A serious supply chain attack targeting the widely used tj-actions/changed-files GitHub Action has exposed CI/CD secrets from thousands of repositories. This popular automation tool, utilized by approximately 23,000 repositories, allows developers to identify modified files in pull requests or commits, triggering actions like testing and code validation.
The attack, first reported by StepSecurity, involved a malicious commit added on March 14, 2025, at 4:00 PM UTC. This commit surreptitiously dumped CI/CD secrets from the Runner Worker process into the repositories of projects using the action. The vulnerability was particularly impactful because publicly accessible workflow logs made these stolen secrets easily viewable.
Attackers cleverly modified the action’s code and retroactively updated multiple version tags to point to the malicious commit. This meant that all versions of the tj-actions/changed-files tool were compromised. The developers later revealed that the attacker gained access by compromising a GitHub Personal Access Token (PAT) belonging to a bot, @tj-actions-bot, with privileged repository access. The method of PAT compromise remains unclear.
GitHub swiftly responded. On March 15, at 2:00 PM UTC, the compromised action was removed. By 10:00 PM UTC that same day, the repository was restored after the malicious code was eliminated. A CVE ID, CVE-2025-30066, has been assigned to track this incident.
Interestingly, the malicious code didn’t exfiltrate data to a remote server. Instead, it only made the stolen secrets visible within publicly accessible repository logs, obfuscated as a double-encoded base64 payload.
“The compromised action injected malicious code into any CI workflows using it, dumping the CI runner memory containing the workflow secrets. On public repositories, the secrets would then be visible to everyone as part of the workflow logs, though obfuscated as a double-encoded base64 payload.”
As Wiz explains in their analysis of the incident.
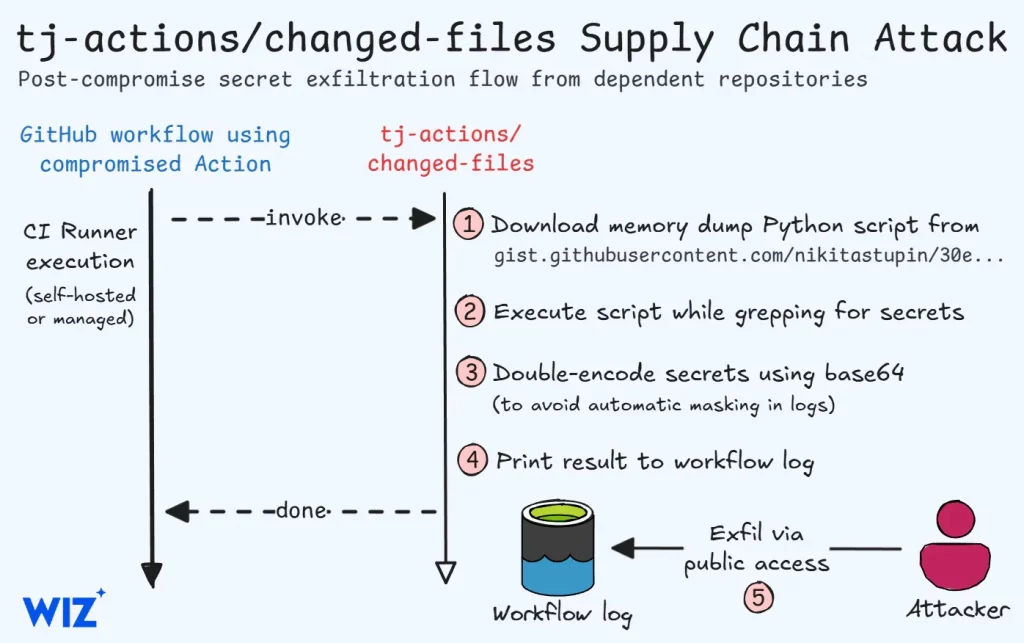
tj-actions supply chain attack
Source: Wiz
The restored tj-actions repository now includes instructions for impacted users:
- Rotate any secrets used between March 14th and 15th.
- Review workflows for unexpected output in the ‘changed-files’ section.
- Update workflows referencing the compromised commit by SHA immediately.
- Ensure you’re using a tagged version (e.g., v35, v44.5.1).
To mitigate future risks, GitHub recommends pinning GitHub Actions to specific commit hashes instead of version tags. GitHub also offers allow-listing functionality to block untrusted actions.
Helpful Reads:









