A devastating ransomware attack targeting the City of Columbus in July 2024 resulted in the theft of personal and financial data from a staggering 500,000 individuals.
The incident, attributed to the Rhysida ransomware gang, highlights the significant vulnerabilities of even large municipal governments to sophisticated cyberattacks. This Columbus data breach underscores the critical need for robust cybersecurity measures and transparent communication during and after such events.
The July 18th Attack and its Immediate Aftermath
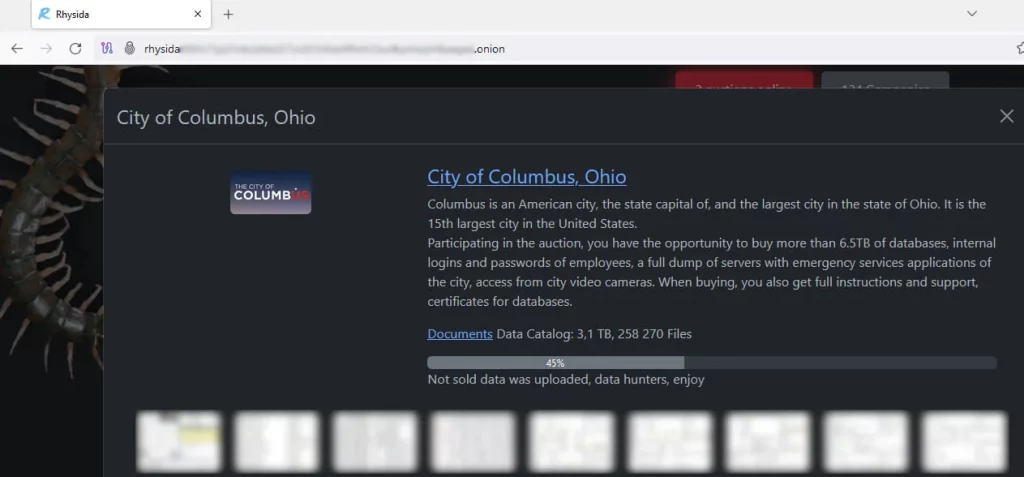
On July 18th, 2024, the City of Columbus, Ohio, fell victim to a ransomware attack. The attack, claimed by the Rhysida ransomware gang, caused significant service disruptions and impacted IT connectivity across various city agencies. Initially, city officials reported that no systems had been encrypted, focusing their investigation on the potential theft of sensitive data. The Rhysida gang, however, boasted of stealing 6.5 TB of data, including employee credentials, city video camera feeds, server dumps, and other sensitive information. Their attempt to extort the city ultimately failed.
Data Leak and the Mayor’s Controversial Statement
Following the failed extortion attempt, Rhysida began leaking the stolen data, releasing 45% (approximately 3.1 TB) of the data – comprising 260,000 documents – onto their dark web leak portal. Columbus Mayor Andrew Ginther initially downplayed the significance of the leak, stating to local media that the leaked data was “encrypted or corrupted.”
This claim was swiftly challenged by security researcher David Leroy Ross (aka Connor Goodwolf), who shared samples of the leaked data with media outlets, demonstrating that it contained unencrypted personal information belonging to city employees, residents, and visitors. This Columbus data breach exposed far more than initially acknowledged.
The City of Columbus responded to Goodwolf’s actions by filing a lawsuit, alleging that his dissemination of the stolen data was illegal and negligent. The city sought $25,000 in damages, a temporary restraining order, and a permanent injunction to prevent further data dissemination. A Franklin County judge granted the temporary restraining order, barring Goodwolf from further downloading and distributing the city’s stolen data.
City of Columbus Breach Notification and its Implications
Despite the city’s earlier assurances about the unusability of the leaked data, a breach notification letter, filed with Maine’s Office of the Attorney General and subsequently sent to 500,000 individuals in early October, revealed that the attackers had indeed stolen and published sensitive personal and financial information. The notification detailed the potential exposure of names, dates of birth, addresses, bank account information, driver’s licenses, Social Security numbers, and other identifying information.
While the city has yet to find evidence of data misuse, it advises affected individuals to monitor their credit reports and financial accounts closely. The city is also providing 24 months of free Experian IdentityWorks credit monitoring and identity restoration services. This Columbus ransomware attack serves as a stark reminder of the far-reaching consequences of such breaches.
The Significance of the Columbus City Data Breach
The Columbus ransomware attack and subsequent data breach represent a significant event in the cybersecurity landscape. The initial downplaying of the situation by city officials, followed by the revelation of the true extent of the data compromise, highlights the challenges of managing public perception and maintaining transparency during a crisis.
The case also raises questions about the effectiveness of current cybersecurity measures in protecting municipal governments from sophisticated ransomware attacks. The actions of the Rhysida ransomware gang and the subsequent legal battles underscore the complex legal and ethical considerations surrounding data breaches and the dissemination of stolen information.
The long-term impact of this Columbus city breach on the affected individuals and the city’s reputation remains to be seen. The incident serves as a cautionary tale for other municipalities, emphasizing the need for proactive cybersecurity strategies, robust incident response plans, and open communication with the public.