APT28 Leverages Signal Messaging Platform in Targeted Malware Attacks on Ukraine
APT28, a Russian state-sponsored threat actor also tracked as UAC-0001, has been linked to a new wave of cyberattacks targeting Ukrainian government entities. According to CERT-UA and cybersecurity firm ESET, the group is now using Signal, the encrypted messaging platform, to deliver two newly discovered malware strains: BeardShell and SlimAgent.
While the use of Signal in this campaign may appear alarming, there is no vulnerability in the Signal platform itself. Rather, the attackers are exploiting the platform’s growing popularity and perceived trustworthiness, particularly among government and military users, to deliver malicious payloads in social engineering campaigns.
Attack Timeline and Infection Chain
- The campaign was first observed in March 2024, with limited visibility into the infection method.
- In May 2025, ESET reported unauthorized access to a gov.ua email account, triggering a deeper incident response.
- The investigation revealed that attackers used Signal messages to send a malicious document (Акт.doc) to their targets.
- Once opened, the document executed macros that launched a Covenant malware loader, a memory-resident backdoor.
- Covenant then fetched and launched:
- A malicious DLL file (
PlaySndSrv.dll) - A shellcode-laced WAV file (
sample-03.wav) to deploy BeardShell.
- A malicious DLL file (
Russian APT28 Hackers Exploit Signal in Targeted Cyberattacks on Ukraine
Russia-linked APT28, one of the most advanced cyberespionage groups globally, has launched a new round of targeted attacks against Ukrainian government systems, this time by leveraging the Signal messaging platform as a delivery channel for phishing and malware payloads.
This campaign is not due to a vulnerability in Signal itself. Rather, the platform’s widespread use by government personnel has made it a useful social engineering tool. Ukraine’s Computer Emergency Response Team (CERT-UA), supported by ESET, confirmed that Signal messages were used to deliver malicious documents in recent spear-phishing operations.
Sophisticated Infection Chain Begins with Signal
The attack starts with a Signal message containing a malicious document titled Акт.doc. Once opened, it triggers macros that launch Covenant, a memory-resident backdoor known for acting as a malware loader.
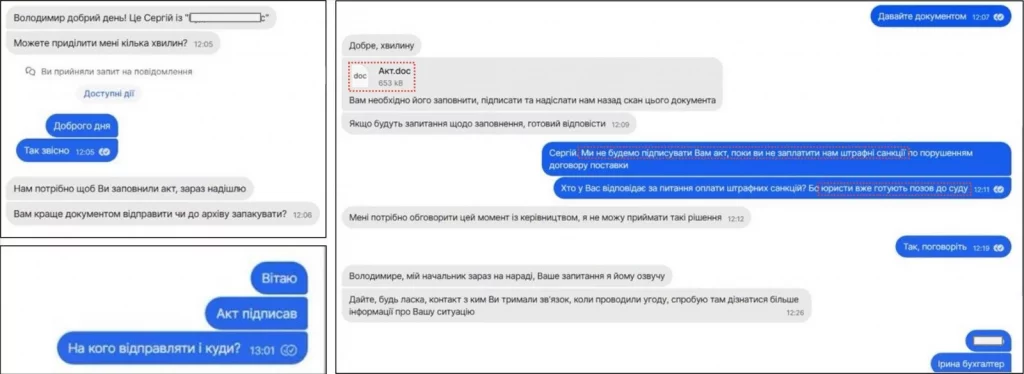
APT28 attack via Signal
Source: CERT-UA
From there, Covenant downloads two additional files:
- A dynamic link library (PlaySndSrv.dll)
- A specially crafted WAV file (sample-03.wav) embedded with shellcode
These components together deploy BeardShell, a previously undocumented backdoor written in C++.
BeardShell Malware and How It Works
BeardShell operates as a remote access trojan (RAT) with a focus on PowerShell-based execution. Once installed, it performs the following actions:
- Downloads encrypted PowerShell scripts
- Decrypts them using ChaCha20-Poly1305
- Executes commands and sends output to its C2 server using the Icedrive API
Persistence is achieved through COM hijacking, a technique where attackers modify Windows registry keys to ensure malware runs each time the system starts.
SlimAgent: Screenshot Grabber Used in Earlier Attacks
CERT-UA also observed a second malware family, SlimAgent, used during similar attacks in 2024. SlimAgent captures screen activity using native Windows API functions:
EnumDisplayMonitorsCreateCompatibleDCCreateCompatibleBitmapBitBltGdipSaveImageToStream
Captured screenshots are encrypted with AES and RSA, then stored locally—likely awaiting exfiltration through separate malware modules.
APT28 Attribution and Broader Strategy
CERT-UA attributed these operations to APT28, which it tracks as UAC-0001. The group has a history of highly targeted intrusions involving phishing, MFA bypass, and exploitation of trusted communication channels.
APT28 was previously exposed in 2024 for a “nearest neighbor” technique that compromised Wi-Fi networks by exploiting proximity. It has also been behind multiple phishing and RAT distribution campaigns involving Signal’s device-linking feature.
CERT-UA advises government and enterprise defenders to monitor traffic linked to:
api.icedrive.netapp.koofr.net
Signal Caught in the Middle
Though Signal has been instrumental in recent campaigns, platform security remains intact. Ukrainian officials previously voiced frustration at Signal’s refusal to collaborate in blocking Russian operations, but Signal president Meredith Whittaker clarified:
“The platform has never shared communication data with Ukraine or any other government.”
Still, Signal’s association with recent attacks highlights how trusted apps can be abused for malware delivery, particularly in high-risk geopolitical environments.
Looking for a trusted recovery solution?
Defend your organization with StoneFly DR365—an air-gapped, immutable backup and recovery appliance trusted by enterprises to ensure zero data loss even in the event of complex cyberattacks.