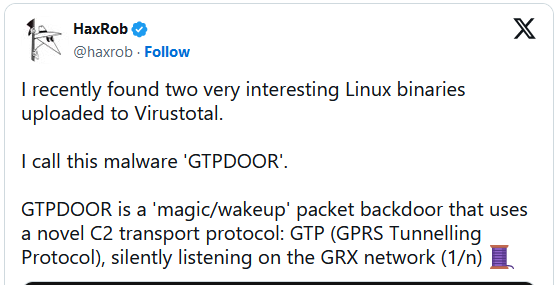
Security researcher HaxRob has recently identified a Linux backdoor called GTPDOOR that has not been previously documented. This backdoor appears to have been specifically developed for stealthy activities within mobile carrier networks.
The UNC1945 threat actors responsible for GTPDOOR Linux Malware are suspected of focusing on systems in close proximity to the GPRS roaming eXchange (GRX), including SGSN, GGSN, and P-GW. By compromising these systems, the attackers can gain direct entry into a telecom’s core network.
The GRX is a crucial element of mobile telecommunications that facilitates seamless data roaming services across various networks and geographical regions. Within a mobile operator’s network infrastructure, the SGSN, GGSN, and P-GW play distinct roles in supporting mobile communications.
The researcher’s analysis suggests that the SGSN, GGSN, and P-GW networks, being more publicly exposed with their IP address ranges documented in public sources, are the primary targets for initial access to a mobile operator’s network.
GTPDOOR Linux Malware Associated with ‘LightBasin’ (UNC1945)
The GTPDOOR backdoor is believed to be associated with the threat group known as ‘LightBasin’ (UNC1945). This particular group has gained notoriety for conducting intelligence-collection activities directed at numerous telecommunications companies globally.
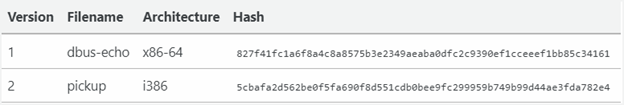
The researcher detected two distinct versions of the GTPDOOR backdoor, which were uploaded to VirusTotal in late 2023. It is worth noting that these versions managed to evade detection by most antivirus engines.
The binaries were specifically designed to target an outdated version of Red Hat Linux, suggesting that the attackers are focusing on systems that may not have received the latest security updates.
Stealthy GTPDOOR Malware Modus Operandi
The GTPDOOR linux malware is a highly advanced threat specifically crafted for telecommunications networks. It exploits the GPRS Tunnelling Protocol Control Plane (GTP-C) to establish covert command and control (C2) communications.
This backdoor is intended to be deployed within Linux-based systems that are in close proximity to the GRX. These systems play a crucial role in routing and forwarding roaming-related signaling and user plane traffic.
By utilizing the GTP-C protocol for communication, GTPDOOR malware can effectively camouflage itself within legitimate network traffic, taking advantage of permitted ports that typically go unnoticed by standard security solutions. To further enhance its stealth capabilities, the malware has the ability to modify its process name, mimicking legitimate system processes.
GTPDOOR Linux Malware operates by actively monitoring specific GTP-C echo request messages, often referred to as “magic packets.” Upon receiving such packets, the malware awakens and executes the designated command on the infected host, subsequently sending the output back to its operators.
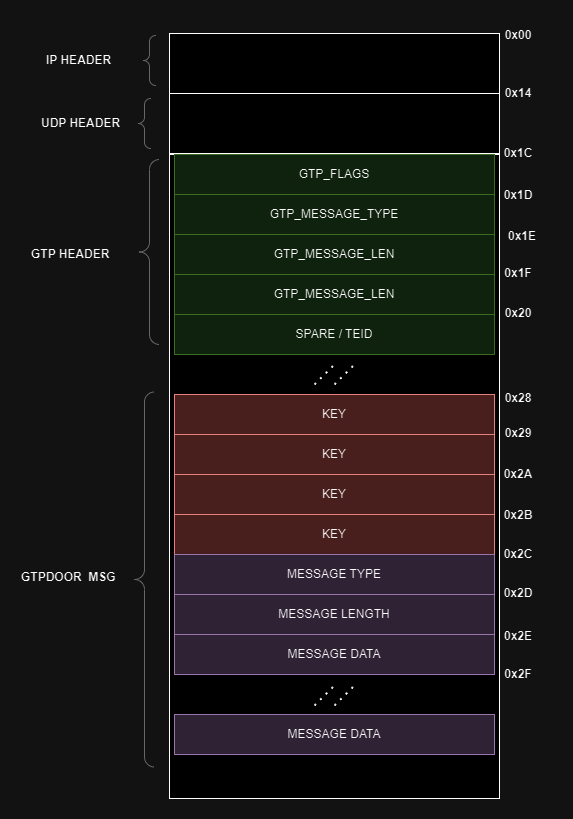
Malicious packet structure
Source: (doubleagent.net)
To ensure that only authorized operators have control over the malware, the contents of these magic GTP packets undergo authentication and encryption using a simple XOR cipher. This cryptographic measure ensures the integrity and confidentiality of the communication between the malware and its operators.
