Ransomware groups have now entered the scene in a global cyber campaign exploiting vulnerabilities in Microsoft SharePoint. The campaign, already responsible for breaches in at least 148 organizations worldwide, is being actively tracked by cybersecurity teams, including Palo Alto Networks’ Unit 42.
The focus of the exploitation campaign—known as ToolShell—centers on two SharePoint vulnerabilities that were previously considered zero-day flaws. Attackers have now escalated the threat by deploying a new ransomware strain identified as 4L4MD4R, expanding the scope and urgency of the situation.
Ransomware Deployment Linked to Known SharePoint Exploits
Security researchers discovered the 4L4MD4R ransomware variant while investigating a malware loader used in failed exploitation attempts on SharePoint systems. The loader, found on July 27, was attempting to download and execute the ransomware from a compromised domain. During the incident, PowerShell commands were observed disabling security monitoring tools.
Unit 42 explained:
“Analysis of the 4L4MD4R payload revealed that it is UPX-packed and written in GoLang. Upon execution, the sample decrypts an AES-encrypted payload in memory, allocates memory to load the decrypted PE file, and creates a new thread to execute it.”
Once activated, 4L4MD4R encrypts files and demands 0.005 Bitcoin as ransom. It leaves a ransom note and a list of encrypted files on the infected system.
Chinese Nation-State Actors Also Involved in ToolShell Exploits
Microsoft and Google have attributed the broader exploitation campaign to Chinese state-sponsored hacking groups, including:
- Linen Typhoon
- Violet Typhoon
- Storm-2603
These groups have been exploiting internet-facing SharePoint servers to gain access to enterprise networks. Microsoft stated:
“Microsoft has observed two named Chinese nation-state actors, Linen Typhoon and Violet Typhoon exploiting these vulnerabilities… we have also observed another China-based threat actor, tracked as Storm-2603.”
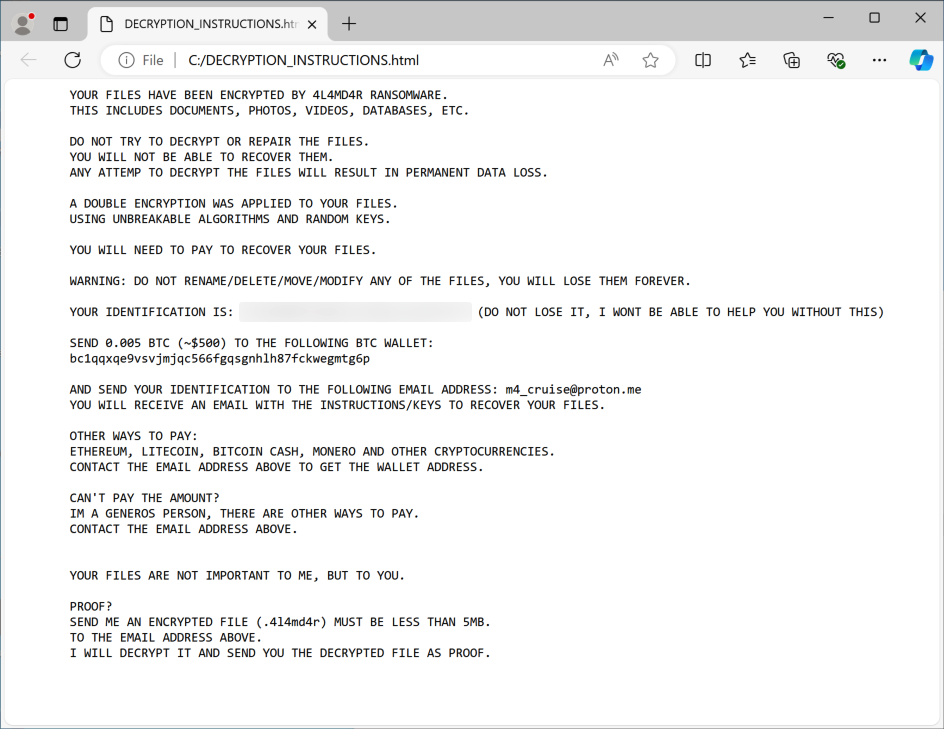
4L4MD4R decryption instructions (Unit 42)
High-Profile Organizations Already Compromised
The ongoing campaign has affected several prominent institutions and government bodies. Among the confirmed victims are:
- U.S. National Nuclear Security Administration
- U.S. Department of Education
- Florida Department of Revenue
- Rhode Island General Assembly
- Government agencies across Europe and the Middle East
Eye Security, the Dutch cybersecurity firm that initially flagged the ToolShell exploit chain, traced early attacks back to vulnerabilities CVE-2025-49706 and CVE-2025-49704. Their early findings included at least 54 affected organizations. Check Point Research later confirmed that exploitation activity began as early as July 7.
Microsoft and CISA Respond with Urgent Patches and Directives
In response, Microsoft issued urgent security patches during its July 2025 Patch Tuesday update and assigned two new identifiers for the exploited flaws: CVE-2025-53770 and CVE-2025-53771. These were aimed at blocking active exploitation of even fully patched SharePoint servers.
The Cybersecurity and Infrastructure Security Agency (CISA) has since added CVE-2025-53770 to its catalog of known exploited vulnerabilities. CISA has instructed all federal agencies to secure affected systems within 24 hours.
Despite early figures, Eye Security’s CTO Piet Kerkhofs emphasized the scale is much broader than initially thought. Their telemetry points to over 400 infected servers across 148 organizations, many of which may have been compromised for extended periods.









