A new Android malware that poses as an antivirus tool “from” Russia’s Federal Security Service (FSB) is being used to target executives at Russian companies. In a report by Russian mobile security firm Dr. Web, researchers track the spyware as Android.Backdoor.916.origin and say it does not match known malware families. Since its initial discovery in January 2025, analysts have observed multiple subsequent versions, indicating ongoing development and active targeting.
Dr. Web’s analysis points to distribution lures, infection methods, and an interface that is Russian-only, suggesting the operation was designed for domestic use against Russian businesses. Branding attempts include an app named “GuardCB” that impersonates the Central Bank of the Russian Federation and variants labeled “SECURITY_FSB” and “ФСБ” (FSB), which attempt to pass as official security software.
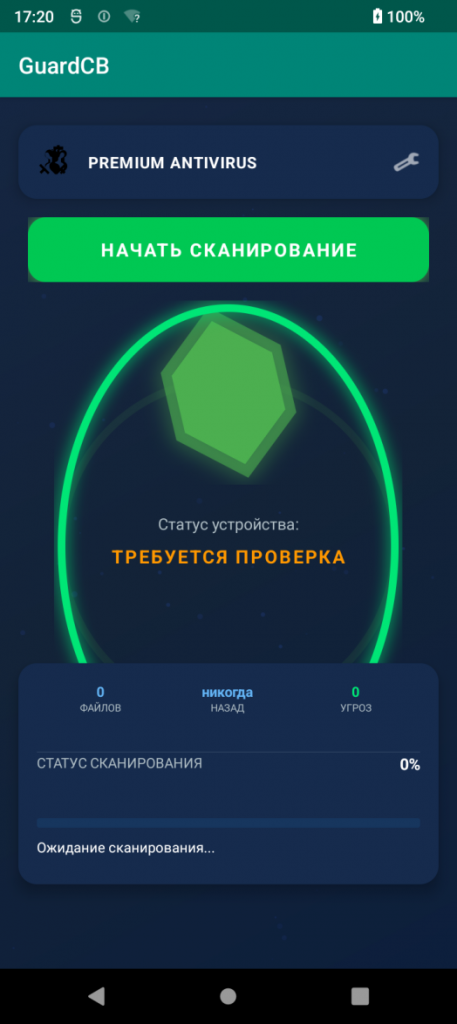
Fake AV scan on the app
Source: Dr. Web
“At the same time, its interface provides only one language — Russian. That is, the malicious program is entirely focused on Russian users,” reports Dr. Web.
“This is confirmed by other detected modifications with file names such as ‘SECURITY_FSB’, ‘FSB’ and others, which cybercriminals are trying to pass off as security programs allegedly related to Russian law enforcement agencies.”
How the Fake Antivirus Infects Android Devices
The malware is presented to victims as a legitimate antivirus tool, but it lacks real security features. Instead, it mimics a working scanner to avoid removal:
- When the user taps Scan, the app runs a simulation that returns fake positive results about 30% of the time.
- The number of supposed detections is randomized between one and three, reinforcing the illusion of real analysis.
Upon installation, the app immediately requests broad, high-risk permissions and launches background services that connect to command and control (C2) infrastructure for operator instructions.
Capabilities Observed in Android.Backdoor.916.origin
Researchers say the spyware includes a wide set of surveillance and data theft features:
- Audio and Video Surveillance: Activate the microphone, camera, and screen streaming to monitor conversations and surroundings.
- Keylogging and Input Capture: Log user input and capture messenger or browser content, including Telegram, WhatsApp, Gmail, Chrome, and Yandex apps.
- Data Exfiltration: Exfiltrate SMS, contacts, call history, geo-location, and stored images.
- Remote Control: Execute shell commands, maintain persistence, and enable self-protection to resist removal.
Risky Permissions Requested on Installation
To enable these functions, the app asks users to grant extensive access:
- Geo-location
- SMS and media files
- Camera and audio recording
- Accessibility Service
- Run in the background at all times
These permissions let the spyware watch activity, read content, and stay active without user interaction.
