Microsoft has issued a warning about a persistent phishing campaign leveraging the ClickFix social engineering technique. This campaign, active since December 2024, impersonates Booking.com and targets hospitality industry employees.
The goal is to compromise employee accounts and steal customer payment and personal data, potentially enabling further attacks. The threat actor behind this campaign is identified by Microsoft as ‘Storm-1865’.
ClickFix is a relatively new social engineering tactic. It presents fake errors on websites or in documents, prompting users to perform a “fix” or “CAPTCHA” to view content. These “fixes” are actually malicious commands that download and install malware. This technique has gained popularity among various threat actors, including ransomware groups and state-sponsored actors.
In this Booking.com impersonation campaign, emails are crafted to mimic various scenarios, including:
- Inquiries about negative reviews.
- Requests from prospective clients.
- Account verification alerts.
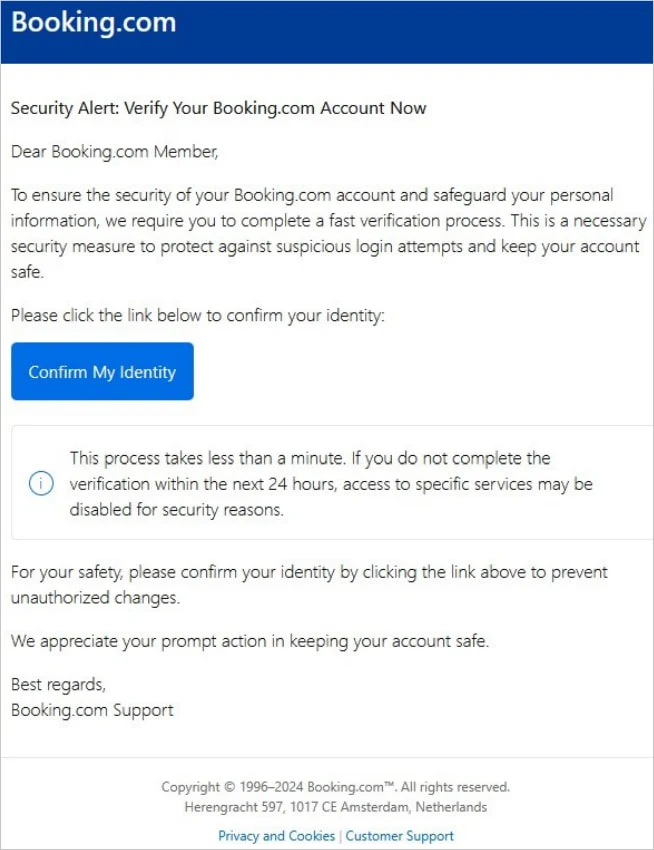
Email sent to targets
Source: Microsoft
These emails contain either a malicious PDF attachment or an embedded button, both leading to a fake CAPTCHA page. The fake CAPTCHA adds a layer of legitimacy, aiming to trick recipients into lowering their guard.
