Hackers are using a new phishing kit called CryptoChameleon in advanced Okta phishing attacks. The phishing kit is currently being used to target employees of the Federal Communications Commission (FCC).
The attackers employ a sophisticated approach, combining phishing and social engineering attacks. They use various methods like email, SMS, and voice phishing to trick victims into providing sensitive information on the fake pages. This information includes usernames, passwords, and in some cases, even photo IDs.
The attackers are using carefully crafted single sign-on (SSO) pages that imitate Okta’s original pages, making them difficult to distinguish.
This same campaign also targets individuals and employees of cryptocurrency platforms like Binance, Coinbase, Kraken, and Gemini. The phishing pages used in this campaign impersonate popular platforms such as Okta, Gmail, iCloud, Outlook, Twitter, Yahoo, and AOL.
Okta Phishing Attacks Are Categorized by Multi-Pronged Social Engineering Attacks
The threat actors behind this attack employ a multi-pronged social engineering attack strategy. They begin by registering domains that are extremely similar to those of legitimate organizations.
For example, in the case of the FCC, they created a domain called “fcc-okta[.]com,” which differs from the genuine Okta single-sign-on page by just one character.
To deceive their targets, the attackers utilize various communication channels such as phone calls, emails, or text messages. They masquerade as customer support representatives and trick the targets into believing that their accounts need to be recovered. They then direct the targets to the phishing site, furthering their malicious intent.
In the case of Coinbase, the attackers sent text messages pretending to be alerts regarding suspicious login activity. These messages directed users to phishing pages, as evidenced by the example provided.
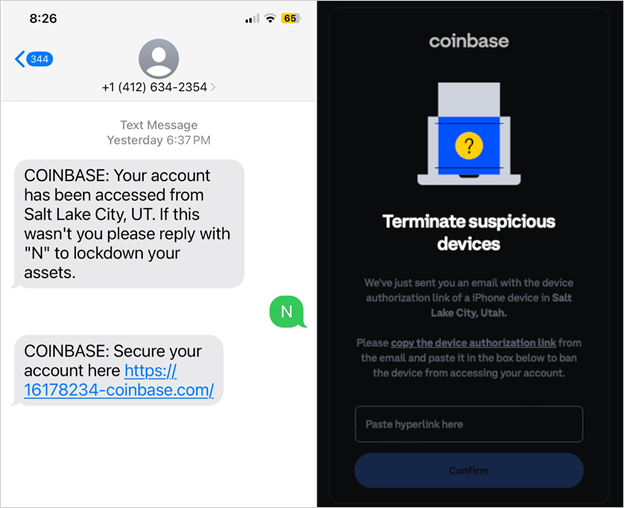
SMS Phishing on the Left and an Identical Phishing Page on the Right
Source: Lookout
When victims access the phishing site, they are prompted to solve a CAPTCHA challenge.
- Firstly, it helps filter out automated bots from accessing the site.
- Secondly, it adds an element of legitimacy to the phishing process, potentially further deceiving the victims.
Once users successfully complete the CAPTCHA challenge, they encounter a phishing page that is an exact replica of Okta’s legitimate login site. The OKTA phishing kit utilized by the cybercriminals allows them to engage with victims in real-time.
This enables them to carry out tactics such as requesting additional authentication, particularly in cases where multi-factor authentication (MFA) codes are needed to gain control over the target’s account.
The phishing attack is then facilitated through a central panel that grants the attackers the ability to personalize the phishing page according to the victim’s specific phone number digits. This customization creates the illusion of legitimacy when the attackers request SMS tokens from the victims.
Once the phishing process is complete, the victim may be redirected either to the legitimate sign-in page of the targeted platform or to a fraudulent portal claiming that their account is under review. These destinations are strategically chosen to minimize suspicion on the victim’s part and provide the attackers with additional time to exploit the stolen information.
In Depth Analysis of OKTA Phishing Attack Campaign Reveals Concerning Details
Further investigation by Lookout revealed more information about the targets within the cryptocurrency industry. By analyzing the phishing kit and identifying relevant lures, the researchers gained insight into the additional entities being targeted.
Additionally, Lookout’s researchers were able to obtain temporary access to the attacker’s backend logs. This access confirmed that the campaign successfully resulted in compromising high-value targets.
“The sites seem to have successfully phished more than 100 victims, based on the logs observed,”
“Many of the sites are still active and continue to phish for more credentials each hour.”
Explains Lookout.
During late 2023, the threat actors predominantly utilized Hostwinds and Hostinger as hosting providers for their phishing pages. However, they later transitioned to RetnNet, based in Russia. This change in hosting providers potentially allows for a more prolonged operational period for illicit websites.
Unfortunately, Lookout was unable to ascertain whether the CryptoChameleon phishing kit is exclusively used by a single threat actor or if it is rented out to multiple groups.
Irrespective of the specific individuals or groups responsible for the CryptoChameleon phishing kit, its sophisticated nature, targeted approach, and effective communication methods highlight the significant impact it can have on the organizations it targets.
For detailed information on indicators of compromise, including command and control servers and phishing sites associated with the campaign, please refer to Lookout’s article. The list can be found at the bottom of the article and will provide further insights for those interested.










