A new botnet named Eleven11bot has infected over 86,000 Internet of Things (IoT) devices, primarily targeting security cameras and network video recorders (NVRs) to conduct Distributed Denial of Service (DDoS) attacks.
Discovery and Scale of Eleven11bot
The Eleven11bot botnet was discovered by researchers at Nokia, who later shared their findings with the threat monitoring platform GreyNoise. Nokia’s security researcher, Jérôme Meyer, commented on the botnet’s significant scale, stating:
“Primarily composed of compromised webcams and Network Video Recorders (NVRs), this botnet has rapidly grown to exceed 30,000 devices. Its size is exceptional among non-state actor botnets, making it one of the largest known DDoS botnet campaigns observed since the invasion of Ukraine in February 2022.”
As of March 4, 2025, the threat monitoring platform The Shadowserver Foundation reported that Eleven11bot has infected approximately 86,400 devices, with the majority located in the United States, the United Kingdom, Mexico, Canada, and Australia.
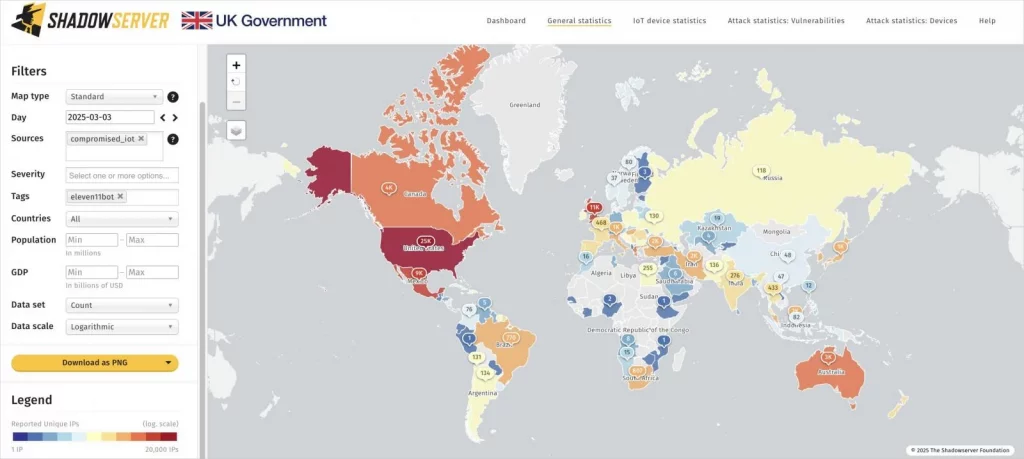
Countries impacted by Eleven11bot
Source: The Shadowserver Foundation
Impact and Attack Volume
Meyer noted that the attacks launched by Eleven11bot have reached volumes of several hundred million packets per second, often lasting multiple days.
GreyNoise, in collaboration with Censys, has identified 1,400 IP addresses linked to the botnet’s operations over the past month, with 96% of these originating from legitimate devices.
The majority of the malicious IP addresses are traced back to Iran, with over 300 classified as malicious by GreyNoise.
Infection Methodology
The Eleven11bot malware spreads by exploiting weak or common admin credentials, utilizing known default passwords for specific IoT models, and actively scanning networks for exposed Telnet and SSH ports.
To combat this growing threat, GreyNoise has published a list of IP addresses associated with Eleven11bot. Organizations are advised to add these addresses to their blocklists and monitor for any suspicious login attempts.

Countries impacted by Eleven11bot
Source: The Shadowserver Foundation
Recommendations for Enterprise IoT Security
To protect against the Eleven11bot threat, enterprises should:
- Ensure all IoT devices are running the latest firmware.
- Disable remote access features when not needed.
- Change default admin credentials to strong, unique passwords.
Given that IoT devices often lack long-term vendor support, regularly checking for end-of-life (EOL) status and replacing outdated devices is crucial.









