Multi-Stage Espionage Campaign Against Diplomatic Missions
A state-sponsored espionage operation has been targeting foreign embassies in South Korea with XenoRAT malware, delivered through malicious GitHub repositories.
According to Trellix researchers, the campaign began in March 2025 and is still active. At least 19 spearphishing attacks have been carried out against high-value diplomatic targets.
While some techniques resemble the playbook of North Korean group Kimsuky (APT43), forensic details also suggest links to China-based operatives.
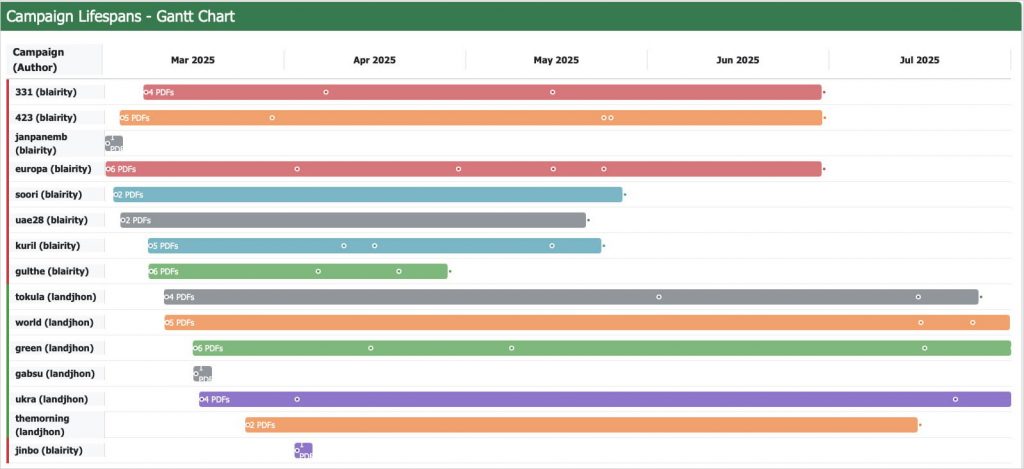
Timeline of individual attacks
Source: Trellix
Attack Timeline and Phishing Lures
The campaign unfolded in three phases, each using different email lures:
- March 2025 – Initial Probing: The first identified email targeted a Central European embassy.
- May 2025 – Diplomatic Targeting: On May 13, a Western European embassy received an email impersonating a senior EU delegation official, referencing a “Political Advisory Meeting” scheduled for the next day.
- June–July 2025 – U.S.–Korea Alliance Themes: The attackers shifted to lures tied to U.S.–Korea military relations.
The lures included fake invitations, official letters, and event notifications. Messages were multilingual—written in Korean, English, French, Arabic, Russian, and Persian—and strategically timed to coincide with real-world diplomatic events.
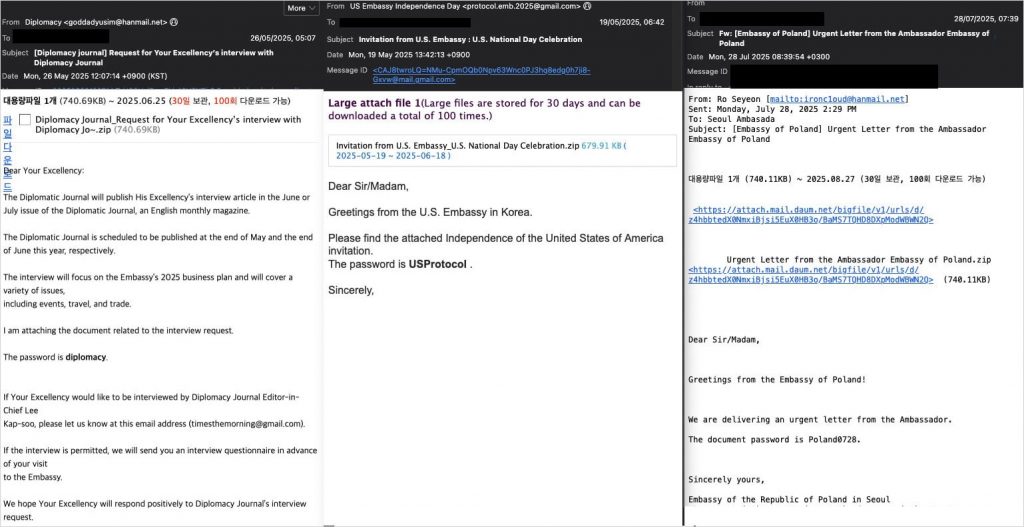
Phishing messages used in the attacks
Source: Trellix
Malware Delivery and Capabilities
All phases used the same delivery method. Password-protected archives (.ZIP) were hosted on platforms like Dropbox, Google Drive, and Daum.
Inside, a .LNK file disguised as a PDF executed obfuscated PowerShell code. This downloaded the XenoRAT payload from GitHub or Dropbox and established persistence via scheduled tasks.
XenoRAT is a sophisticated trojan capable of:
- Logging keystrokes
- Capturing screenshots
- Accessing webcams and microphones
- Conducting file transfers
- Enabling remote shell operations
The malware is loaded directly into memory through reflection and obfuscated with Confuser Core 1.6.0, helping it remain undetected.
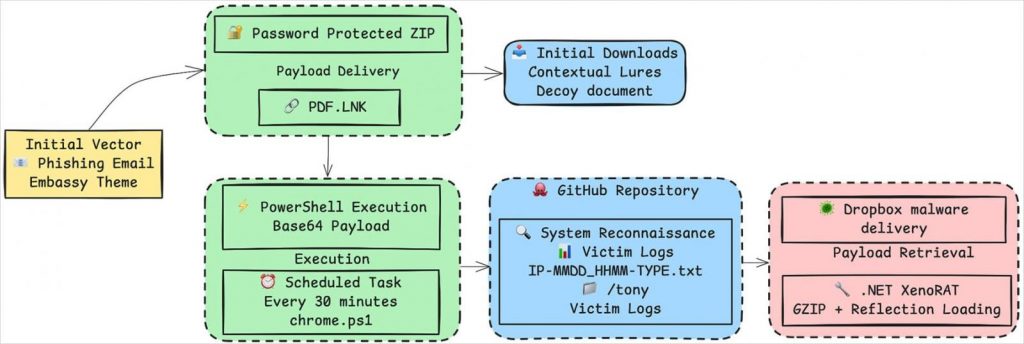
Overview of the infection chain
Source: Trellix
Attribution to North Korean and Chinese Threat Actors
The operation exhibits hallmarks of APT43 (Kimsuky). Indicators include:
- Use of Korean email services
- Abuse of GitHub for command-and-control
- GUIDs and mutex patterns tied to Kimsuky malware families
- IP addresses and domains linked to prior Kimsuky activity
However, Trellix also found evidence pointing toward China-based actors. Time zone analysis aligned with Chinese work hours, and attacker downtime coincided with Chinese national holidays, not North Korean ones.
Trellix ultimately attributed the campaign to APT43 with medium confidence, suggesting possible Chinese involvement or sponsorship.









