The Everest ransomware gang added Mailchimp to its dark leak site in late July, claiming to have stolen internal documents and a “767 MB” dataset. Security insiders and Mailchimp’s parent company, Intuit, are casting doubt on the impact—calling the alleged compromise little more than crumbs and reporting no evidence of a breach in their systems.
Everest posts Mailchimp as a victim, touts internal documents while offering a ticking clock negotiation
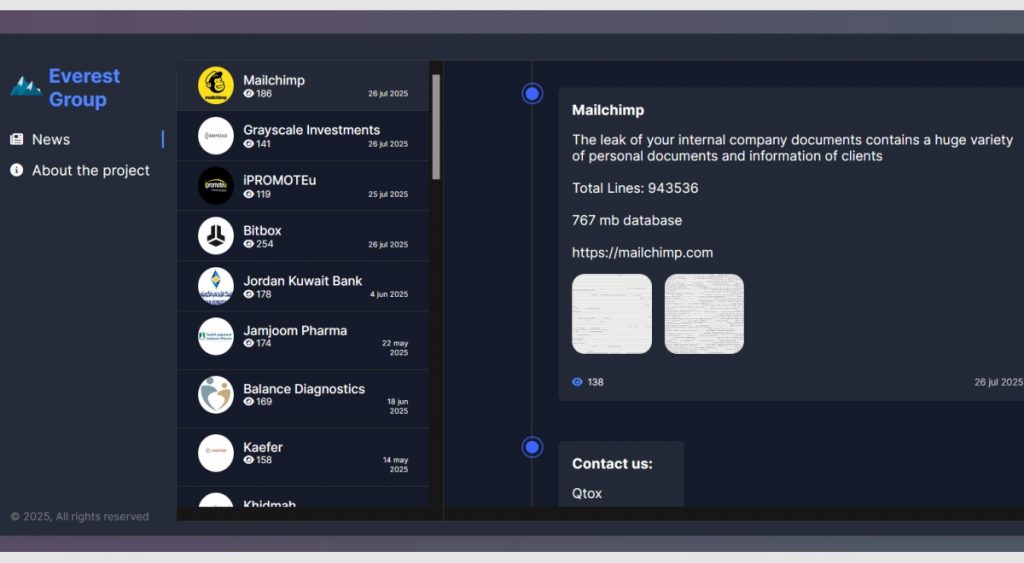
On July 26, Everest listed Mailchimp among its latest victims, joining a wave of July targets that included Crumbl cookie company and BitBox, a crypto storage firm. The group claimed to have exfiltrated a “767 mb database” containing “943,536” lines of internal data and warned that Mailchimp had four days to open ransom negotiations, embedding voice-recorded instructions accessible only until their countdown timer expires.
Everest’s post framed the haul as significant, saying:
“The leak of your internal company documents contains a huge variety of personal documents and information of clients.”
But the claim immediately drew skepticism from observers. Analysts noted the volume of data was minuscule relative to Mailchimp’s scale—some described it as “300 milliseconds worth of Mailchimp data” or equivalent to a single customer. The tone on social media quickly turned mocking, with comments like, “We got yer crumbs. Come and get them,” underscoring the perception that the material did not reflect a systemic compromise.
Everest leak site. Image by Cybernews.
Mailchimp and Intuit report no evidence of system breach amid public doubt
In an update, Intuit spokesperson Tania Mercado told reporters that Mailchimp’s security teams were aware of Everest’s claims but had found no evidence of any data exfiltration or system compromise.
“The security of our products and our customers’ data are among our highest priorities. Based on our investigation at this time we have no evidence to suggest any security incidents or exfiltration of data from our systems,” Mercado said.
Mailchimp, founded in 2001 and now owned by Intuit after a $12 billion acquisition, serves millions globally. Despite its size—reportedly handling hundreds of billions of emails for clients and boasting millions of active users—the allegedly compromised snippet appears to have limited scope, further fueling debate over whether Everest holds leverage or merely seeks reputational pressure.
Everest’s wider campaign shows evolution from encryption to data extortion
The Mailchimp claim sits within Everest’s broader strategy. First observed in July 2021 and linked to Russian-speaking infrastructure, the group has gradually shifted away from heavy reliance on encryption to prioritize data theft and leaking as a pressure tactic. According to dark web tracking, Everest listed 248 victims since 2023, including 90 in the past year, with recent activity pushing into regions such as the Middle East.
Security researchers note that Everest publicly names victims and releases partial datasets to create reputational, legal, and financial urgency, increasing the probability of payouts. Martin Vigo, lead security researcher at AppOmni, has described the approach as “using the leak site as a pressure mechanism,” where the public exposure itself compounds the cost of inaction for targeted organizations.
Other recent Everest claims show mixed credibility and consequences
Earlier in the same period, Everest listed Crumbl and BitBox as victims. Crumbl’s listing disappeared from the leak site, prompting speculation the company paid a ransom. In BitBox’s case, security researcher Dominic Alvieri noted that posted samples appeared to include recent order fulfillment data tied to identifiable hardware wallet purchasers, signaling a more tangible risk:
“Everest did post samples that appear to be recently fulfilled orders from BitBox redirected with identifiable hardware wallet purchaser data. I would be somewhat concerned here.”
That contrasts with the Mailchimp allegation, where insiders describe the exposed material as lacking in depth or impact.
Implications for enterprises and threat attribution
The Mailchimp episode illustrates how extortion groups can attempt to extract value through narrative and perception, even when technical substance is thin or unverified. For large platforms, the mere appearance on a leak site can trigger customer concern, stock scrutiny, and internal resource diversion, regardless of actual compromise.
Everest’s blend of data theft, public naming, and negotiated countdowns reinforces the evolving ransomware/extortion landscape, where reputational pressure is as much a tool as the threat of widespread leaks.