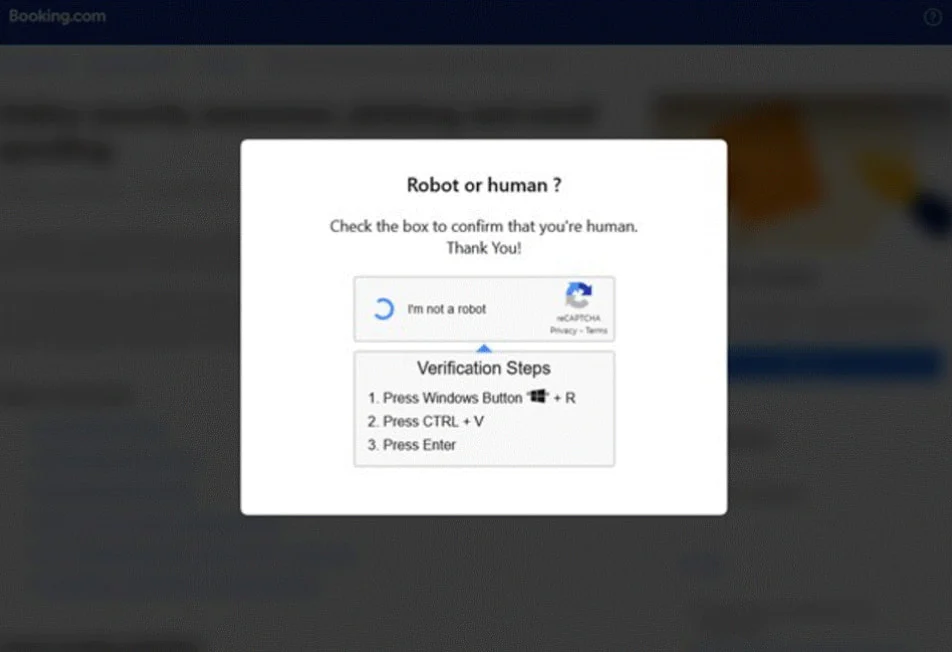
CAPTCHA page
Source: Microsoft
When the user attempts to “solve” the CAPTCHA, a hidden mshta.exe command is copied to the clipboard.
Victims are instructed to paste this into the Windows Run command and execute it. The command executes a malicious HTML file (VirusTotal) on the attacker’s server, downloading and installing malware.

Malicious ‘mshta’ command copied to Windows clipboard
Source: Microsoft
The malware delivered includes a range of Remote Access Trojans (RATs) and infostealers:
- XWorm
- Lumma stealer
- VenomRAT
- AsyncRAT
- Danabot
- NetSupport RAT
Microsoft’s report states: “Depending on the specific payload, the specific code launched through mshta.exe varies. Some samples have downloaded PowerShell, JavaScript, and portable executable (PE) content. All these payloads include capabilities to steal financial data and credentials for fraudulent use, which is a hallmark of Storm-1865 activity.”
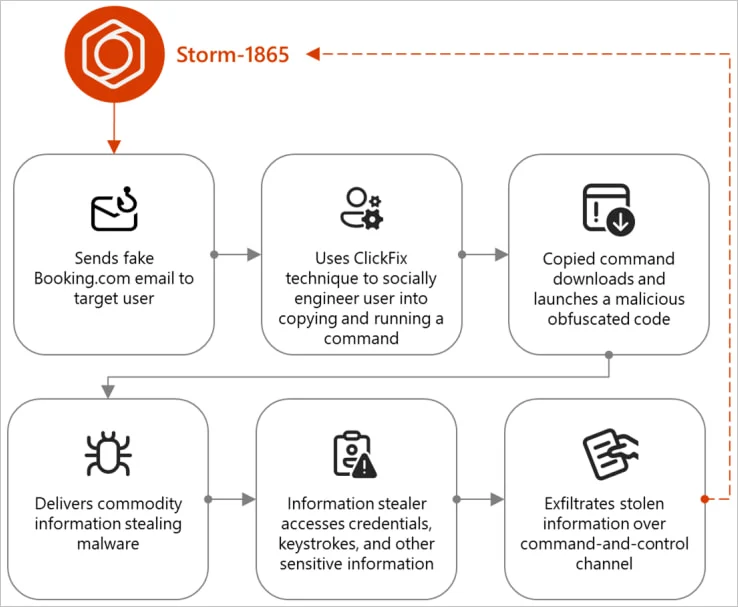
Overview of the Storm-1865 ClickFix attack
Source: Microsoft
To protect against these attacks, Microsoft recommends:
- Verifying sender email addresses.
- Exercising caution with urgent requests.
- Checking for typos in emails.
- Accessing Booking.com accounts directly, rather than through email links.
Booking.com has also released a statement confirming that their systems haven’t been breached but acknowledging that some partners and customers have been impacted by this phishing campaign.
They emphasize that they would never request payment information via unofficial channels and encourage users to report suspicious communications. This highlights the importance of employee training and awareness regarding Phishing Prevention Strategies.
Helpful Reads:









