The DollyWay malware campaign, active since 2016, has compromised over 20,000 WordPress websites globally. This sophisticated operation redirects users to malicious sites, generating millions of fraudulent impressions monthly. The campaign’s evolution over eight years showcases advanced evasion and monetization techniques, posing a significant threat to businesses relying on WordPress.
DollyWay’s Multi-Stage Attack
DollyWay’s latest version (v3) functions as a large-scale scam redirection system. However, previous iterations distributed more harmful payloads, including ransomware and banking trojans. GoDaddy researcher Denis Sinegubko highlights the campaign’s complexity: “GoDaddy Security researchers have uncovered evidence linking multiple malware campaigns into a single, long-running operation we’ve named ‘DollyWay World Domination’,” according to a recent GoDaddy report. The name originates from a string found in some malware variations: define('DOLLY_WAY', 'World Domination').
DollyWay redirects victims to landing page
Source: GoDaddy
The attack unfolds in three stages:
- Initial Compromise: DollyWay v3 exploits vulnerabilities in WordPress plugins and themes to gain access. A script injection using
wp_enqueue_scriptdynamically loads a secondary script. - Data Collection and Filtering: This second script gathers visitor referrer data to categorize traffic. It then identifies and filters out invalid targets—direct visitors without referrers, known bots (a hardcoded list of 102 user-agents), and logged-in WordPress users.
- Final Redirection: Three random infected sites are selected as Traffic Direction System (TDS) nodes. A hidden JavaScript script from one of these nodes performs the final redirection to scam pages hosted on VexTrio and LosPollos affiliate networks. Crucially, redirection only occurs upon user interaction (clicks), evading passive scanning tools. The malware uses affiliate tracking parameters to ensure payment for each redirection.
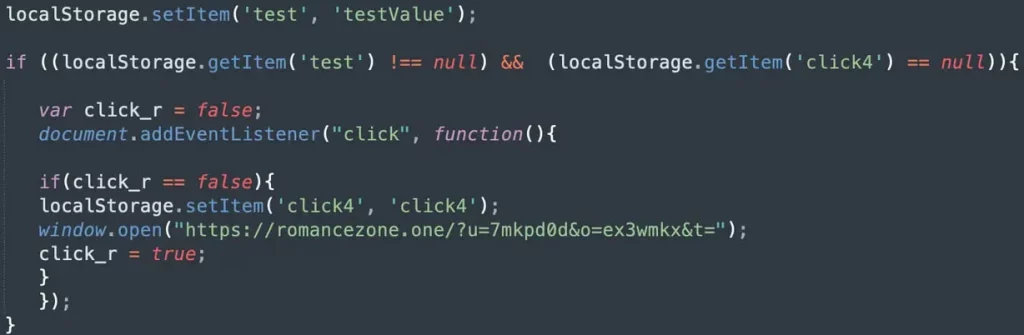
JavaScript snippet performing conditional redirection to a scam website
Source: GoDaddy
Persistence and Evasion Techniques
DollyWay’s persistence is remarkable. It automatically reinfects a site with each page load, making removal challenging. This is achieved by distributing its PHP code across all active plugins and adding a copy of the WPCode plugin (if not already installed) containing obfuscated malware snippets. The hackers cleverly hide WPCode from the WordPress plugin list, hindering removal.
Furthermore, DollyWay creates hidden admin users with random 32-character hex strings, only detectable through direct database inspection. These techniques significantly complicate remediation efforts. Learn more about protecting your systems from similar attacks by reading our article on Top Cyber Threats Facing Enterprise Businesses in 2025.
GoDaddy has shared indicators of compromise (IoCs) to aid in defense against DollyWay. They plan to release further details on the operation’s infrastructure and tactics in a future post. Understanding the complexities of these attacks is crucial for enterprise-level security. For more information on advanced persistent threats, see our article on Phishing Prevention Strategies.









