Security researchers have recently detected attacks targeting Red Hat and Ubuntu systems by a Linux version of the DinodasRAT malware, also known as XDealer.
DinodasRAT Malware Details
According to a recent report by Kaspersky, researchers have discovered that the Linux version of DinodasRAT employs certain techniques upon execution.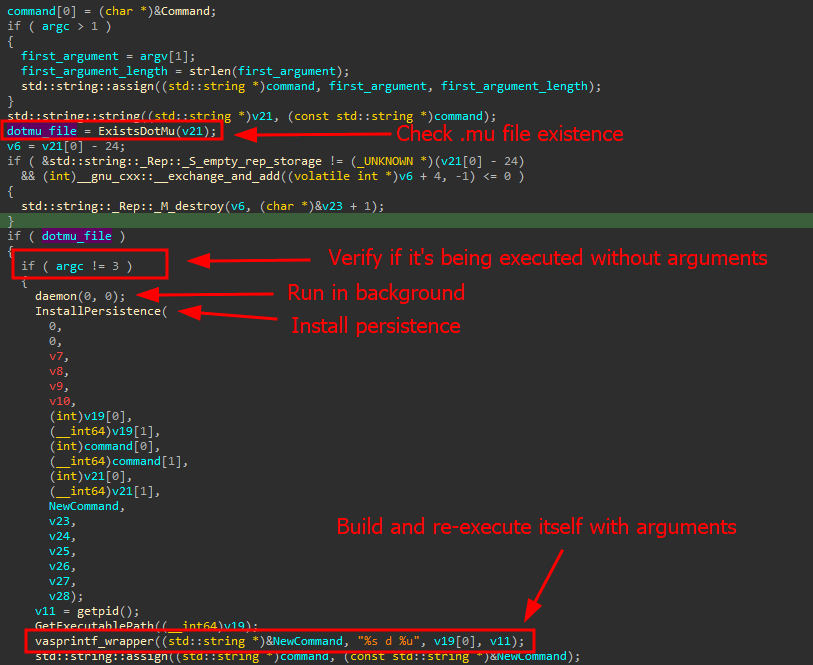
Malware’s Execution Logic
Source: Kaspersky
Firstly, it creates a hidden file in the same directory as its binary, serving as a mutex to ensure that only one instance runs on the infected device.
The malware then establishes persistence on the computer using either SystemV or SystemD startup scripts.
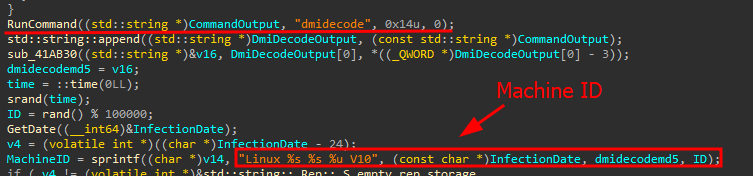
To evade detection, the malware executes once more while the parent process waits. Furthermore, the infected machine is labeled with infection, hardware, and system details, and the collected data is sent to the command and control (C2) server for managing victim hosts.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
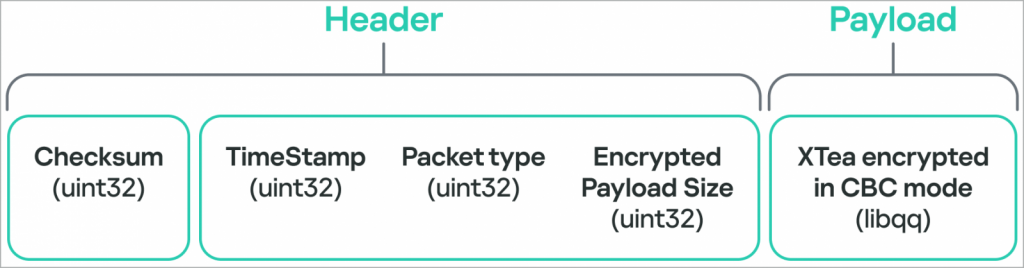
Dinodas Malware Network Packet Structure
Source: Kaspersky
DinodasRAT malware possesses a range of capabilities specifically designed for monitoring, controlling, and extracting data from compromised systems. Its key functionalities include:
- Monitoring and harvesting data related to user activities, system configurations, and running processes.
- Executing commands received from the command and control (C2) server, which may involve actions related to files and directories, execution of shell commands, and updating the C2 address.
- Enumerating, starting, stopping, and managing processes and services on the infected system.
- Providing the attackers with a remote shell for direct command execution or file manipulation in separate threads.
- Proxying C2 communications through remote servers, enhancing stealth and obfuscation.
- Downloading new iterations of the malware, potentially incorporating enhancements and additional capabilities.
- Uninstalling itself and thoroughly erasing all traces of its previous activities from the compromised system.
According to the researchers, DinodasRAT malware grants the attacker full control over compromised systems. They emphasize that the threat actor primarily utilizes the malware to gain initial access to the target and subsequently maintain that access through Linux servers.
“The backdoor is fully functional, granting the operator complete control over the infected machine, enabling data exfiltration and espionage,”
Kaspersky says.
Kaspersky’s report does not disclose specific information about the initial method of infection. However, it highlights that starting from October 2023, the DinodasRAT malware has been observed targeting victims in China, Taiwan, Turkey, and Uzbekistan.