AMI MegaRAC Firmware Flaw Actively Exploited in the Wild
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a public warning confirming active exploitation of a critical authentication bypass vulnerability in AMI’s MegaRAC Baseboard Management Controller (BMC) firmware. Tracked as CVE-2024-54085, the flaw allows attackers to take complete control of vulnerable servers with minimal effort and no user interaction.
MegaRAC BMC software enables remote management of server hardware, including rebooting, troubleshooting, or system recovery—critical features for cloud service providers and enterprise data centers. Vendors such as HPE, ASUS, and ASRock rely on this firmware in many of their server products.
Vulnerability Impact: From Remote Control to Physical Damage
Security researchers at Eclypsium, who discovered the flaw, warned that attackers could exploit it to hijack servers remotely and deploy malware or ransomware. Even more concerning, the bug also enables firmware tampering, system bricking, and permanent damage to components like the BIOS or BMC chip.
“Exploitation of this vulnerability allows an attacker to remotely control the compromised server, remotely deploy malware, ransomware, firmware tampering, bricking motherboard components (BMC or potentially BIOS/UEFI), potential server physical damage, and indefinite reboot loops that a victim cannot stop,”
— Eclypsium researchers
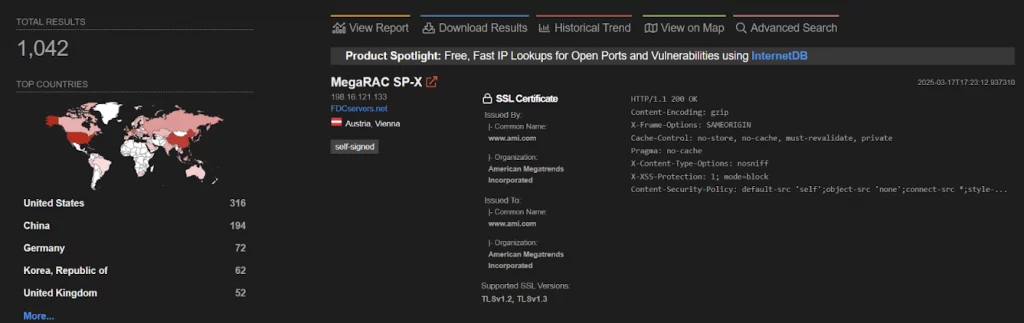
Exposed AMI MegaRAC instances (Eclypsium)
The flaw stems from improper authentication validation and was found while Eclypsium was analyzing fixes for a similar bug disclosed in 2023 (CVE-2023-34329). In March, AMI issued patches, but by then, more than 1,000 servers with exposed MegaRAC instances had already been identified online.
According to Eclypsium, MegaRAC firmware binaries are not encrypted, making exploit development relatively simple. They also noted that although the vulnerability is limited to AMI’s BMC stack, the broader impact is significant because AMI firmware is deeply embedded across the server BIOS supply chain.
Government Agencies on High Alert
Following its verification, CISA added CVE-2024-54085 to its Known Exploited Vulnerabilities Catalog, mandating that Federal Civilian Executive Branch (FCEB) agencies patch their systems no later than July 16, 2024, under Binding Operational Directive 22-01.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,”
— CISA
Though the directive targets federal agencies, CISA strongly urges all private sector defenders and infrastructure operators to prioritize patching due to the severity and ease of exploitation.
A Wake-Up Call for Enterprise Infrastructure Security
The active targeting of remote management firmware like MegaRAC is a clear indicator of threat actors moving beyond software to exploit hardware-level access. As organizations race to harden their environments, this vulnerability reinforces the need for complete resilience—especially in environments managing thousands of endpoints or critical data.
Maintaining operational continuity requires more than patching; it demands a secure, immutable backup and recovery strategy that protects against data loss even when systems are fully compromised.
Looking for a trusted recovery solution?
Defend your organization with StoneFly DR365—an air-gapped, immutable backup and recovery appliance trusted by enterprises to ensure zero data loss even in the event of complex cyberattacks.










