Disneyland Paris Data Allegedly Leaked by Anubis Ransomware Group
The Anubis ransomware gang has claimed responsibility for what it calls “the largest data leak in the history of Disneyland Park,” asserting it holds 64GB of files tied to Disneyland Paris. The announcement appeared on Anubis’ data leak site on June 20, 2025, where a countdown timer indicates the data may be publicly released within days.
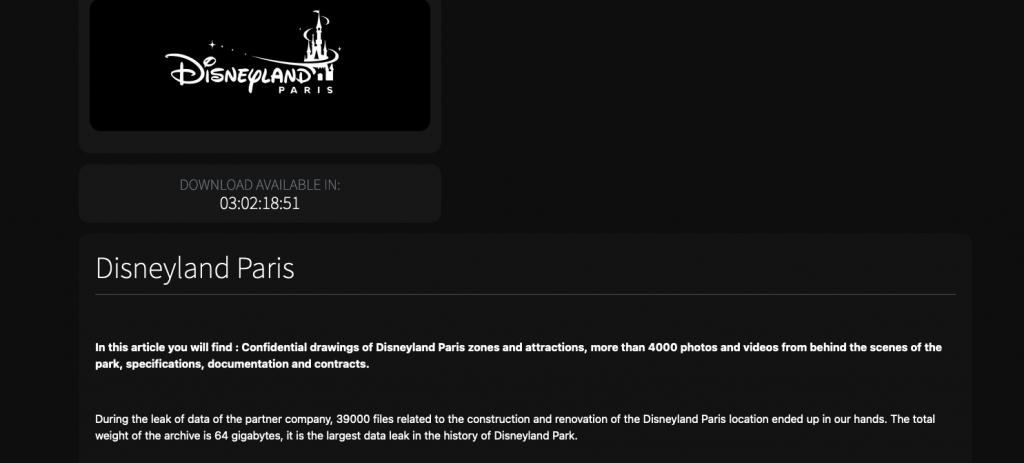
Whether the data was acquired via a direct breach of Disneyland Paris or through a third-party partner remains unconfirmed. Anubis themselves stated:
“During the leak of data of the partner company, 39,000 files related to the construction and renovation of the Disneyland Paris location ended up in our hands.”
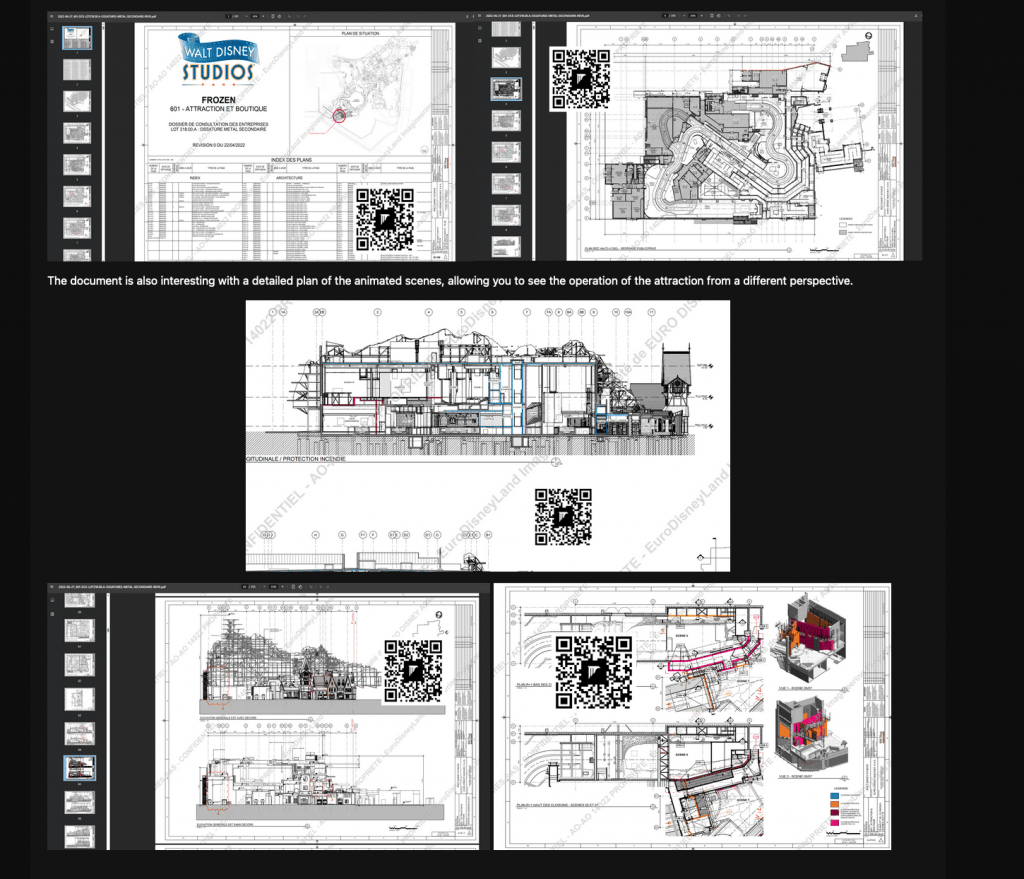
So far, the preview data samples appear to include non-sensitive materials—primarily engineering plans, drawings, and internal photographs. Anubis claims the leak contains over 4,000 behind-the-scenes photos and videos, documents it alleges may be of interest to Disneyland’s competitors.
Editorial Oddities and the Streisand Effect
In a peculiar twist, Anubis’ blog post references its own “editorial staff,” a claim met with skepticism by analysts. Cybernews responded to the unusual tone of the post with a degree of irony, particularly in light of Anubis’ self-description and public messaging style.
Anubis also stated:
“Disneyland Paris strictly monitors media leaks and removes all such photos from the internet. Thus, they unintentionally caused the Barbra Streisand effect.”
The so-called Streisand effect refers to situations where attempts to suppress information inadvertently draw more attention to it.
As of now, Disneyland Paris has not issued an official statement regarding the breach. Cybernews has reached out to their press office and is awaiting a response.
Who Is the Anubis Ransomware Group?
Anubis is a relatively new ransomware group, believed to have emerged in December 2024. Despite their recent appearance, they have established a sophisticated operation blending traditional cyber extortion with a startup-like approach to monetization.
Key features of the group include:
- Double extortion tactics: Encrypting files and threatening public leaks.
- Ransomware-as-a-Service (RaaS): Offering tools and infrastructure to affiliates.
- Access brokering: Selling or sharing access to breached networks.
The group operates across multiple channels, including a presence on X (formerly Twitter), and has become increasingly vocal about its data leaks.