What are 1-day Vulnerabilities?
1-day vulnerabilities are publicly disclosed flaws for which a patch has already been released. Threat actors who wish to exploit these vulnerabilities must act swiftly before their intended targets can apply security updates.
Typically, exploits for 1-day vulnerabilities are not immediately available upon disclosure. However, in some cases, it is relatively easy to determine how to take advantage of the vulnerability.
Additionally, by reverse-engineering the patch, the underlying issue and its exploitation methods can be discovered.
Magnet Goblin Hackers Are Capable Enough to Exploit 1-day Vulnerabilities Within a Day, Says Checkpoint
According to Check Point analysts who have identified Magnet Goblin, these threat actors are known for their swift exploitation of newly disclosed vulnerabilities. In some cases, they exploit flaws within a day of a Proof of Concept (PoC) exploit being released.
The hackers target various devices and services, including Ivanti Connect Secure (CVE-2024-21887, CVE-2023-46805, CVE-2024-21888, CVE-2024-21893), Apache ActiveMQ, ConnectWise ScreenConnect, Qlik Sense (CVE-2023-41266, CVE-2023-41265, CVE-2023-48365), and Magento (CVE-2022-24086).
Magnet Goblin leverages these vulnerabilities to infect servers with custom malware, specifically NerbianRAT, MiniNerbian, and a customized version of the WARPWIRE JavaScript stealer.
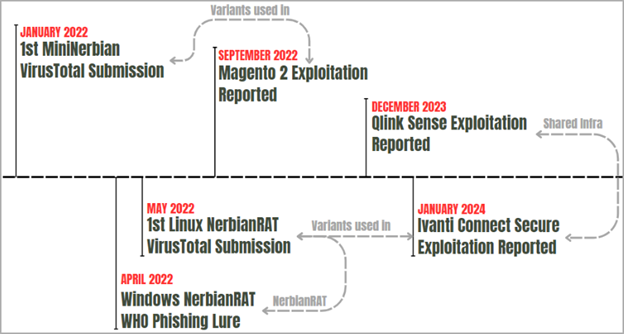
Timeline of Magnet Goblin activities
Source: Check Point
Custom Linux Malware ‘NerbianRAT’ Modus Operandi
According to the latest report from Check Point, while NerbianRAT for Windows has been known since 2022, Magnet Goblin has been circulating a Linux variant of the malware since May 2022. Despite being sloppily compiled, this Linux variant remains effective.
Upon initial execution, the malware carries out several preliminary actions. These include collecting system information such as the current time, username, and machine name.
NerbianRAT generates a unique bot ID, sets a hardcoded IP address as both the primary and secondary host, establishes the working directory, and loads a public RSA key for encrypting network communication using AES.
Subsequently, NerbianRAT loads its configuration, which specifies the activity times (worktime), time intervals for communication with the command and control (C2) server, and other relevant parameters.
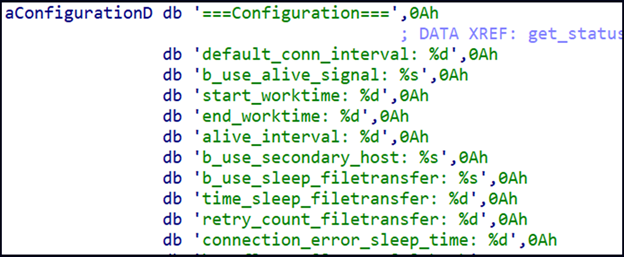
Configuration parameters
Source: Check Point
Upon receiving instructions from the command and control (C2) server, the custom Linux malware is capable of executing various actions on the infected system. These actions, which may be sent in any order, include:
- Immediate execution of a Linux command
- Sending the command result to the server, while also cleaning the associated file and terminating any ongoing commands
- Updating a specific configuration variable
- Modifying the interval for establishing connections
- Requesting additional actions from the server
- Refreshing the command buffer for C2 execution commands
- Executing a Linux command in a new thread
- Adjusting and saving worktime settings
- Returning idle timings, configuration details, or command results
- Taking no action, remaining idle
Magnet Goblin Hackers Also Use MiniNerbian, a Mini Version of the NerbianRAT
MiniNerbian, a streamlined variant of NerbianRAT, focuses on command execution and supports the following actions:
- Executing commands from the C2 and returning the results
- Updating the activity schedule, either for the entire day or specific hours
- Updating the configuration settings
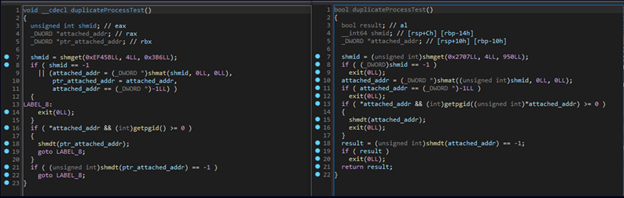
Similarities Between Codes of NerbianRAT and MiniNerbian
Source: Check Point
Unlike the more intricate NerbianRAT, MiniNerbian communicates with the C2 server through HTTP, distinguishing it from the former’s employment of raw TCP sockets for communication.
It is possible that Magnet Goblin hackers use MiniNerbian as a redundant or stealthier backdoor in certain cases. According to Check Point, identifying specific threats like the attacks carried out by Magnet Goblin amidst the vast amount of 1-day exploitation data can be challenging.
This allows such hacker groups to camouflage themselves amidst the chaos that often follows the disclosure of vulnerabilities.
Taking prompt action to apply patches is crucial in countering 1-day exploitation. Furthermore, implementing additional measures like network segmentation, endpoint protection, and multi-factor authentication can help mitigate the potential impact of breaches.










