A new Linux backdoor, dubbed “Auto-Color,” is targeting government organizations and universities. Researchers at Palo Alto Networks’ Unit 42 discovered the malware. It was active between November and December 2024. The Auto-Color Linux Backdoor malware attacks have affected North America and Asia.
Understanding the Auto-Color Linux Backdoor Threat
Auto-Color is highly evasive. It’s difficult to remove and can maintain access for long periods. The malware shares some similarities with Symbiote Linux malware. However, they are distinct.
Infection Chain and Methods
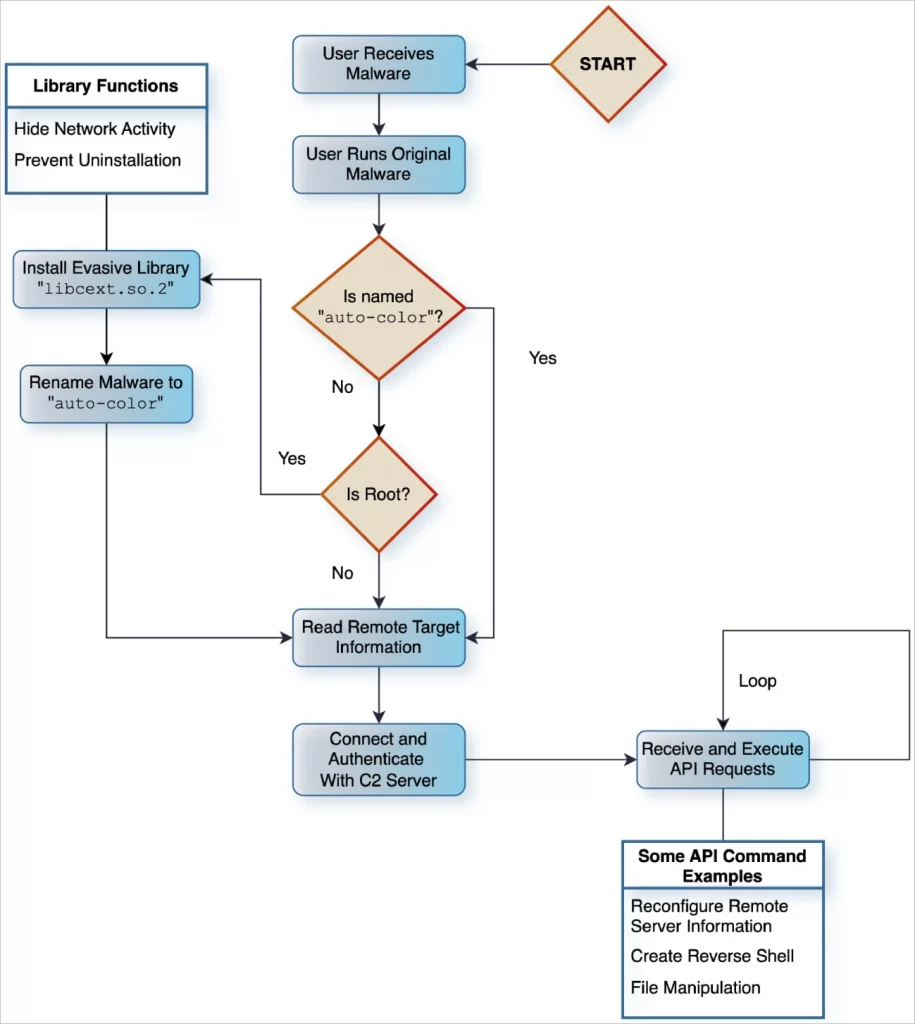
Auto-Color infection chain
Source: Unit 42
The initial infection vector is unknown. The attack starts with a file. These files have benign names. Examples include “door,” “egg,” and “log.”
If the malware runs with root privileges, it installs a malicious library. This is libcext.so.2. It disguises itself as the legitimate libcext.so.0 library, then copies itself to /var/log/cross/auto-color. It modifies /etc/ld.preload to ensure the implant runs before other system libraries.
Without root access, Auto-Color still executes. It skips persistent mechanisms. This limits its long-term impact. It still provides remote access and attackers might gain root access through other means.
Auto-Color’s Functionality and Evasion Techniques
Auto-Color decrypts command-and-control (C2) server information. It uses a custom encryption algorithm. A random 16-byte value handshake validates the exchange.
Custom encryption is used to obfuscate C2 server addresses. It also obfuscates configuration data and network traffic. The encryption key changes dynamically. This makes detection harder.
After establishing a connection, the C2 can order Auto-Color to:
- Open a reverse shell for full remote access.
- Execute arbitrary commands.
- Modify or create files to expand the infection.
- Act as a proxy, forwarding attacker traffic.
- Modify its configuration dynamically.
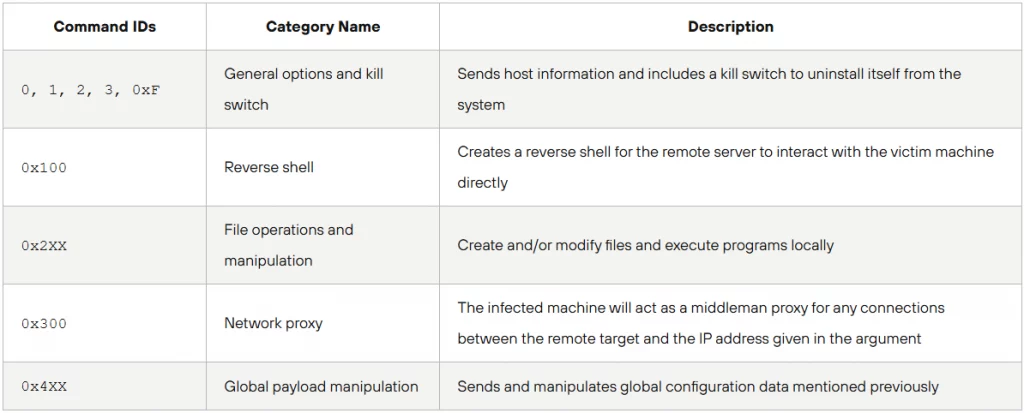
Commands supported by Auto-Color
Source: Unit 42
Auto-Color has rootkit-like features. It hooks libc functions. This intercepts system calls and hides C2 connections. It then modifies the /proc/net/tcp file.
Auto-Color Linux Backdoor also has a “kill switch.” Attackers can delete infection traces. This impedes investigations.
Defense Strategies Against Auto-Color
Auto-Color’s stealth, modular design, and remote control features make it a serious threat. Unit 42 suggests these defenses:
- Monitor changes to
/etc/ld.preload. This is a key persistence mechanism. - Check
/proc/net/tcpfor output anomalies. - Use behavior-based threat detection solutions.
- Inspect system logs and network traffic. Look for connections to listed C2 IPs. The researchers provided indicators of compromise (IoCs).
This Auto-Color Linux backdoor is a significant threat. Staying vigilant and employing robust security measures is crucial.
For more information on other recent threats, check out our latest news.










