Attackers are manipulating search results and lookalike websites to trick users into downloading trojanized installers that impersonate trusted apps such as Signal, WhatsApp and Chrome. FortiGuard Labs researchers say the campaign bundles legitimate application files with hidden malware, then gains administrator privileges on infected machines to run extended surveillance and data-capture routines.
How Attackers Weaponize Search Engines and Lookalike Domains
FortiGuard’s analysis shows threat actors are using SEO plugins, registered lookalike domains and carefzully tuned content to push malicious sites into high search rankings. Victims who click top results are routed to pages that present authentic-looking download buttons and installer packages. The installers include the real app alongside a malicious payload, making the infection hard to spot during installation.
The technique—commonly called SEO poisoning—lets attackers reach users without sending phishing emails or opening noisy attack channels. In this campaign, even users who rely on highly ranked search results can be misled by the spoofed domains and polished site copy.
Source: FortiGuard Labs
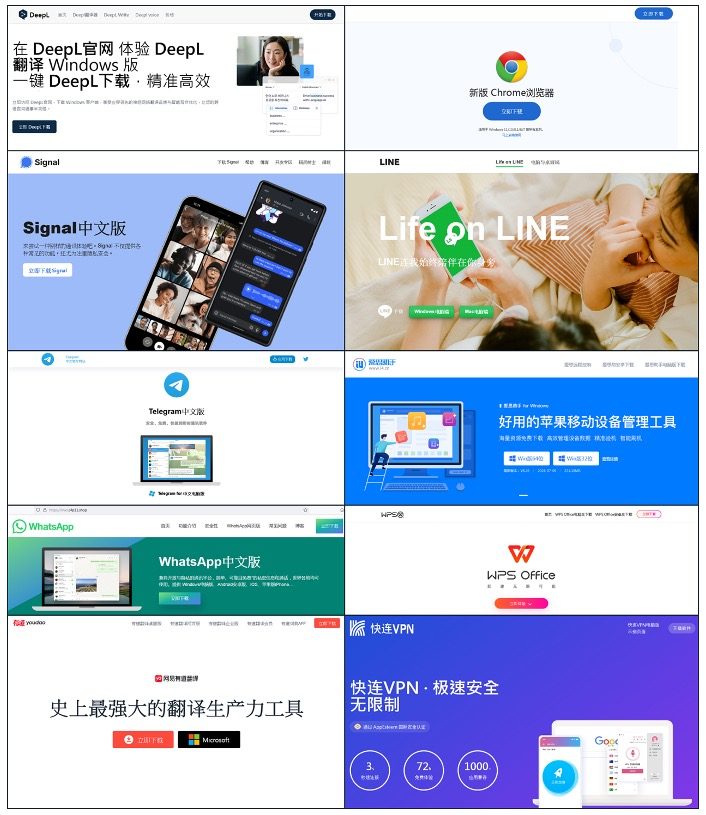
Apps Used as Bait
FortiGuard identified multiple well-known brands and utilities abused as decoys, including:
- Signal
- DeepL
- Chrome
- Telegram
- Line
- A VPN Provider
- WPS Office
Because the installers contain the legitimate binary, users typically see the expected application appear to install correctly while the hidden components deploy in the background.
Malware Capabilities and Installation Flow
Analysis revealed two principal malware families distributed by this scheme: Hiddengh0st and a new Winos variant. The delivery chain follows a consistent pattern:
- Victim downloads and runs the trojanized installer from a spoofed site.
- Installer drops malicious DLLs into hidden directories and escalates privileges to administrator level.
- Malware executes persistence routines and loads plugins for modular functionality.
- Plugins enable extended surveillance and data theft.
Observed capabilities include system and environment enumeration, AV and security-tool discovery, keystroke and clipboard logging, foreground-window and screen capture, and remote plugin loading. FortiGuard also noted plugin indicators suggesting potential interception of Telegram communications. The modular design lets attackers expand the toolkit over time, adding features such as credential theft or remote-control modules.
Target Audience and Regional Focus
FortiGuard reported that the campaign primarily targeted Chinese-speaking users. That regional focus, combined with targeted SEO content and lookalike domains, increases the likelihood of successful deception for intended audiences while avoiding broader detection.
Why This Attack Is Hard To Detect
Because the installer contains both the legitimate application and malicious components, users rarely see obvious red flags. The visible app appears to function normally, which delays discovery and gives attackers time to establish persistence. The use of high-ranking search results and sponsored placements further lends credibility to the fake sites.
FortiGuard summed it up:
“The installers contained both the legitimate application and the malicious payload, making it difficult for users to notice the infection.”
Fits a Broader Pattern of SEO Abuse
The campaign mirrors earlier SEO-poisoning and ad-driven fraud operations tracked by security teams such as Cisco Talos. In past schemes, attackers exploited popular brands and paid search placements to funnel victims to fake vendor pages. Ransomware groups and fraud actors have used similar tactics with AI tools, financial brands, and consumer services to deliver malware or harvest credentials.
Risk Signals for Enterprise
For enterprises, the scheme underscores that supply-chain and third-party risk extends beyond code repositories and app stores. Malicious installers masquerading as legitimate software can bypass casual inspection and reach endpoints through normal user behavior. The behavior profile—privilege escalation, persistence, data capture, and modular plugin loading—matches patterns frequently observed in long-running intrusions.
FortiGuard provided behavioral indicators tied to Hiddengh0st and the Winos variant and traced multiple delivery domains and installer variants. Their report highlights the delivery infrastructure, installer characteristics, and observed post-installation behavior for defenders mapping detection rules and EDR hunting queries.









