A new ransomware strain, NailaoLocker, has been discovered targeting healthcare organizations across the European Union. The attacks, occurring between June and October 2024, exploited a vulnerability in Check Point Security Gateways (CVE-2024-24919) to gain initial access.
Ransomware Attack Methodology
The attackers used the vulnerability to deploy two known malware families, ShadowPad and PlugX, strongly associated with Chinese state-sponsored threat groups. Orange Cyberdefense CERT linked the attacks to Chinese cyber-espionage tactics, although direct attribution to specific groups remains inconclusive.
NailaoLocker Ransomware Details
Orange Cyberdefense researchers describe NailaoLocker as a relatively unsophisticated ransomware strain. “Written in C++, NailaoLocker is relatively unsophisticated and poorly designed, seemingly not intended to guarantee full encryption,” the report states.
Unlike more advanced ransomware, it doesn’t terminate security processes, lacks anti-debugging and sandbox evasion mechanisms, and doesn’t scan network shares.
The malware uses DLL sideloading (sensapi.dll) with a legitimate, signed executable (usysdiag.exe). A loader (NailaoLoader) verifies the environment, decrypts the main payload (usysdiag.exe.dat), and loads it into memory. Encryption uses AES-256-CTR, appending the “.locked” extension to files.
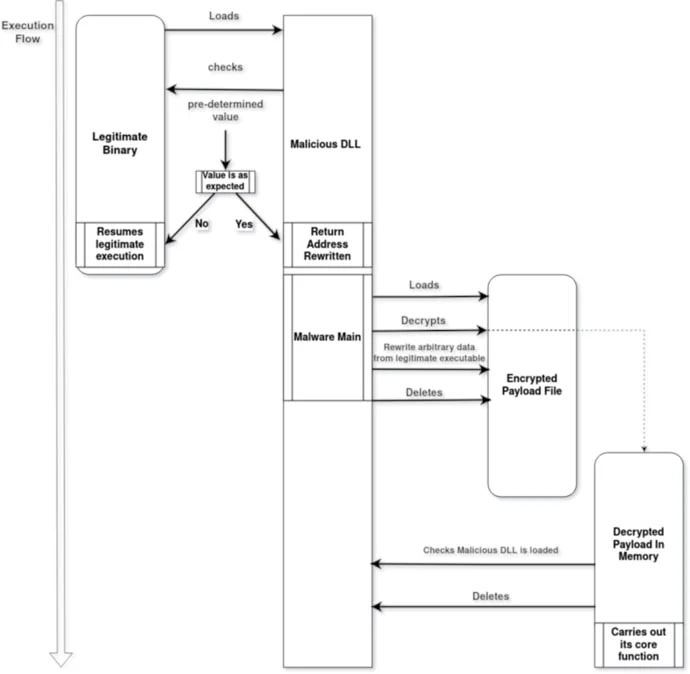
Overview of the attack chain
Source: Orange CERT
The ransom note, a lengthy HTML file (“unlock_please_view_this_file_unlock_please_view_this_file…html”), instructs victims to contact a disposable ProtonMail address (e.g., johncollinsy@proton[.]me). The note notably lacks any mention of data theft, an unusual feature for modern ransomware.
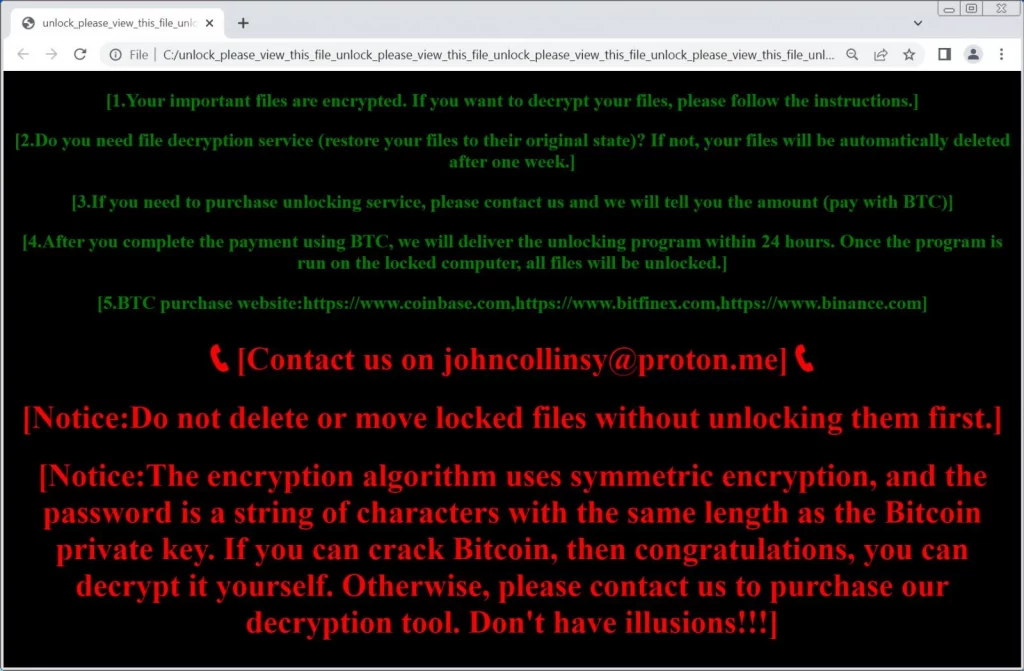
NailaoLocker ransom note
Source: Orange CERT
Espionage and Ransomware: A Combined Threat
Orange Cyberdefense noted similarities between the ransom note and a ransomware tool sold by the cybercrime group Kodex Softwares (formerly Evil Extractor), but no direct code overlap exists.
The researchers propose several hypotheses: a false flag operation, a strategic data theft operation combined with revenue generation, or a Chinese cyberespionage group supplementing their activities with ransomware for financial gain. This last hypothesis is particularly concerning, as Chinese state-backed actors haven’t previously shown this dual approach.