Exploit Details Now Public for Critical Cisco IOS XE WLC Vulnerability
A critical vulnerability in Cisco IOS XE Wireless LAN Controllers (WLC), tracked as CVE-2025-20188, is now in the spotlight after researchers from Horizon3 published technical details that could pave the way for full remote code execution (RCE) attacks. The flaw allows attackers to upload arbitrary files and execute commands as root—without authentication—when specific features are enabled.
What the Vulnerability Entails
Cisco first disclosed the flaw on May 7, 2025. The root of the issue is a hard-coded JSON Web Token (JWT) used in backend processes. This JWT secret—literally the string “notfound”—allows attackers to craft valid tokens and abuse a file upload endpoint without needing actual credentials.
Cisco rated the issue as critical and noted that exploitation is only possible when the Out-of-Band AP Image Download feature is enabled. When active, the flaw impacts:
- Catalyst 9800-CL Wireless Controllers for Cloud
- Catalyst 9800 Embedded Wireless Controllers for 9300/9400/9500 Series
- Catalyst 9800 Series Wireless Controllers
- Embedded Wireless Controllers on Catalyst Access Points
Horizon3’s Technical Walkthrough
The Horizon3 team analyzed the vulnerability and revealed how it can be triggered. The backend of the Cisco WLC software uses OpenResty—a framework combining Lua with Nginx—for handling file uploads. JWT validation falls back to the string “notfound” when a key file is missing, effectively giving attackers a way in.
In the example shared, an HTTP POST request is sent to the vulnerable endpoint /ap_spec_rec/upload/ on port 8443. By manipulating the filename and using directory traversal techniques, attackers can drop files outside the expected upload path.
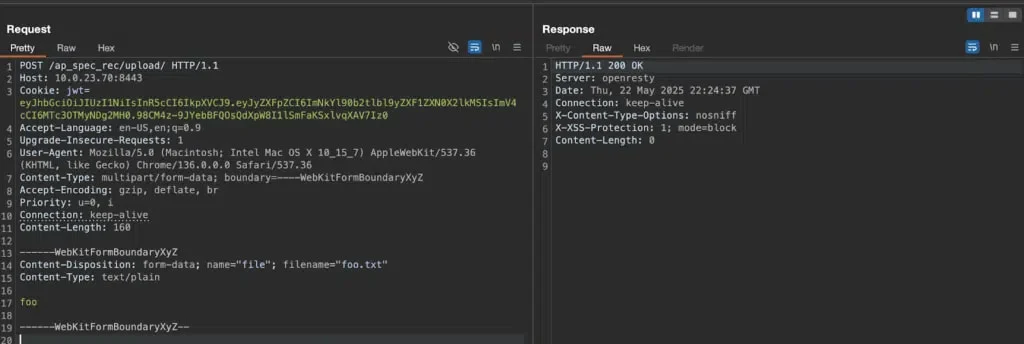
Request to regenerate the JWT using the notfound secret key
Source: Horizon3
“Once you’ve bypassed file path validation, you can overwrite monitored config files or drop a web shell,” Horizon3 explained. One of the abused components is pvp.sh, a service that watches directories and reloads configurations. By overwriting these files and triggering a reload, attackers can execute arbitrary commands with root privileges.
Implications for Enterprises
The risk of exploitation is high, especially now that enough details are publicly available for skilled attackers—or even automated tools—to build working exploits.
Although Horizon3 did not release a fully functional exploit, the documentation leaves few gaps. With automated scanning tools and templates already in circulation, attackers can act fast.
Administrators are strongly advised to upgrade to Cisco IOS XE version 17.12.04 or later. If immediate patching isn’t possible, disabling the Out-of-Band AP Image Download feature can temporarily mitigate the risk.
Final Note for Security Teams
This vulnerability underscores the importance of hardening infrastructure, avoiding hard-coded secrets, and regularly auditing enabled features. Wireless LAN Controllers sit at the heart of enterprise networks. A breach here isn’t just a technical flaw—it’s a gateway to broader compromise.









