similarities between Cicada3301 and ALPHV/BlackCat, a notorious ransomware group. These similarities suggest a possible rebrand or a fork created by former ALPHV core team members.
Here are the key points of resemblance:
- Both are written in Rust.
- Both use the ChaCha20 algorithm for encryption.
- Both employ identical VM shutdown and snapshot-wiping commands.
- Both use the same user interface command parameters, the same file naming convention, and the same ransom note decryption method.
- Both use intermittent encryption on larger files.
It’s worth noting that ALPHV conducted an exit scam in early March 2024, claiming a fake FBI takedown operation after stealing a massive $22 million payment from Change Healthcare from one of their affiliates.
Cicada3301’s Connection to the Brutus Botnet
Truesec has also uncovered evidence suggesting that Cicada3301 may be collaborating with or utilizing the Brutus botnet for initial access to corporate networks. This botnet was previously linked to global-scale VPN brute-forcing activities targeting Cisco, Fortinet, Palo Alto, and SonicWall appliances. The Brutus activity was first observed two weeks after ALPHV shut down operations, further strengthening the link between the two groups in terms of timelines.
Cicada3301’s Linux Encryptor Targets VMware ESXi
Cicada3301 is a Rust-based ransomware operation with both Windows and Linux/VMware ESXi encryptors. Truesec’s analysis of the VMware ESXi Linux encryptor reveals its sophisticated capabilities.
Like BlackCat and other ransomware families such as RansomHub, a special key must be entered as a command line argument to launch the encryptor. This key is used to decrypt an encrypted JSON blob that contains the configuration the encryptor will use when encrypting a device.
Truesec explains that the encryptor verifies the key’s validity by using it to decrypt the ransom note. If successful, the encryption operation proceeds.
The encryptor’s main function (linux_enc) utilizes the ChaCha20 stream cipher for file encryption and then encrypts the symmetric key used in the process with an RSA key. The encryption keys are generated randomly using the ‘OsRng’ function.
Cicada3301 targets specific file extensions matching documents and media files and checks their size to determine where to apply intermittent encryption (>100MB) and where to encrypt the entire file contents (<100MB).
When encrypting files, the encryptor appends a random seven-character extension to the file name and creates ransom notes named ‘RECOVER-[extension]-DATA.txt.’ Notably, BlackCat/ALPHV encryptors also used random seven-character extensions and a ransom note named ‘RECOVER-[extension]-FILES.txt.’
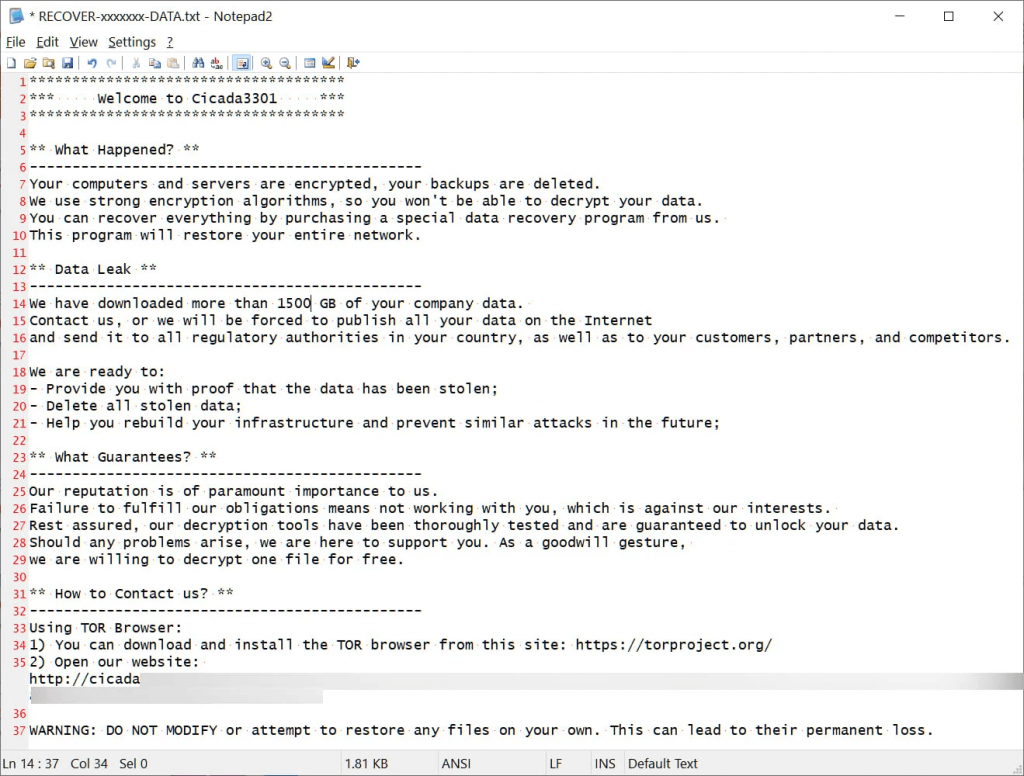
Cicada3301 ransom note
Source: BleepingComputer
The ransomware operators can set a sleep parameter to delay the encryptor’s execution, potentially to evade immediate detection.
A “no_vm_ss” parameter instructs the malware to encrypt VMware ESXi virtual machines without attempting to shut them down first. However, by default, Cicada3301 first uses ESXi’s ‘esxcli’ and ‘vim-cmd’ commands to shut down virtual machines and delete their snapshots before encrypting data.
Here are the commands used to shut down virtual machines and delete snapshots:
esxcli –formatter=csv –format-param=fields==\”WorldID,DisplayName\” vm process list | grep -viE \”,(),\” | awk -F \”\\\”*,\\\”*\” \'{system(\”esxcli vm process kill –type=force –world-id=\”$1)}\’ > /dev/null 2>&1;
for i in `vim-cmd vmsvc/getallvms| awk \'{print$1}\’`;do vim-cmd vmsvc/snapshot.removeall $i & done > /dev/null 2>&1Cicada3301: A Sophisticated Threat with a Focus on ESXi Environments
Cicada3301’s activities and success rate point to an experienced actor who knows what they’re doing, further supporting the hypothesis of an ALPHV reboot or at least the utilization of affiliates with prior ransomware experience.
The new ransomware’s focus on ESXi environments highlights its strategic design to maximize damage in enterprise environments, which many threat actors now target for lucrative profits. By combining file encryption with the ability to disrupt VM operations and remove recovery options, Cicada3301 ensures a high-impact attack that affects entire networks and infrastructures, maximizing the pressure placed on victims.
This new ransomware operation poses a serious threat to businesses and organizations that rely on VMware ESXi systems. It is crucial for organizations to take proactive steps to protect their systems from these attacks, including:
- Regularly updating their ESXi systems with the latest security patches.
- Implementing strong access controls and multi-factor authentication.
- Maintaining regular backups of critical data and systems.
- Developing a comprehensive incident response plan.
By taking these steps, organizations can significantly reduce their risk of falling victim to ransomware attacks like Cicada3301.
Conclusion
The emergence of Cicada3301 underscores the relentless evolution of cyber threats. This ransomware operation, with its focus on ESXi environments, highlights a shift in tactics, targeting critical infrastructure and maximizing disruption. Enterprise businesses must remain vigilant and proactively strengthen their security posture to mitigate the risk of falling victim to such attacks.









