What is Kernel-mode Hardware-enforced Stack Protection
Kernel-mode Hardware-enforced Stack Protection is a security feature introduced in Windows 11 designed to block memory-based attacks, including return-oriented programming (ROP) and stack buffer overflows. It leverages hardware-enforced shadow stacks (available via Intel’s Control-flow Enforcement Technology, or CET) to secure critical system components running in kernel mode.
This feature is part of Microsoft’s ongoing efforts to harden the Windows kernel and protect devices against increasingly sophisticated exploit techniques.
Why Should You Enable Kernel-Mode Hardware-Enforced Stack Protection
Enabling this feature can:
- Defend against memory corruption and control-flow hijacking attacks
- Help secure critical kernel-mode drivers and processes
- Leverage hardware-level protections like Intel CET
- Improve your organization’s overall endpoint security posture
This is especially important for IT teams, security professionals, and developers who manage or deploy Windows environments in enterprise or production systems.
Requirements & Prerequisites
Before proceeding, make sure your system meets the following:
| Requirement | Details |
|---|---|
| OS | Windows 11 (Build 22H2 or later) |
| Processor Support | Intel 11th Gen+ or AMD Zen 3+ CPUs with CET/Shadow Stack support |
| Drivers | Compatible with Kernel-mode Stack Protection (some drivers may block it) |
| System Protection Features | Core Isolation & Virtualization-based Security (VBS) enabled |
Step-by-Step: How to Enable Kernel-Mode Hardware-Enforced Stack Protection
1. Open Windows Security Settings
- Press
Startand search for Windows Security - Click on Device Security
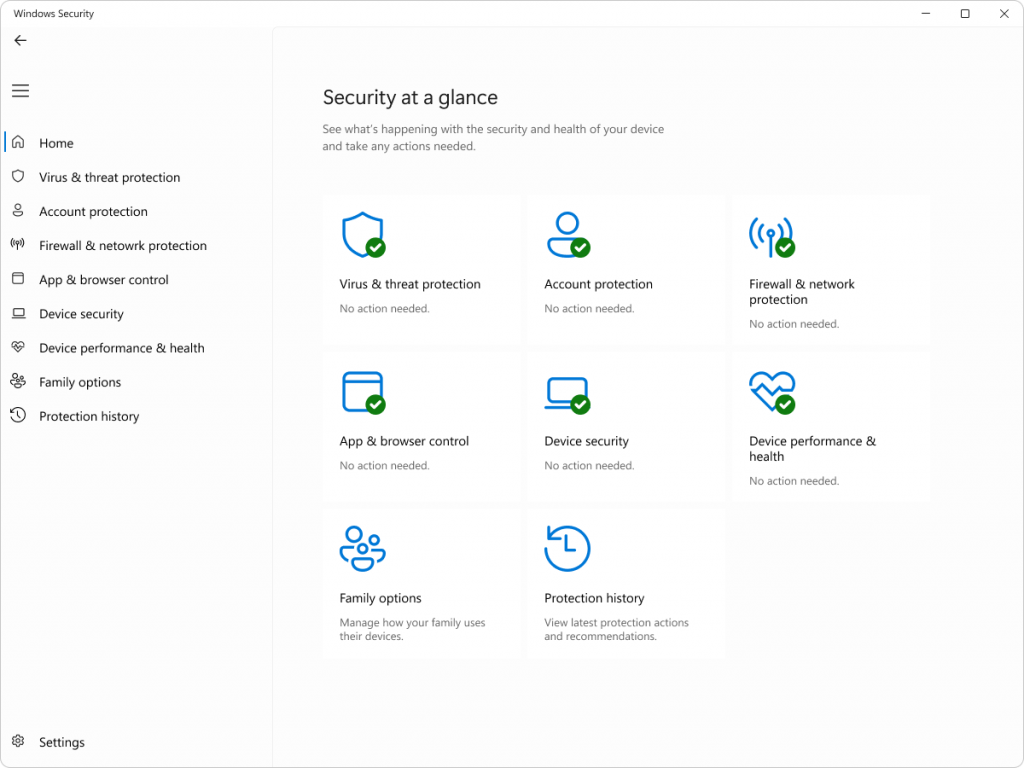
2. Navigate to Core Isolation Settings