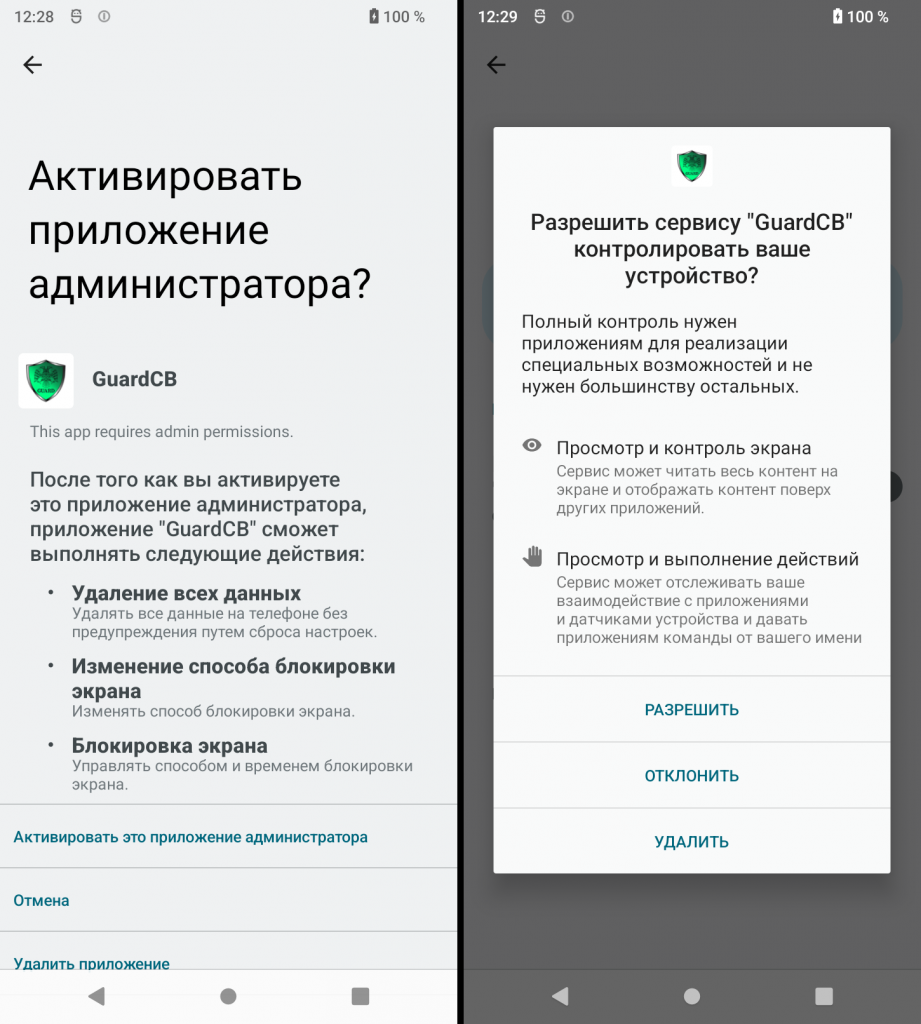
Permission to delete all data and change lock screen (left) and Accessibility Settings (right)
Source: Dr. Web
Branding Lures Impersonate Trusted Russian Institutions
Dr. Web observed two main branding lines to increase trust:
- “GuardCB”: Impersonates the Central Bank of the Russian Federation.
- “SECURITY_FSB” / “ФСБ”: Attempts to impersonate software tied to the FSB.
The consistent Russian-language interface and domestic branding support the view that the malware is aimed at Russian businesses and their executives, not broader global audiences.
Command and Control, Hosting Rotation, and Resilience
After installation, the app starts multiple services and connects to a C2 server to receive commands such as data exfiltration, device surveillance, and command execution. Analysts also found logic that would allow the malware to switch between up to 15 hosting providers. While this rotation feature is not currently active, its presence indicates a design for resilience if takedowns occur.
Fake Antivirus Behavior Designed To Resist Removal
The app’s mock scanner is central to its deception. By returning occasional fake detections, it convinces the victim that the tool is doing real work. The pseudo-results serve two goals:
- Create credibility as a protective product.
- Discourage uninstall, since users believe the app shields them from threats.
The interface and flow mirror real antivirus tools, helping the backdoor remain on devices long enough to collect meaningful data.
Timeline, Versions, and Ongoing Development
- Initial discovery: January 2025
- Multiple versions sampled: indicates active development and iterative changes
- Target profile: Executives of Russian businesses based on lures, permissions, language, and branding
The evolution across samples suggests the operators are maintaining and improving the codebase to expand surveillance and durability on compromised devices.
What Dr. Web Reported About Targeting and Language
Dr. Web assessed the audience as Russian users due to the single-language interface and the institutional impersonation used in branding. The security firm also noted no overlap with known Android malware families, implying either a new codebase or substantial rework of existing components.
“Its interface provides only one language — Russian… the malicious program is entirely focused on Russian users,” the researchers wrote.
Indicators of Compromise and Research Artifacts
Dr. Web shared indicators of compromise (IOCs) for Android.Backdoor.916.origin in a public GitHub repository. The listing includes sample hashes, infrastructure, and other technical markers to aid detection and response. (No links are included here.)
Why This Campaign Matters for Enterprises
The combination of fake antivirus branding, heavy permission abuse, accessibility misuse, and C2-driven surveillance marks a high-risk mobile threat. With a focus on executives, the spyware aims at users who handle sensitive corporate data, financial communications, and privileged messaging channels. The Russian-only presentation and institutional lures further suggest tailored targeting within Russia’s business community.










