Microsoft Threat Intelligence recently disclosed a new variant of the XCSSET macOS malware family that has appeared in limited, targeted attacks against developers who use Xcode. According to Microsoft, the variant was observed during routine hunting and includes new capabilities for browser targeting, clipboard hijacking, and stealth.
XCSSET’s infection chain has an unusual developer-focused propagation mechanism: the malware searches for local Xcode projects and injects malicious code so that the payload executes when the project is built. Microsoft notes that the campaign “banks on project files being shared among developers building Apple or macOS-related applications,” which increases supply-chain risk for teams that regularly exchange project files.
“The XCSSET malware is designed to infect Xcode projects, typically used by software developers, and run while an Xcode project is being built. We assess that this mode of infection and propagation banks on project files being shared among developers building Apple or macOS-related applications.”
Microsoft reports the new variant adds or updates these capabilities: installation of a modified build of HackBrowserData to harvest Firefox artifacts, a clipboard-monitoring module that looks for cryptocurrency addresses and substitutes attacker addresses, LaunchDaemon-based persistence that executes payloads from hidden locations, and a fake System Settings.app drop in /tmp to obscure activity.
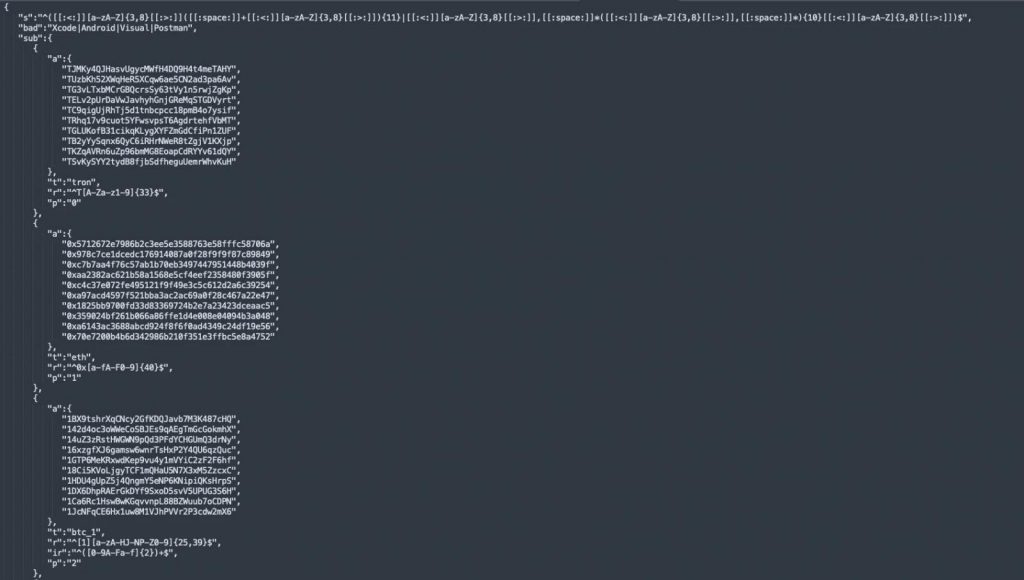
Attacker’s cryptocurrency addresses used with the Clipboard hijacker
Source: Microsoft
Technical Breakdown, Detection, and Comparative Incidents
How the XCSSET macOS Malware Variant Works (Attack Chain and Tooling)
- Initial delivery / spread: weaponized Xcode projects (malicious files or modified libraries) are shared via repos, zip files, or developer collaboration channels. When an infected project is built, the malicious build phase runs.
- Browser harvesting: the malware includes or downloads a modified version of [HackBrowserData] to decrypt and export data (cookies, saved logins, autofill) from multiple browsers, now explicitly extended to target Firefox.
- Clipboard hijacking: a watcher monitors the macOS pasteboard for regex patterns that match cryptocurrency addresses and replaces them with attacker-controlled addresses at the moment of paste.
- Persistence and obfuscation: the variant creates LaunchDaemon entries that point to a
~/.rootpayload and drops a decoySystem Settings.appunder/tmp, attempting to blend with legitimate system activity. - Secondary actions: credential and key theft, notes and file exfiltration, and possible deployment of additional backdoors.
Practical Detection and Hunting Steps (Commands and Signatures)
Below are actionable checks developers and security teams can run immediately on macOS dev machines and build servers. Run these from an admin shell or under an endpoint security playbook.
