The HellCat hacking group is behind a global wave of attacks targeting Jira servers, compromising sensitive data across numerous organizations. This sophisticated campaign highlights the vulnerability of widely used project management platforms and the persistent threat of credential theft.
HellCat Hackers’ Modus Operandi: Exploiting Compromised Credentials
HellCat’s attacks leverage compromised employee credentials, often obtained through infostealers, to gain access to Jira servers. This method has proven highly effective, as evidenced by successful breaches at Ascom, Schneider Electric, Telefónica, Orange Group, Jaguar Land Rover, and Affinitiv. The stolen data frequently includes source code, project details, invoices, confidential documents, and internal communications.
Ascom, a Swiss telecommunications company, recently confirmed a breach where HellCat stole approximately 44GB of data.
According to a HellCat member, “they stole from Ascom source code for multiple products, details about various projects, invoices, confidential documents, and issues from the ticketing system.”
Despite Ascom stating the breach had no impact on business operations, the theft of sensitive information presents a significant risk.
The Jaguar Land Rover (JLR) breach, also attributed to HellCat, resulted in the theft and leak of around 700 internal documents.
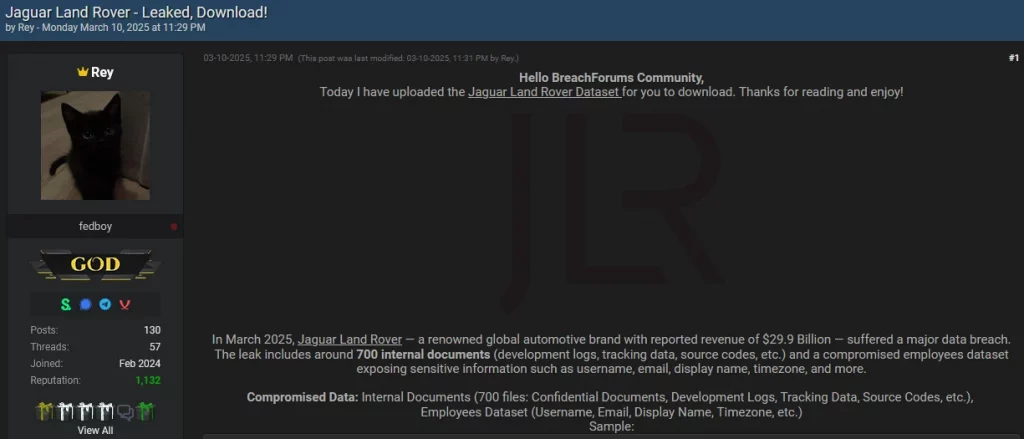
HellCat ransowmare claims Jaguar Land Rover breach
“At the heart of this latest incident lies a technique that has become HELLCAT’s signature: exploiting Jira credentials harvested from compromised employees that were infected by Infostealers.” Alon Gal, co-founder and CTO at Hudson Rock, explained.
In this case, the compromised credentials belonged to an LG Electronics employee with access to JLR’s Jira server, highlighting the risk of third-party access. These credentials, exposed years prior, remained valid, underscoring the importance of regular credential rotation.
Affinitiv, a marketing analytics company, also fell victim to a HellCat attack via its Jira system, resulting in the theft of a database containing over 470,000 unique emails and more than 780,000 records.
To demonstrate the breach, HellCat publicly released screenshots showing names, email addresses, postal addresses, and dealership names.
Jira: A Prime Target for Attackers
Alon Gal warns that Jira’s central role in enterprise workflows and the wealth of data it contains make it a prime target. He emphasizes that such access can be used to “move laterally, escalate privileges, and extract sensitive information.”
The ease of obtaining compromised credentials from infostealers, coupled with the persistence of unchanged credentials, makes these attacks increasingly likely. Companies must prioritize regular credential rotation and robust security measures to mitigate this risk.