GTPDOOR version 1 provides the capability to perform the following operations on compromised hosts:
- Setting a new encryption key: The backdoor can establish a fresh encryption key to be utilized for command and control (C2) communications, enhancing the security of its covert interactions.
- Writing arbitrary data to ‘system.conf’: The malware has the ability to write any desired information to a local file named ‘system.conf’. This allows the threat actors to store and manipulate data as needed within the compromised system.
- Executing arbitrary shell commands: GTPDOOR can execute shell commands of the threat actors’ choice on the infected host. It then transmits the output generated by these commands back to the attackers. This functionality enables the threat actors to remotely control and operate the compromised system.
In addition to the operations mentioned earlier, GTPDOOR version 2 introduces additional features:
- IP address/subnet-based Access Control List (ACL): The backdoor now supports specifying specific IP addresses or subnets that are permitted to communicate with the compromised host. This ACL mechanism provides a level of control over network connections, allowing only authorized entities to establish communication with the backdoor.
- Dynamic adjustment of network permissions: GTPDOOR v2 enables the retrieval of the ACL list, allowing for real-time modifications to the backdoor’s network permissions. This flexibility allows threat actors to adapt and adjust the allowed communication channels as needed, enhancing their control over the compromised host.
GTPDOOR Malware Clears the ACL to Reset Itself
HaxRob further emphasizes that GTPDOOR possesses the capability to be surreptitiously probed from an external network, triggering a response through a TCP packet transmitted via any port. This behavior allows the malware to evade detection by traditional port-based security measures.
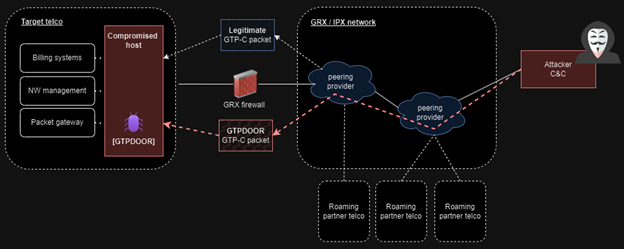
GTPDOOR attack overview
Source: (doubleagent.net)
Detection and Defense Against the GTPDOOR Linux Malware
To effectively detect and defend against GTPDOOR Linux Malware and similar threats, it is crucial to implement robust detection strategies. The following steps are recommended for detection:
- Monitor raw socket activities: Keep a close eye on any unusual raw socket activities, as they may indicate a potential breach. Tools like “lsof” can be used to check for open raw sockets.
- Analyze listening sockets: Use the command “netstat -lp –raw” to identify any abnormal or unexpected listening sockets that may be associated with the malware.
- Identify suspicious processes: Look for processes that mimic kernel threads but have abnormal Parent Process IDs (PPIDs). These processes may be indicative of GTPDOOR Linux Malware or other malicious activity.
- Search for mutex file: Check for the presence of the mutex file “/var/run/daemon.pid,” which is commonly utilized by GTPDOOR. Its existence may indicate an infection.
- Check for unexpected system.conf file: Look for the presence of an unexpected “system.conf” file, as this may be a sign of GTPDOOR’s presence. The malware may create this file to store its configuration or other relevant information.
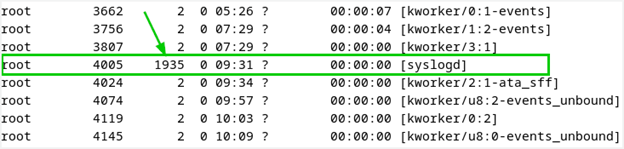
Abnormal PID
Source: (doubleagent.net)
This YARA rule is also provided to the defenders to detect the GTPDOOR Linux malware.
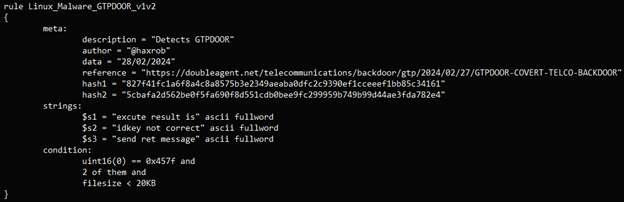
To counter this threat, the researcher suggests implementing GTP firewalls with stringent rules and strict adherence to the security guidelines established by GSMA (Global System for Mobile Communications Association).
These measures aim to effectively block or filter out malicious packets and connections, fortifying the defenses against GTPDOOR and similar threats.