- Under “Core Isolation,” click on Core isolation details
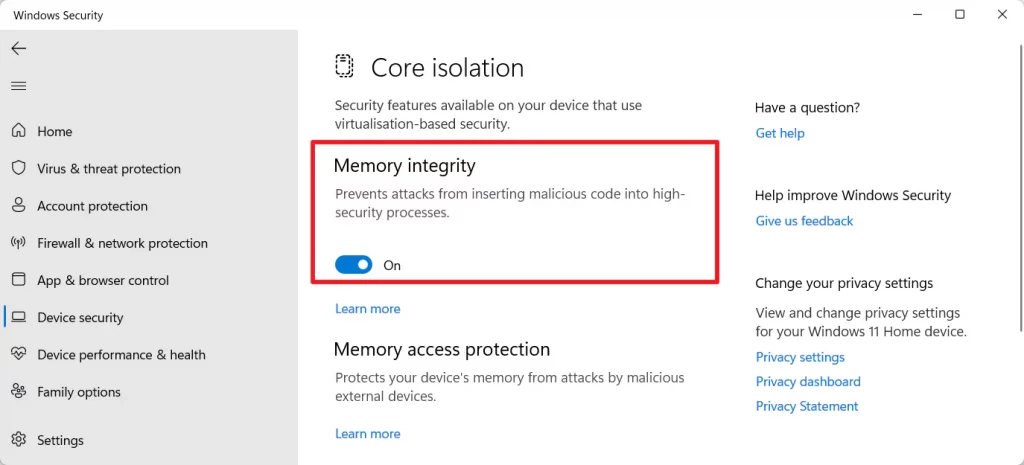
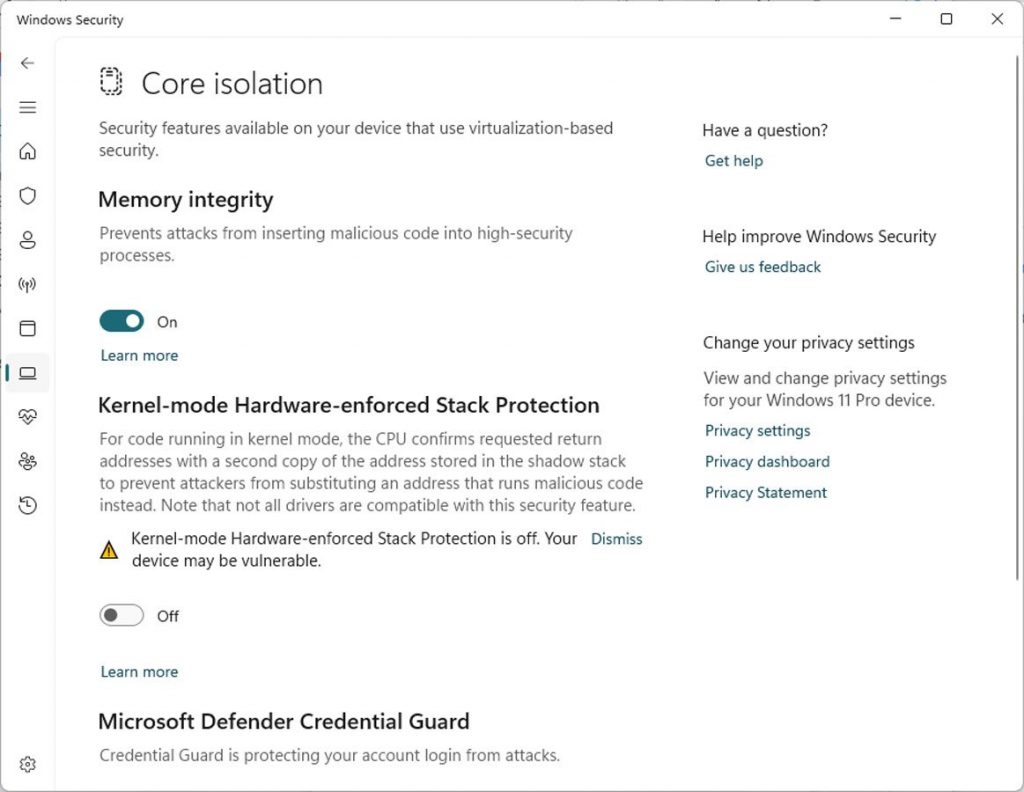
3. Toggle On Stack Protection
- Locate the Kernel-mode Hardware-enforced Stack Protection option
- Switch the toggle to On
4. Restart Your Computer
To apply the changes, you’ll need to restart your device. After reboot, the protection will be enforced for compatible kernel-mode components.
Troubleshooting & Compatibility Notes
- If the feature is grayed out or unavailable, your CPU may not support shadow stack (CET).
- Some legacy or incompatible drivers can block the toggle. Use tools like Microsoft’s Compatibility Analyzer or update/remove outdated drivers.
- Enterprise admins can verify stack protection enablement using Group Policy or PowerShell.
PowerShell Command to Verify Status
Open PowerShell as Administrator and run:
Get-CimInstance -ClassName Win32_DeviceGuardLook for:
KernelModeHardwareEnforcedStackProtection=1(Enabled)
Pro Tips for Enterprises
- Consider auditing drivers across all devices before a fleet-wide enablement.
- Pair Stack Protection with Memory Integrity, Core Isolation, and Credential Guard for defense-in-depth.
- Use Group Policy for large-scale deployment:
Computer Configuration > Administrative Templates > System > Device Guard > Turn On Virtualization Based Security
Final Thoughts
Kernel-mode Hardware-enforced Stack Protection represents a significant step toward securing Windows 11 systems at the hardware level. By enabling this feature, users and organizations can block a wide class of memory corruption exploits that have historically plagued Windows environments.
If you’re running a compatible system, enabling it is highly recommended—not only as a best practice but as a proactive defense against emerging threats.