- Find suspicious Xcode build phases or injected scripts in project directories:
# From the repo root, search for suspicious shell script phases or added files
grep -R --line-number --exclude-dir=.gitE "runScript" .
grep -R --line-number --exclude-dir=.gitE "shellScript" .
# Search for unexpected binary drops or unusual pbxproj additions
find . -type f -name "*.pbxproj" -exec grep -n "script" {} +
- Check LaunchDaemons and unexpected startup items:
# List system LaunchDaemons and binaries
ls /Library/LaunchDaemons /Library/LaunchAgents ~/Library/LaunchAgents /System/Library/LaunchDaemons
# Inspect suspicious plist entries for odd ProgramArguments or executables
plutil -p /Library/LaunchDaemons/com.example.suspicious.plist
- Detect clipboard-monitoring or replacement behavior (heuristic checks):
# List processes with Input Monitoring / Accessibility privileges (requires admin)
tccutil reset Accessibility
# Or enumerate apps that have been granted permissions via system preferences (manual review recommended)
- Identify unusual browser-scraping helpers or foreign binaries:
# Locate binaries that are recent or not signed by Apple
sudo find / -type f -perm -111 -mtime -7 2>/dev/null | xargs -I{} sh -c 'codesign -v {} 2>&1 || echo "Unsigned: {}"'
- Network telemetry: watch for processes making DNS or HTTPS calls to unfamiliar hosts immediately after Xcode builds:
# Live TCP connections (macOS)
sudo lsof -iTCP -sTCP:ESTABLISHED -n -P
# Or use packet capture to identify C2 patterns (requires security tools)
Comparative Incidents Involving XCSSET Malware
XCSSET is not new. Microsoft previously documented updated obfuscation and persistence techniques earlier in 2025, and the family has cycled through variants since its initial discovery. The clipboard hijacking pattern echoes prior macOS malware that intercepts payment flows; similarly, supply-chain-style infections (via developer tools or build systems) recall other incidents where development artifacts were weaponized to spread malware. Security outlets and vendors are already advising developers to treat shared Xcode assets as potentially hostile.
Risk Implications and Remediation Advice
Risk Profile for Developers and Organizations
- Software Supply-Chain Risk: infected Xcode projects can propagate silently through repositories, CI artifacts and zipped project bundles, potentially infecting downstream users and customers.
- Credential and Session Theft: browser data collection (cookies, saved credentials) can enable account takeovers and session hijacking, intensifying breach impact.
- Direct Financial Loss: clipboard hijacking can lead to irreversible cryptocurrency theft if users paste addresses during transfers.
- Operational Exposure: persistence on developer machines or build servers can be used to sign or distribute tainted builds at scale.
Immediate Remediation Steps (Developer / DevOps)
- Inspect Any Received Xcode Projects Before Building: manually review build phases in Xcode and scan
*.pbxprojfiles for unexpected script phases or references to obfuscated binaries. Use thegrepchecks above as automatable pre-build hooks. - Treat Third-Party Project Files as Untrusted: prefer downloading dependencies from canonical package managers and vet any external project archives before importing. Maintain a strict pull-request review policy that checks for build-phase changes.
- Harden Build Infrastructure: run builds inside ephemeral CI runners or hardened containers that reset state between jobs; avoid allowing builds to run on long-lived developer workstations with access to secrets.
- Patch and Update: keep macOS, Xcode and browsers current—Apple’s security updates page provides the latest fixes and guidance: [Apple Security Releases].
- Monitor for Indicators of Compromise: add alerts for new LaunchDaemon entries, unsigned binaries created under developer directories, and unusual outbound connections from build hosts.
- Protect Crypto Workflows: use hardware wallets or dedicated, air-gapped signing devices for high-value transactions to defeat clipboard-replacement attacks.
Long-Term Controls and Policy Recommendations
- Enforce least privilege for developer machines: separate keys, tokens and credentials between dev, test and CI environments.
- Implement pre-commit and pre-build scanning to flag added shell scripts or binary blobs in pull requests.
- Use signed, reproducible builds and artifact signing so downstream consumers can verify integrity.
- Educate developers on the risks of opening shared projects from untrusted sources and on verifying build phases in Xcode.









