Rhysida Claims Ransomware Attack on Government of Peru Amid Denials from Officials
The Government of Peru is reportedly facing serious disruptions following a ransomware attack claimed by the Rhysida gang, a known cybercriminal group linked to Russia. The group published its demands on the dark web, asserting that they had stolen sensitive government data and are now offering it for sale.
The listing was added late Thursday to Rhysida’s dark leak blog, giving Peruvian authorities a May 9 deadline to respond with a ransom payment. The gang is asking for 5 bitcoin, roughly $488,000 USD, in exchange for the allegedly exfiltrated data.
Government Denies Cyberattack on Peru, Cites Website Maintenance
Despite the gang’s claims, Peruvian officials have denied any ransomware incident, attributing outages on their official portal to routine maintenance.
“Glitches on the government’s website were reported, but the government has said there is no evidence of a #cyberattack,”
— Comparatech, via X (formerly Twitter)
The country’s main web portal, Gob.pe, remained inaccessible on Friday, although a government statement reviewed by Venerix described the outage as a result of ongoing site maintenance.
Rhysida Posts Alleged Stolen Documents, Opens Data for Sale
On its site, Rhysida published several sample files purportedly taken from Peruvian government servers. Most of the samples were unreadable, but one appeared to be an official administrative document dated June 2023, bearing an official seal.
In its dark web message, the gang stated:
“With just 7 days on the clock, seize the opportunity to bid on exclusive, unique, and impressive data. Open your wallets and be ready to buy exclusive data.”
“We sell only to one hand, no reselling, you will be the only owner!”
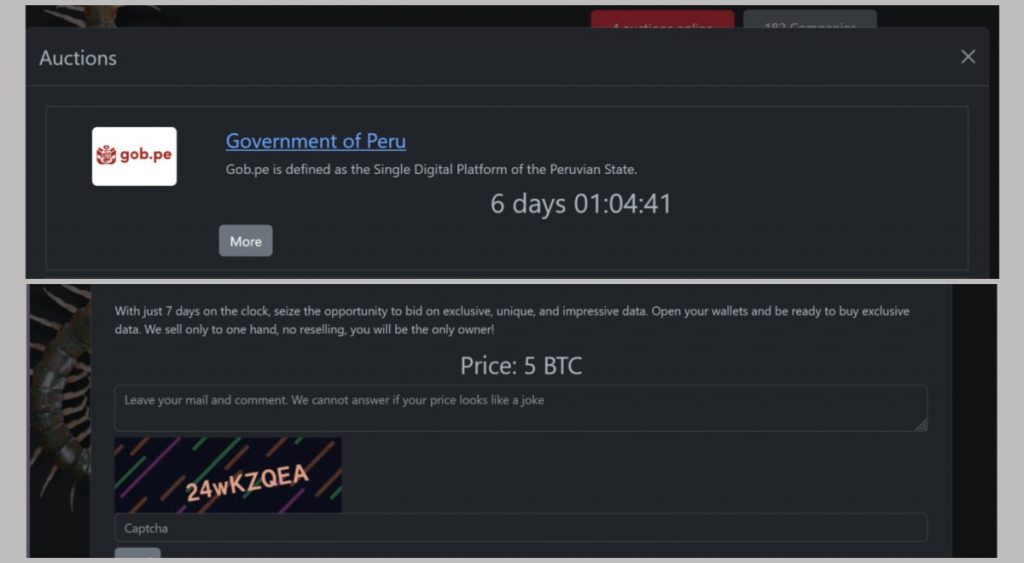
The data allegedly includes sensitive national information related to:
- National identification and passport registries
- Taxpayer records
- Health insurance data
- Labor documentation
- Police files
These systems are all hosted through Gob.pe, described as Peru’s “single digital platform” for official government services.
Rhysida’s History of High-Impact Attacks
Rhysida has become increasingly active since May 2023, claiming over 182 victims across multiple sectors, including:
- Healthcare
- Education
- Manufacturing
- Municipal governments
Notable previous attacks include:
- Montreal-Nord, Quebec (January 2025) – $1 million ransom
- City of Columbus, Ohio (July 2024) – weeks-long service outages
- Seattle-Tacoma International Airport (Sea-Tac) – 100 BTC ransom, operational disruption
- Easterseals (October 2024) – $1.35 million ransom
- UK National British Library and Lurie Children’s Hospital among others
In February 2024, KISA (Korea Internet & Security Agency) released a free decryption tool for Rhysida ransomware victims after successfully breaking the gang’s encryption.
Attack Tactics and Affiliations
Rhysida uses double extortion tactics—encrypting data and threatening to leak it unless paid. The group is also known to:
- Gain access through phishing emails
- Masquerade as cybersecurity consultants
- Deploy Cobalt Strike to identify vulnerabilities
- Launch encryption attacks under its own ransomware strain
Rhysida has also been linked to the Vice Society ransomware group, which reportedly shares tools and ransom proceeds with the gang.
Ongoing Uncertainty as Claims Remain Unverified
Threat intelligence firm Venerix stated it has verified only 22% of Rhysida’s claims to date. The remaining claims are yet to be confirmed or disproven.
While Peruvian officials maintain there is no evidence of a breach, Rhysida’s dark web posting and the site’s prolonged inaccessibility have raised concerns about the true extent of the incident.
The situation remains fluid as the ransom deadline approaches.